



  |
 |
|
Welcome to the GSM-Forum forums. You are currently viewing our boards as a guest which gives you limited access to view most discussions and access our other features. Only registered members may post questions, contact other members or search our database of over 8 million posts. Registration is fast, simple and absolutely free so please - Click to REGISTER! If you have any problems with the registration process or your account login, please contact contact us . |
| |||||||
| Register | FAQ | Donate | Forum Rules | Root any Device | ★iPhone Unlock★ | ★ Direct Codes ★ | Direct Unlock Source | Today's Posts | Search |
 |
| | LinkBack | Thread Tools | Display Modes |
| | #7891 (permalink) | |
| Freak Poster     | Quote:
| |
 |
| | #7893 (permalink) |
| No Life Poster      Join Date: Jul 2010 Location: North Africa
Posts: 891
Member: 1350724 Status: Offline Thanks Meter: 188 | REALME C11 FLASH DONE EXE: NckDongle Spreadtrum Module 2.1.2 ACTION: Flash Firmware. Selected firmware: RMX3231-user-native_SHARKL3_R11.pac NV: Default Mode (protect calibration) Device Storage: EMMC Start Detect phone... Phone must be off with battery inside. Long press "VOL -" key while inserting usb cable. For some phones need to Long press "VOL -"+ "VOL +" key while inserting usb cable. Detected: SCI USB2Serial (COM19) [00:00:00] Sending loader. BOOT: SPRD3 Sending loader, keep boot key untill loader start. [00:00:04] Loader ok [00:00:04] Wait for loader.... Loader OK: ~"Spreadtrum Boot Block version 1.1 Changing bautrate OK. [00:00:04] [1]First boot done. [00:00:04] Sending second loader. [00:00:13] Second loader sent ok. New flash protocol detected. [00:00:13] Reading: system Error while read flash(1). [00:00:33] Reading: super System name: super Phone and firmware have same android [00:00:33] Reading: miscdata [00:00:33] Reading: l_fixnv1_a NVRAM saved to: C:\Users\Documents\spreadtrum_module\flashmode_nvr am_backup\_86XXXXX6612\_86740XXXXX6612_nvram_backu p.tar Phone have super partition. [00:00:44] Making flash ic repartition. [00:00:44] Start write: l_fixnv1_a Protecting GSM_CALI_ITEM_ID id: 0x2 Protecting LTE_Calibration id: 0xA05 Protecting LTE_Cali_Band1 id: 0x9C4 Protecting LTE_Cali_Band2 id: 0xA04 Protecting LTE_Cali_Band3 id: 0x9C8 Protecting LTE_Cali_Band4 id: 0x9C9 Protecting LTE_Cali_Band5 id: 0x9CA Protecting LTE_Cali_Band6 id: 0x9CB Protecting LTE_Cali_Band7 id: 0x9CC Protecting LTE_Cali_Band8 id: 0x9CD Protecting LTE_Cali_Band9 id: 0x9CE Protecting LTE_Cali_Band10 id: 0x9CF Protecting LTE_Cali_Band11 id: 0x9D0 Protecting LTE_Cali_Band12 id: 0x9D1 Protecting LTE_Cali_Band13 id: 0x9D2 Protecting LTE_Cali_Band14 id: 0x9D3 Protecting LTE_Cali_Band15 id: 0x9D4 Protecting LTE_Cali_Band16 id: 0x9D5 Protecting LTE_Cali_Band17 id: 0x9D6 Protecting LTE_Cali_Band18 id: 0x9D7 Protecting LTE_Cali_Band19 id: 0xA01 Protecting LTE_Cali_Band20 id: 0xA02 Protecting LTE_Cali_Band21 id: 0xA08 Protecting LTE_Cali_Band22 id: 0xA09 Protecting LTE_Cali_Band23 id: 0xA0A Protecting W_Calibration id: 0x12D Protecting AFC id: 0x9C7 Protecting GSM_Agc_Cali id: 0x4 Protecting BandSelect id: 0xA18 Protecting WIFI id: 0x199 Protecting MMITest id: 0x19A Protecting SUBSIDY_BLOB id: 0x91B Protecting SUBSIDY_PUBKEY id: 0x91D Protecting WIFICal1 id: 0x19F Protecting WIFICal2 id: 0x1A0 Protecting WIFICal3 id: 0x1A1 Protecting SIMLOCK_SIGN id: 0x1A3 Protecting SIMLOCK_PK id: 0x1A4 Protecting SPA_SIMLOCK_ENCRYPT_DATA id: 0x1D3 Protecting SPA_SIMLOCK_DYNAMIC_DATA id: 0x1D4 Protecting SIMLOCK_CUSTOMIZE_DATA id: 0x1F0 Protecting SIMLOCK_USER_DATA id: 0x1F1 Protecting SIMLOCK_NVCONTROL_KEY id: 0x1F2 Protecting SIMLOCK_KEY id: 0x1F4 Protecting SIMLOCK_CFG id: 0x7E4 Protecting SECURITY_DATA_PK id: 0x91E Protecting SECURITY_DATA_SIGN id: 0x91F Protecting NV_SIM_LOCK_FACTORY_RESET_TIME id: 0x930 Protecting NV_SIM_LOCK_ACTIVATE_TIME id: 0x931 Protecting NV_SIM_LOCK_RM_EXTRA_INFO id: 0x932 Protecting GSM_rf_8psk_tx_gain_table id: 0xAA3 Protecting IMEI_SIGN id: 0x1A6 Protecting ENGPCBA_DATA id: 0x1CC Protecting ENIMEI1_DATA id: 0x1CD Protecting ENIMEI2_DATA id: 0x1CE Protecting SIMLOCK_BLOB_V50 id: 0x8D1 [00:00:52] Start write: prodnv [00:00:52] Format: uboot_a [00:00:52] [uboot_a]Format OK. [00:00:52] Format: uboot_log [00:00:52] [uboot_log]Format OK. [00:00:52] Start write: splloader [00:00:52] Start write: vbmeta_a [00:00:53] Start write: ocdt_a [00:00:53] Start write: vbmeta_system_a [00:00:53] Start write: vbmeta_system_ext_a [00:00:53] Start write: vbmeta_vendor_a [00:00:53] Start write: vbmeta_product_a [00:00:53] Start write: l_modem_a [00:01:01] Start write: l_deltanv_a [00:01:01] Start write: l_ldsp_a [00:01:08] Start write: l_gdsp_a [00:01:11] Start write: pm_sys_a [00:01:12] Start write: gpsgl_a [00:01:12] Start write: gpsbd_a [00:01:12] Start write: wcnmodem_a [00:01:13] Start write: boot_a [00:01:31] Start write: dtbo_a [00:01:34] Start write: my_preload [00:01:38] Start write: super [00:21:30] Start write: cache [00:21:30] Start write: userdata [00:21:43] Start write: logo [00:21:43] Start write: fbootlogo [00:21:44] Start write: socko_a [00:22:01] Start write: odmko_a [00:22:02] Format: l_runtimenv1 [00:22:02] [l_runtimenv1]Format OK. [00:22:02] Format: misc [00:22:02] [misc]Format OK. [00:22:02] Format: sysdumpdb [00:22:02] [sysdumpdb]Format OK. [00:22:02] Start write: trustos_a [00:22:03] Start write: teecfg_a [00:22:03] Start write: sml_a [00:22:03] Start write: persist [00:22:04] Format: metadata [00:22:04] [metadata]Format OK. [00:22:04] Start write: uboot_a Flashing done. [can take 0-10 sec]Wait untill phone restart. Exe version: NckDongle Spreadtrum Module 2.1.2 Log saved: \Documents\spreadtrum_module\Saved_Logs\_writepac_ .txt Total Time: 00:22:14 Done. |
 |
| The Following User Says Thank You to unlockmachine44 For This Useful Post: |
| | #7895 (permalink) |
| No Life Poster      Join Date: Jul 2010 Location: North Africa
Posts: 891
Member: 1350724 Status: Offline Thanks Meter: 188 | realme c21y hard reset done Loader format:NEW Start Detect phone. Phone must be off with battery inside. Insert USB cable. Detected: SCI USB2Serial (COM19) Sending loader, keep boot key untill loader start. Loader OK: Spreadtrum Boot Block version 1.1 Changing bautrate OK. Send Second Loader. New flash metod detected. Build product name: S19610AA1 Build description: S19610AA1_ctcc-user 11 RP1A.201005.001 10519 release-keys Product name: RMX3261 Build Id: RP1A.201005.001 Android Release: 11 Android Version: RMX3261_11_A.74 Security patch: 2022-03-05 [misc]Formating userdata, wait... Wait untill phone will restart. Exe version: NckDongle Spreadtrum Module 2.1.2 Log saved: \Documents\spreadtrum_module\Saved_Logs\RMX3261_11 _A.74_format_userdata_misc_1.txt Total Time: 00:00:15 Done. |
 |
| | #7896 (permalink) |
| No Life Poster      Join Date: Jul 2010 Location: North Africa
Posts: 891
Member: 1350724 Status: Offline Thanks Meter: 188 | realme c21y hard reset done Loader format:NEW Start Detect phone. Phone must be off with battery inside. Insert USB cable. Detected: SCI USB2Serial (COM19) Sending loader, keep boot key untill loader start. Loader OK: Spreadtrum Boot Block version 1.1 Changing bautrate OK. Send Second Loader. New flash metod detected. Build product name: S19610AA1 Build description: S19610AA1_ctcc-user 11 RP1A.201005.001 10519 release-keys Product name: RMX3261 Build Id: RP1A.201005.001 Android Release: 11 Android Version: RMX3261_11_A.74 Security patch: 2022-03-05 [misc]Formating userdata, wait... Wait untill phone will restart. Exe version: NckDongle Spreadtrum Module 2.1.2 Log saved: \Documents\spreadtrum_module\Saved_Logs\RMX3261_11 _A.74_format_userdata_misc_1.txt Total Time: 00:00:15 Done. |
 |
| | #7897 (permalink) |
| Junior Member   Join Date: Nov 2011 Location: Adicora, Venezuela
Posts: 39
Member: 1687055 Status: Offline Thanks Meter: 6 | Blu C6L 2020 FRP ACTION: Erase FRP Loader format:NEW Start Detect phone. Phone must be off with battery inside. Long press "VOL -" key while inserting usb cable. Keep key untill boot complete. Detected: SPRD U2S Diag (COM14) Sending loader, keep boot key untill loader start. Loader OK: Spreadtrum Boot Block version 1.1 Changing bautrate OK. Send Second Loader. New flash metod detected. UID: TBGP58_17_18_28 *************** [S]Manufacturer: sprd [S]Brand: SPRD [S]Device: sp9832e_1h10_go [S]Model: sp9832e_1h10_gofu Build ID: QP1A.190711.020 CPU arhitecture: armeabi-v7a Hardware: sp9832e_1h10_go Build product name: sp9832e_1h10_go Build description: sp9832e_1h10_gofu-user 10 QP1A.190711.020 35434 release-keys Build Id: QP1A.190711.020 Android Release: 10 Android Version: QP1A.190711.020 release-keys Security patch: 2021-09-05 This phone have frp partition. Removing frp, wait... Format OK. [can take 0-10 sec]Wait untill phone restart. Exe version: NckDongle Spreadtrum Module 2.1.3 Log saved: C:\Users\Lrtz\Documents\spreadtrum_module\Saved_Lo gs\QP1A_190711_020release-keys_erase_frp.txt Total Time: 00:00:35 Done. |
 |
| | #7898 (permalink) |
| Junior Member   Join Date: Nov 2011 Location: Adicora, Venezuela
Posts: 39
Member: 1687055 Status: Offline Thanks Meter: 6 | Blu C6L 2020 FRP ACTION: Erase FRP Loader format:NEW Start Detect phone. Phone must be off with battery inside. Long press "VOL -" key while inserting usb cable. Keep key untill boot complete. Detected: SPRD U2S Diag (COM14) Sending loader, keep boot key untill loader start. Loader OK: Spreadtrum Boot Block version 1.1 Changing bautrate OK. Send Second Loader. New flash metod detected. UID: TBGP58_17_18_28 *************** [S]Manufacturer: sprd [S]Brand: SPRD [S]Device: sp9832e_1h10_go [S]Model: sp9832e_1h10_gofu Build ID: QP1A.190711.020 CPU arhitecture: armeabi-v7a Hardware: sp9832e_1h10_go Build product name: sp9832e_1h10_go Build description: sp9832e_1h10_gofu-user 10 QP1A.190711.020 35434 release-keys Build Id: QP1A.190711.020 Android Release: 10 Android Version: QP1A.190711.020 release-keys Security patch: 2021-09-05 This phone have frp partition. Removing frp, wait... Format OK. [can take 0-10 sec]Wait untill phone restart. Exe version: NckDongle Spreadtrum Module 2.1.3 Log saved: C:\Users\Lrtz\Documents\spreadtrum_module\Saved_Lo gs\QP1A_190711_020release-keys_erase_frp.txt Total Time: 00:00:35 Done. |
 |
| The Following User Says Thank You to therulass For This Useful Post: |
| | #7899 (permalink) |
| No Life Poster      Join Date: Jan 2020 Location: Algeria
Posts: 823
Member: 2944109 Status: Offline Thanks Meter: 665 | Oppo A54 (CPH2239) Reset To Factory Done 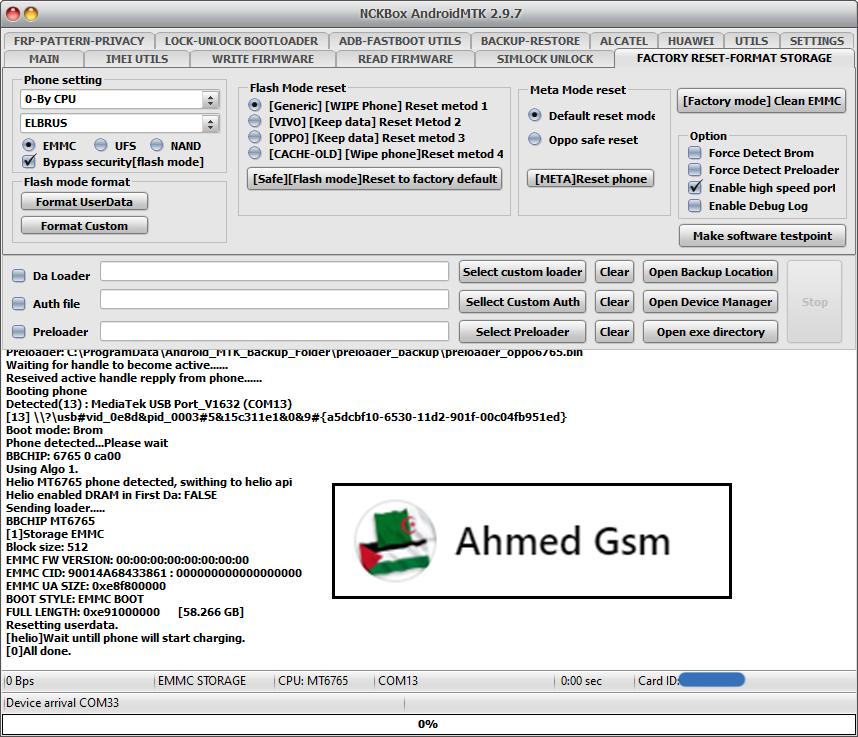 Code: [MISC]Action: Reset To Factory.
Selected 0-By CPU:ELBRUS
Exe version: NCKBox AndroidMTK 2.9.7
Phone must be off with battery inside.
Battery must be charged
Please connect phone in brom mode
For some phones need to keep "VOL-" button untill inserting USB cable.
For some phones need to keep "VOL+ and VOL-" button untill inserting USB cable.
For some phones need to keep "VOL+" button untill inserting USB cable.
Detected(13) : MediaTek USB Port_V1632 (COM13)
[13] \\?\usb#vid_0e8d&pid_0003#5&15c311e1&0&9#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
CPU: MT6765 CPU code: 766 Target config: e5
***********************
Secure boot enabled: true
Need serial link authorization: false
Need download agent authorization: true
SWJTAG enabled: true
EPP_PARAM at 0x600 after EMMC_BOOT/SDMMC_BOOT: false
Root cert required: false
Memory read authorization: true
Memory write authorization: true
Cmd 0xC8 blocked: true
***********************
Executing exploit, do not disconnect phone
Exploit has been executed successfully.
[3ec00]Dumping phone preloader.
Preloader: C:\ProgramData\Android_MTK_Backup_Folder\preloader_backup\preloader_oppo6765.bin
Waiting for handle to become active......
Reseived active handle repply from phone......
Booting phone
Detected(13) : MediaTek USB Port_V1632 (COM13)
[13] \\?\usb#vid_0e8d&pid_0003#5&15c311e1&0&9#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Boot mode: Brom
Phone detected...Please wait
BBCHIP: 6765 0 ca00
Using Algo 1.
Helio MT6765 phone detected, swithing to helio api
Helio enabled DRAM in First Da: FALSE
Sending loader.....
BBCHIP MT6765
[1]Storage EMMC
Block size: 512
EMMC FW VERSION: 00:00:00:00:00:00:00:00
EMMC CID: 90014A68433861 : 000000000000000000
EMMC UA SIZE: 0xe8f800000
BOOT STYLE: EMMC BOOT
FULL LENGTH: 0xe91000000 [58.266 GB]
Resetting userdata.
[helio]Wait untill phone will start charging.
[0]All done. |
 |
| The Following User Says Thank You to Gsm-Ahmed For This Useful Post: |
| | #7900 (permalink) |
| No Life Poster      Join Date: Jan 2020 Location: Algeria
Posts: 823
Member: 2944109 Status: Offline Thanks Meter: 665 | Wiko Ridge Fab 4G Flash Done 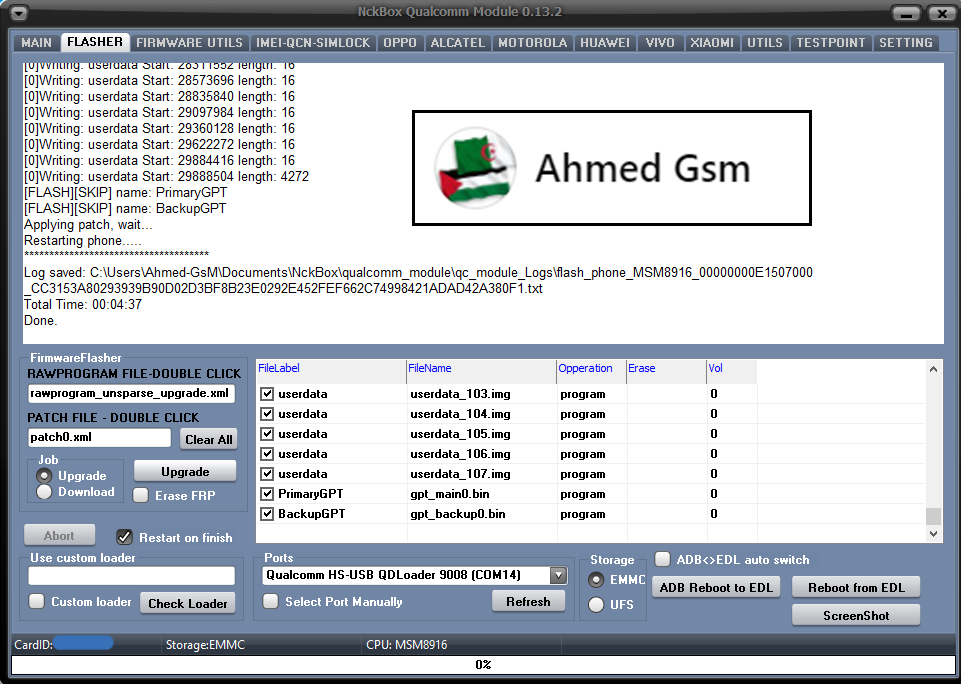 Code: Exe Version: NckBox Qualcomm Module 0.13.2 Operation: Upgrade Searching for phone..... Qualcomm HS-USB QDLoader 9008 (COM14) detected. Hello received. HW ID: 00000000E1507000 MSM8916 PK HASH: CC3153A80293939B90D02D3BF8B23E0292E452FEF662C74998421ADAD42A380F Checking database for suitable loader..... Arhitecture:32 bits [32]Sending loader, please wait.. Waiting for loader to start... [1] Send NOP ok, loader start. CPU: MSM8916 MaxPayloadSizeFromTargetInBytes: 4096 MaxPayloadSizeToTargetInBytes: 8192 Reading partition info, wait. Volume[0] Size: 14.68 GB Partitions count: 30 [018DBFDF]Userdata Size: 12.43 GB [FLASH][SKIP] name: modem [0]Writing: sbl1 Start: 262144 length: 489 [0]Writing: sbl1bak Start: 263168 length: 489 [0]Writing: aboot Start: 264192 length: 916 [0]Writing: abootbak Start: 266240 length: 916 [0]Writing: rpm Start: 268288 length: 296 [0]Writing: rpmbak Start: 269312 length: 296 [0]Writing: tz Start: 270336 length: 945 [0]Writing: tzbak Start: 271360 length: 945 [0]Writing: hyp Start: 272384 length: 112 [0]Writing: hypbak Start: 273408 length: 112 [0]Writing: splash Start: 284690 length: 5401 [0]Writing: fsg Start: 393280 length: 181 [0]Writing: sec Start: 396352 length: 1 [0]Writing: boot Start: 396384 length: 30069 [0]Writing: system Start: 461920 length: 262160 [0]Writing: system Start: 724904 length: 16 [0]Writing: system Start: 728888 length: 257312 [0]Writing: system Start: 986208 length: 16 [0]Writing: system Start: 990192 length: 258152 [0]Writing: system Start: 1248352 length: 16 [0]Writing: system Start: 1249192 length: 16 [0]Writing: system Start: 1253176 length: 257312 [0]Writing: system Start: 1510496 length: 16 [0]Writing: system Start: 1514480 length: 258152 [0]Writing: system Start: 1772640 length: 16 [0]Writing: system Start: 1773480 length: 16 [0]Writing: system Start: 1777464 length: 257312 [0]Writing: system Start: 2034784 length: 16 [0]Writing: system Start: 2038768 length: 258152 [0]Writing: system Start: 2296928 length: 16 [0]Writing: system Start: 2297768 length: 16 [0]Writing: system Start: 2301752 length: 257312 [0]Writing: system Start: 2559072 length: 16 [0]Writing: system Start: 2563056 length: 258152 [0]Writing: system Start: 2821216 length: 16 [0]Writing: system Start: 2822056 length: 16 [0]Writing: system Start: 2826040 length: 257312 [0]Writing: system Start: 3083360 length: 16 [0]Writing: system Start: 3087344 length: 258152 [0]Writing: system Start: 3345504 length: 16 [0]Writing: system Start: 3349488 length: 102784 [0]Writing: system Start: 3607648 length: 16 [0]Writing: system Start: 3611632 length: 149968 [0]Writing: system Start: 3761608 length: 26064 [0]Writing: cache Start: 3853408 length: 3016 [0]Writing: cache Start: 4115552 length: 16 [0]Writing: cache Start: 4115752 length: 16 [0]Writing: cache Start: 4377696 length: 16 [0]Writing: cache Start: 4380512 length: 8408 [0]Writing: recovery Start: 4389984 length: 31233 [0]Writing: userdata Start: 4718592 length: 10304 [0]Writing: userdata Start: 4980736 length: 16 [0]Writing: userdata Start: 4986952 length: 16 [0]Writing: userdata Start: 5242880 length: 16 [0]Writing: userdata Start: 5246968 length: 258072 [0]Writing: userdata Start: 5511240 length: 16 [0]Writing: userdata Start: 5767168 length: 16 [0]Writing: userdata Start: 6029312 length: 16 [0]Writing: userdata Start: 6035528 length: 16 [0]Writing: userdata Start: 6291456 length: 16 [0]Writing: userdata Start: 6553600 length: 16 [0]Writing: userdata Start: 6559816 length: 16 [0]Writing: userdata Start: 6815744 length: 16 [0]Writing: userdata Start: 7077888 length: 16 [0]Writing: userdata Start: 7084104 length: 16 [0]Writing: userdata Start: 7340032 length: 16 [0]Writing: userdata Start: 7602176 length: 16 [0]Writing: userdata Start: 7864320 length: 16 [0]Writing: userdata Start: 8126464 length: 16 [0]Writing: userdata Start: 8388608 length: 16 [0]Writing: userdata Start: 8650752 length: 16 [0]Writing: userdata Start: 8912896 length: 16 [0]Writing: userdata Start: 9175040 length: 16 [0]Writing: userdata Start: 9437184 length: 16 [0]Writing: userdata Start: 9699328 length: 16 [0]Writing: userdata Start: 9961472 length: 16 [0]Writing: userdata Start: 10223616 length: 16 [0]Writing: userdata Start: 10485760 length: 16 [0]Writing: userdata Start: 10747904 length: 16 [0]Writing: userdata Start: 11010048 length: 16 [0]Writing: userdata Start: 11272192 length: 16 [0]Writing: userdata Start: 11278408 length: 16 [0]Writing: userdata Start: 11534336 length: 16 [0]Writing: userdata Start: 11796480 length: 16 [0]Writing: userdata Start: 11802696 length: 16 [0]Writing: userdata Start: 12058624 length: 16 [0]Writing: userdata Start: 12320768 length: 16 [0]Writing: userdata Start: 12582912 length: 16 [0]Writing: userdata Start: 12845056 length: 16 [0]Writing: userdata Start: 13107200 length: 16 [0]Writing: userdata Start: 13369344 length: 16 [0]Writing: userdata Start: 13631488 length: 16 [0]Writing: userdata Start: 13893632 length: 16 [0]Writing: userdata Start: 14155776 length: 16 [0]Writing: userdata Start: 14417920 length: 16 [0]Writing: userdata Start: 14680064 length: 16 [0]Writing: userdata Start: 14942208 length: 16 [0]Writing: userdata Start: 15204352 length: 16 [0]Writing: userdata Start: 15466496 length: 16 [0]Writing: userdata Start: 15728640 length: 16 [0]Writing: userdata Start: 15990784 length: 16 [0]Writing: userdata Start: 16252928 length: 16 [0]Writing: userdata Start: 16515072 length: 16 [0]Writing: userdata Start: 16777216 length: 16 [0]Writing: userdata Start: 17039360 length: 16 [0]Writing: userdata Start: 17301504 length: 16 [0]Writing: userdata Start: 17563648 length: 16 [0]Writing: userdata Start: 17569864 length: 16 [0]Writing: userdata Start: 17825792 length: 16 [0]Writing: userdata Start: 18087936 length: 16 [0]Writing: userdata Start: 18350080 length: 16 [0]Writing: userdata Start: 18612224 length: 16 [0]Writing: userdata Start: 18874368 length: 16 [0]Writing: userdata Start: 19136512 length: 16 [0]Writing: userdata Start: 19398656 length: 16 [0]Writing: userdata Start: 19660800 length: 16 [0]Writing: userdata Start: 19922944 length: 16 [0]Writing: userdata Start: 20185088 length: 16 [0]Writing: userdata Start: 20447232 length: 16 [0]Writing: userdata Start: 20709376 length: 16 [0]Writing: userdata Start: 20971520 length: 16 [0]Writing: userdata Start: 21233664 length: 16 [0]Writing: userdata Start: 21495808 length: 16 [0]Writing: userdata Start: 21757952 length: 16 [0]Writing: userdata Start: 22020096 length: 16 [0]Writing: userdata Start: 22282240 length: 16 [0]Writing: userdata Start: 22544384 length: 16 [0]Writing: userdata Start: 22806528 length: 16 [0]Writing: userdata Start: 23068672 length: 16 [0]Writing: userdata Start: 23330816 length: 16 [0]Writing: userdata Start: 23592960 length: 16 [0]Writing: userdata Start: 23855104 length: 16 [0]Writing: userdata Start: 24117248 length: 16 [0]Writing: userdata Start: 24379392 length: 16 [0]Writing: userdata Start: 24641536 length: 16 [0]Writing: userdata Start: 24903680 length: 16 [0]Writing: userdata Start: 25165824 length: 16 [0]Writing: userdata Start: 25427968 length: 16 [0]Writing: userdata Start: 25690112 length: 16 [0]Writing: userdata Start: 25952256 length: 16 [0]Writing: userdata Start: 25958472 length: 16 [0]Writing: userdata Start: 26214400 length: 16 [0]Writing: userdata Start: 26476544 length: 16 [0]Writing: userdata Start: 26738688 length: 16 [0]Writing: userdata Start: 27000832 length: 16 [0]Writing: userdata Start: 27262976 length: 16 [0]Writing: userdata Start: 27525120 length: 16 [0]Writing: userdata Start: 27787264 length: 16 [0]Writing: userdata Start: 28049408 length: 16 [0]Writing: userdata Start: 28311552 length: 16 [0]Writing: userdata Start: 28573696 length: 16 [0]Writing: userdata Start: 28835840 length: 16 [0]Writing: userdata Start: 29097984 length: 16 [0]Writing: userdata Start: 29360128 length: 16 [0]Writing: userdata Start: 29622272 length: 16 [0]Writing: userdata Start: 29884416 length: 16 [0]Writing: userdata Start: 29888504 length: 4272 [FLASH][SKIP] name: PrimaryGPT [FLASH][SKIP] name: BackupGPT Applying patch, wait... Restarting phone..... ************************************* Log saved: C:\Users\Ahmed-GsM\Documents\NckBox\qualcomm_module\qc_module_Logs\flash_phone_MSM8916_00000000E1507000_CC3153A80293939B90D02D3BF8B23E0292E452FEF662C74998421ADAD42A380F1.txt Total Time: 00:04:37 Done. |
 |
| | #7901 (permalink) |
| No Life Poster      | ACTION: Direct Unlock Detecting phone, wait... Using connection mode 1 Detected: SPRD U2S Diag (COM14) Platform Version: MOCORTM_20A_W21.30.5_Debug Project Version: sharkl5_pub_5m BASE Version: 4G_MODEM_20A_W21.30.5 HW Version: sharkl5_5m_modem 07-30-2021 02:19:42 Build number: M8L_Plus-user 11 R01005 1631767524 release-keys EMMC DDR SIZE :29.00 GB+1.00 GB UID: 242b04be977758188dc95f86166d813e282ea4f9bb84a68443 630534dbe1a043 IMEI 1: 359598950xxxxxx IMEI 2: 867400020316620 IMEI 3: 867400020316638 IMEI 4: 867400020316646 BT: 80FD7AFA4F79 WIFI: 80FD7AF96519 Reading simlock backup, wait.... Saved to: C:\Users\kenjaTECH\Documents\spreadtrum_module\dia g_nvram_backup\M8L_Plus-user_11_R01005_1631767524_release-keys_359598950xxxxxx__diag_simlock_nvram_backup.ta r Simlock Status: SIMLOCK: ACTIVE NETWORK SUBNET: INACTIVE SP LOCK: ACTIVE CORPORATE: INACTIVE USER LOCK: INACTIVE [3]Simlock Type: 0 0 Sim 1 Unlock Code: 84744773 Sim 2 Unlock Code: 41023788 Warning, this is factory key, some opperators can modify factory key. Unlock is supported for this phone Writing simlock... Writing simlock ok Done. Exe version: NckBox Spreadtrum Module 2.1.4 Log saved: C:\Users\kenjaTECH\Documents\spreadtrum_module\Sav ed_Logs\M8L_Plus- |
 |
| | #7902 (permalink) |
| No Life Poster      Join Date: Jan 2020 Location: Algeria
Posts: 823
Member: 2944109 Status: Offline Thanks Meter: 665 | BlackBerry 9800 Torch MEP0 Unlock Done 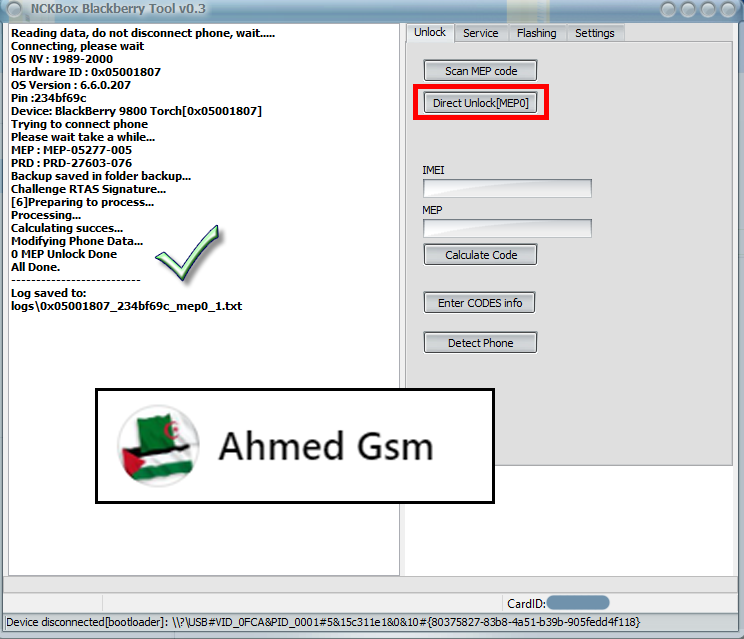 Code: Reading data, do not disconnect phone, wait..... Connecting, please wait OS NV : 1989-2000 Hardware ID : 0x05001807 OS Version : 6.6.0.207 Pin :234bf69c Device: BlackBerry 9800 Torch[0x05001807] Trying to connect phone Please wait take a while... MEP : MEP-05277-005 PRD : PRD-27603-076 Backup saved in folder backup... Challenge RTAS Signature... [6]Preparing to process... Processing... Calculating succes... Modifying Phone Data... 0 MEP Unlock Done All Done. -------------------------- Log saved to: logs\0x05001807_234bf69c_mep0_1.txt |
 |
| The Following User Says Thank You to Gsm-Ahmed For This Useful Post: |
| | #7903 (permalink) |
| No Life Poster        Join Date: Mar 2011 Location: dominican republic Age: 45
Posts: 2,104
Member: 1537078 Status: Offline Sonork: celular center Thanks Meter: 576 | FRP TCL 4187U SUCCESS Spreadtrum 9863a_3h10 Board First 16 bytes from public rsa key. AD7E67E09F57F0A391493DE4F96FDFBC *************** Phone Storage: EMMC SELECTED: SC9863A_GENERIC([simlock]A10+) ACTION: Erase FRP Loader format:NEW Start Detect phone. Phone must be off with battery inside. Long press "VOL -"+ "VOL +" key while inserting usb cable. Keep key untill boot complete. Detected: SCI USB2Serial (COM43) Sending loader, keep boot key untill loader start. Loader OK: Spreadtrum Boot Block version 1.1 Changing bautrate OK. Send Second Loader. New flash metod detected. UID: T4VK55_22_24_12 *************** [S]Manufacturer: TCL [S]Brand: TCL [S]Device: Jakarta_Lite [S]Model: 4187U Build ID: QP1A.190711.020 CPU arhitecture: arm64-v8a Hardware: s9863a1h10 Build product name: 4187U Build description: s9863a1h10_Natv-user 10 QP1A.190711.020 49217 release-keys Build Id: QP1A.190711.020 Android Release: 10 Android Version: 4187U_3JBR_2SIM_V1.4_20201208_UNLOCK Security patch: 2020-12-05 TCT sys version: O87UBR14 This phone have frp partition. Removing frp, wait... Format OK. [can take 0-10 sec]Wait untill phone restart. Exe version: NckBox Spreadtrum Module 2.1.4 Log saved: C:\Users\Cell Center\Documents\spreadtrum_module\Saved_Logs\4187 U_3JBR_2SIM_V1_4_20201208_UNLOCK_erase_frp.txt Total Time: 00:00:19 Done. |
 |
| The Following User Says Thank You to chipscell25 For This Useful Post: |
| | #7904 (permalink) |
| No Life Poster      Join Date: Jan 2020 Location: Algeria
Posts: 823
Member: 2944109 Status: Offline Thanks Meter: 665 | Condor T9 Plus (SP647) Flash Firmware Done Condor T9 Plus (SP647) Flash Firmware Done 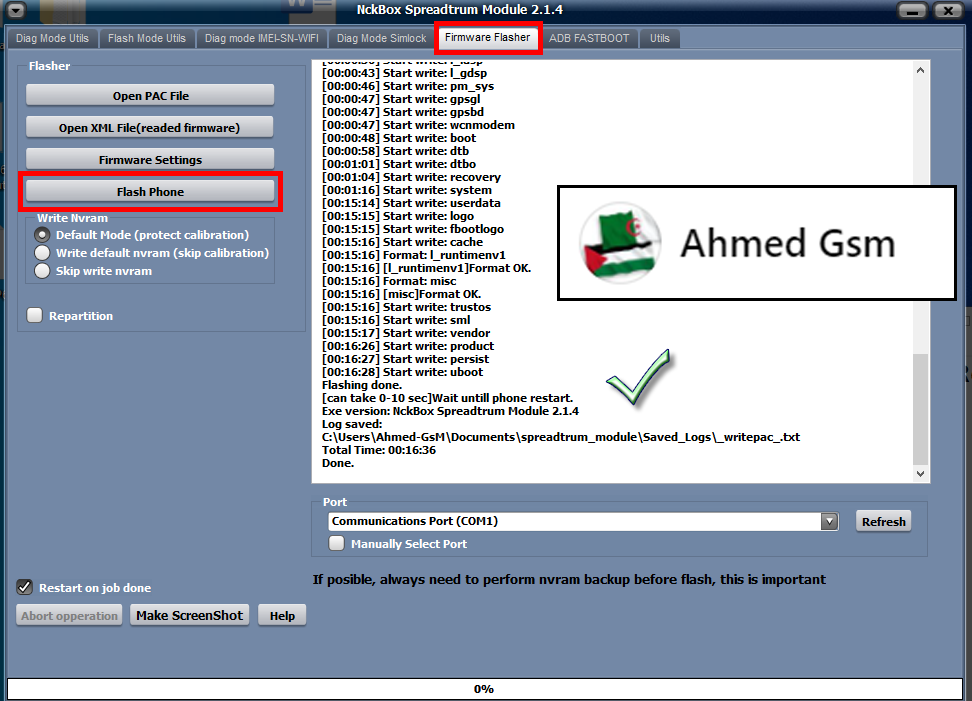 Code: ACTION: Flash Firmware. Selected firmware: Condor_SP647_V10_20190606_1114.pac NV: Default Mode (protect calibration) Device Storage: EMMC Start Detect phone. Phone must be off with battery inside. Long press "VOL -"+ "VOL +" key while inserting usb cable. Keep key untill boot complete. Detected: SPRD U2S Diag (COM15) [00:00:00] Sending loader. BOOT: SPRD3 Sending loader, keep boot key untill loader start. [00:00:03] Loader ok [00:00:03] Wait for loader.... Loader OK: ~"Spreadtrum Boot Block version 1.1 Changing bautrate OK. [00:00:03] [1]First boot done. [00:00:03] Sending second loader. [00:00:08] Second loader sent ok. New flash protocol detected. [00:00:08] Reading: system System name: system Phone and firmware have same android [00:00:09] Reading: miscdata [00:00:09] Reading: l_fixnv1 NVRAM saved to: C:\Users\Ahmed-GsM\Documents\spreadtrum_module\flashmode_nvram_backup\_355431101144853\_355431101144853_nvram_backup.tar [00:00:21] Start write: l_fixnv1 Protecting GSM_CALI_ITEM_ID id: 0x2 Protecting LTE_Calibration id: 0xA05 Protecting LTE_Cali_Band1 id: 0x9C4 Protecting LTE_Cali_Band2 id: 0xA04 Protecting LTE_Cali_Band3 id: 0x9C8 Protecting LTE_Cali_Band4 id: 0x9C9 Protecting LTE_Cali_Band5 id: 0x9CA Protecting LTE_Cali_Band6 id: 0x9CB Protecting LTE_Cali_Band7 id: 0x9CC Protecting LTE_Cali_Band8 id: 0x9CD Protecting LTE_Cali_Band9 id: 0x9CE Protecting LTE_Cali_Band10 id: 0x9CF Protecting LTE_Cali_Band11 id: 0x9D0 Protecting LTE_Cali_Band12 id: 0x9D1 Protecting LTE_Cali_Band13 id: 0x9D2 Protecting LTE_Cali_Band14 id: 0x9D3 Protecting LTE_Cali_Band15 id: 0x9D4 Protecting LTE_Cali_Band16 id: 0x9D5 Protecting LTE_Cali_Band17 id: 0x9D6 Protecting LTE_Cali_Band18 id: 0x9D7 Protecting LTE_Cali_Band19 id: 0xA01 Protecting LTE_Cali_Band20 id: 0xA02 Protecting LTE_Cali_Band21 id: 0xA08 Protecting LTE_Cali_Band22 id: 0xA09 Protecting LTE_Cali_Band23 id: 0xA0A Protecting W_Calibration id: 0x12D Protecting AFC id: 0x9C7 Protecting GSM_Agc_Cali id: 0x4 Protecting BandSelect id: 0xA18 Protecting WIFI id: 0x199 Protecting MMITest id: 0x19A Protecting SUBSIDY_BLOB id: 0x91B Protecting SUBSIDY_PUBKEY id: 0x91D Protecting WIFICal1 id: 0x19F Protecting WIFICal2 id: 0x1A0 Protecting WIFICal3 id: 0x1A1 Protecting SIMLOCK_SIGN id: 0x1A3 Protecting SIMLOCK_PK id: 0x1A4 Protecting SIMLOCK_CUSTOMIZE_DATA id: 0x1F0 Protecting SIMLOCK_USER_DATA id: 0x1F1 Protecting SIMLOCK_NVCONTROL_KEY id: 0x1F2 Protecting SIMLOCK_KEY id: 0x1F4 Protecting SIMLOCK_CFG id: 0x7E4 Protecting GSM_rf_8psk_tx_gain_table id: 0xAA3 [00:00:28] Start write: prodnv [00:00:28] Format: uboot [00:00:28] [uboot]Format OK. [00:00:28] Format: uboot_log [00:00:28] [uboot_log]Format OK. [00:00:28] Start write: splloader [00:00:28] Start write: vbmeta [00:00:29] Start write: l_modem [00:00:36] Start write: l_ldsp [00:00:43] Start write: l_gdsp [00:00:46] Start write: pm_sys [00:00:47] Start write: gpsgl [00:00:47] Start write: gpsbd [00:00:47] Start write: wcnmodem [00:00:48] Start write: boot [00:00:58] Start write: dtb [00:01:01] Start write: dtbo [00:01:04] Start write: recovery [00:01:16] Start write: system [00:15:14] Start write: userdata [00:15:15] Start write: logo [00:15:15] Start write: fbootlogo [00:15:16] Start write: cache [00:15:16] Format: l_runtimenv1 [00:15:16] [l_runtimenv1]Format OK. [00:15:16] Format: misc [00:15:16] [misc]Format OK. [00:15:16] Start write: trustos [00:15:16] Start write: sml [00:15:17] Start write: vendor [00:16:26] Start write: product [00:16:27] Start write: persist [00:16:28] Start write: uboot Flashing done. [can take 0-10 sec]Wait untill phone restart. Exe version: NckBox Spreadtrum Module 2.1.4 Log saved: C:\Users\Ahmed-GsM\Documents\spreadtrum_module\Saved_Logs\_writepac_.txt Total Time: 00:16:36 Done. |
 |
| | #7905 (permalink) |
| No Life Poster      Join Date: Jan 2020 Location: Algeria
Posts: 823
Member: 2944109 Status: Offline Thanks Meter: 665 | Condor P6 Plus (PGN-522) FRP Reset Done Condor P6 Plus (PGN-522) FRP Reset Done  Code: Exe version: NCKBox AndroidMTK 2.9.7
Selected model: 0-By CPU ELBRUS
[auto]Action: Reset FRP
Phone must be off with battery inside.
Battery must be charged
Please insert USB cable now...
For some phones need to keep "VOL-" button untill inserting USB cable.
For some phones need to keep "VOL+ and VOL-" button untill inserting USB cable.
For some phones need to keep "VOL+" button untill inserting USB cable.
Detected(5) : MediaTek PreLoader USB VCOM_V1632 (Android) (COM5)
[5] \\?\usb#vid_0e8d&pid_2000#5&15c311e1&0&10#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Boot mode: Preloader
BBCHIP: 335 0 ca00
Using Algo 2.
Phone detected...Please wait
Sending DA agent, please wait...
----------------------------------------------------
BaseBand CPU :MT6735M
BaseBand CPU Secure Version : FF
BaseBand CPU Bootloader Version : 01
----------------------------------------------------
INT RAM: 128 KB SDRAM
EXT RAM: 1 GB DRAM
----------------------------------------------------
EMMC: (116Gb+8192Mb) SAMSUNG 0x464531324d42
EMMC FW VERSION: 07:00:00:00:00:00:00:00
EMMC CID: 150100464531324D42 : 00000000000000
EMMC UA SIZE: 0x3a3e00000
BOOT STYLE: EMMC BOOT
FULL LENGTH: 0x3a4a00000 [14.572 GB]
Checking data, wait...
Writing FRP, wait...
FRP Reset Done.
Wait untill phone will start charging.
[0]All done. |
 |
| The Following User Says Thank You to Gsm-Ahmed For This Useful Post: |
 |
| Bookmarks |
| |
|
|