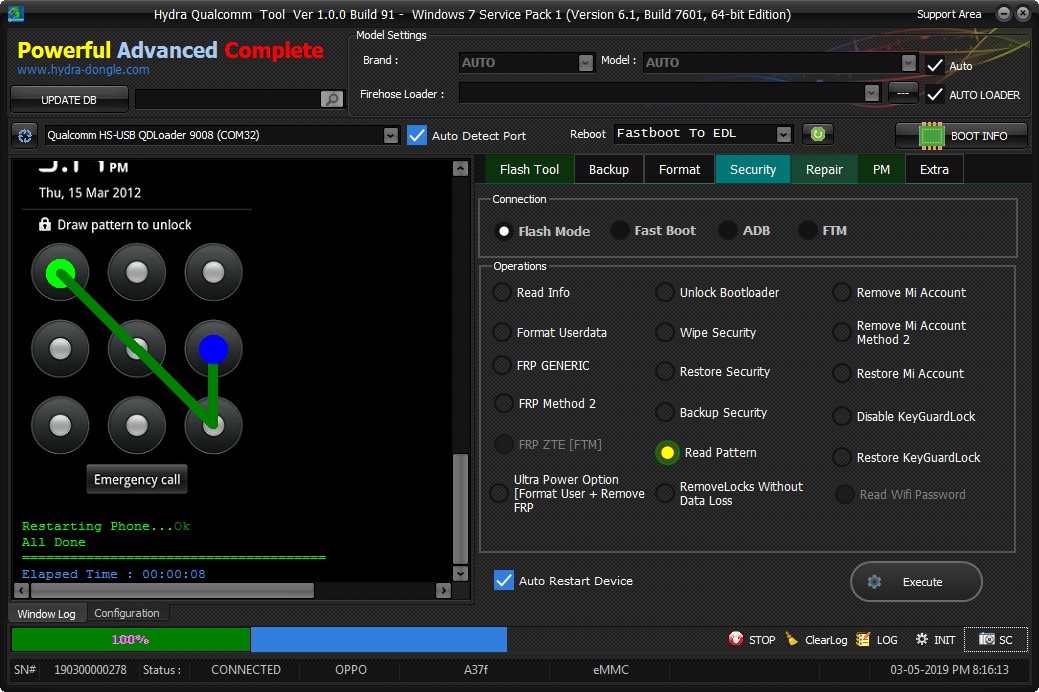
Code:
Hydra Qualcomm Tool Ver 1.0.0 Build 91
Windows 7 Service Pack 1 (Version 6.1, Build 7601, 64-bit Edition)
******* Dongle Info *******
Version : Hydra Tool v 1.1
Serial : 190300000278
Initialize : OKAY
Status : Activated
Selected Comport : Auto
Selected Loader : Auto
Searching Qualcomm 9008 Port[FOUND](COM32)
Getting device info...
Serial No.: 0x2357A18A
MSM ID : 0x007050E1
PBL Ver : 00000000
PK HASH : CC3153A80293939B90D02D3BF8B23E0292E452FEF662C74998421ADAD42A380F
Sending Firehose Loader[8916.mbn]Ok
Connecting to Firehose...
Ping...Ok
Configuration......Ok
Chip Configuration :
MemoryName : eMMC
MaxPayloadSizeToTargetInBytes : 16384
MaxPayloadSizeToTargetInBytesSupported : 16384
MaxPayloadSizeFromTargetInBytes : 4096
MaxXMLSizeInBytes : 4096
TargetName : 8916
Version : 1
Running : Ok
Phone Information........
Model : A37f
Brand : OPPO
Android Ver : 5.1.1
Board : msm8916
Display ID : A37fEX_11_190228
Security Patch : 2018-03-01
Emmc_size :
Platform : msm8916
Kernel ID : 2018-03-01
Marketname :
OTA Version Name : A37fEX_11_190228
SYS USB CONFIG :
FRPPST : /dev/block/bootdevice/by-name/config
======================================
Reading Pattern lock...
Trying to search : gatekeeper.pattern.key
Trying to search : personalpattern.key
Trying to search : cm_gesture.key
Trying to search : gesture.key FOUND
Gesture Data : 8207C5CC9B3B6F2BF0C2D4824AE8B8560946F3DF
Bruteforcing pattern hash..Please wait for few seconds
Pattern Code : 1596
1 2 3
4 5 6
7 8 9