The eMMC and UFS memory chips have an access protected section called the RPMB (Replay Protect Memory Block).
In a UFS chip, the section that performs the RPMB functions is ID: W-LUN 0xC4
This section is intended for storage of information to which direct access is closed.
The picture from the Samsung presentation shows how it works.
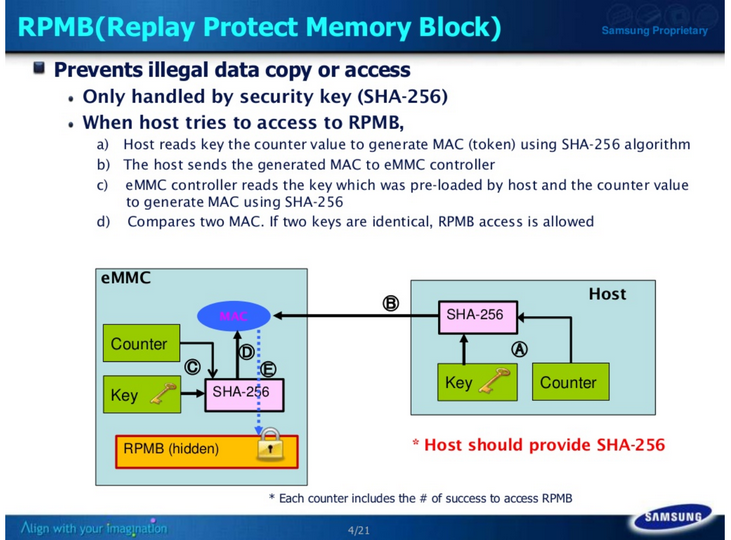 How it works in more detail: If the key (Key) is absent
How it works in more detail: If the key (Key) is absent, then the device (processor) programs the key into the microchip.
The key is generated from the processor SN and the eMMC CID, and thus the key is different for different processors and different eMMCs. Further work occurs in the mode as with the programmed key. The programmed key cannot be changed.
If the key (Key) already exists, then, as a rule, the counter has a value greater than 0.
With a microcircuit that already has a key (16 bytes), the device (processor) can work only through data encoded with a key (Key) and a counter.
Read mode: the device (processor) receives the counter value from the eMMC, requests reading data (in blocks of 256 bytes), receives the data encoded by the counter and key, decrypts it using the stored key and counter value, checks the validity of the data.
Write mode: the device (processor) receives the counter value from the eMMC, encodes the data using a key and a counter (in blocks of 256 bytes) and sends it to the microchip. The chip decrypts them using the stored key and the value of the counter, checks the validity of the data. If the data is valid, the block is written, and the value of the record counter (Counter) is incremented by 1.
Thus, the value of the write counter (Counter) shows how many blocks of 256 bytes (or how many times) were written into the RPMB area.
In order to write to the RPMB section, you need to know the key that is stored in the microchip (eMMC).
In order to read, you can try to apply a certain method of obtaining data. Although it is impossible to guarantee their validity, but experiments conducted by the Z3x Easy JTAG team show that the data read in this way is valid in more than 90% of cases.
In the latest versions of the Z3x EasyJTAG Classic program (3.4.4.0 and above), the output has been added to the log of the status bar of the RPMB area (did it ever write to the data or not).
An example of a line in the program log:
EMMC RPMB is not yet programmed (clear) or NO Error
or
EMMC RPMB is programmed and written 12 times
At the same time, the ability to read RPMB experimentally is available through the choice of the RPMB partition (in the ROM select box).
Important:
1) when the Firmware is written to the eMMC, the internal NAND memory of the eMMC is re-initialized, erasing the key, the counter and the RPMB data
2) it is not possible to remove the key from the RPMB or change the counter other than increasing the counter value by writing data encoded with a valid key.