



  |
 |
|
Welcome to the GSM-Forum forums. You are currently viewing our boards as a guest which gives you limited access to view most discussions and access our other features. Only registered members may post questions, contact other members or search our database of over 8 million posts. Registration is fast, simple and absolutely free so please - Click to REGISTER! If you have any problems with the registration process or your account login, please contact contact us . |
| |||||||
| Register | FAQ | Donate | Forum Rules | Root any Device | ★iPhone Unlock★ | ★ Direct Codes ★ | Direct Unlock Source |
 |
| | LinkBack | Thread Tools | Display Modes |
| | #1486 (permalink) | |
| Product Manager      Join Date: Apr 2008 Location: Whitehole throught Blackhole!
Posts: 9,582
Member: 747989 Status: Offline Sonork: 100.1593052 Thanks Meter: 8,621 | Vivo S1 Pro (PD1945F) Successfully formatted by Hydra Tool Vivo S1 Pro (PD1945F) Successfully formatted by Hydra Tool Screen Short:  Logs: Quote:
Dipendra Pathak | |
 |
| | #1487 (permalink) | |
| Product Manager      Join Date: Apr 2008 Location: Whitehole throught Blackhole!
Posts: 9,582
Member: 747989 Status: Offline Sonork: 100.1593052 Thanks Meter: 8,621 | Oppo F9 (CPH1823) System File successfully flashed by Hydra Tool Oppo F9 (CPH1823) System File successfully flashed by Hydra Tool Screen Short:  Logs: Quote:
Dipendra Pathak | |
 |
| | #1488 (permalink) | |
| Product Manager      Join Date: Apr 2008 Location: Whitehole throught Blackhole!
Posts: 9,582
Member: 747989 Status: Offline Sonork: 100.1593052 Thanks Meter: 8,621 | Xiaomi Redmi 5A (riva) Zero Wipe FRP successfully removed by Hydra Tool Xiaomi Redmi 5A (riva) Zero Wipe FRP successfully removed by Hydra Tool Screen Short:  Logs: Quote:
Dipendra Pathak | |
 |
| | #1489 (permalink) | |
| Product Manager      Join Date: Apr 2008 Location: Whitehole throught Blackhole!
Posts: 9,582
Member: 747989 Status: Offline Sonork: 100.1593052 Thanks Meter: 8,621 | Xiaomi Redmi Note 9 Merlin Removed Mi Account Successfully Done by Hydra Tool Xiaomi Redmi Note 9 Merlin Removed Mi Account Successfully Done by Hydra Tool Screen Short:  Logs: Quote:
Dipendra Pathak | |
 |
| | #1490 (permalink) | |
| Product Manager      Join Date: Apr 2008 Location: Whitehole throught Blackhole!
Posts: 9,582
Member: 747989 Status: Offline Sonork: 100.1593052 Thanks Meter: 8,621 | Xiomi Mi CC 9 Successfully Flashed by Hydra Tool Xiomi Mi CC 9 Successfully Flashed by Hydra Tool Screen Short:  Logs: Quote:
Dipendra Pathak | |
 |
| | #1491 (permalink) | |
| Product Manager      Join Date: Apr 2008 Location: Whitehole throught Blackhole!
Posts: 9,582
Member: 747989 Status: Offline Sonork: 100.1593052 Thanks Meter: 8,621 | Xiaomi Redmi Note 7 Pro (Violet) Prisist flashed successfully by Hydra Tool Xiaomi Redmi Note 7 Pro (Violet) Prisist flashed successfully by Hydra Tool Screen Short:  Logs: Quote:
Dipendra Pathak | |
 |
| The Following User Says Thank You to Dipendra Pathak For This Useful Post: |
| | #1492 (permalink) | |
| Product Manager      Join Date: Apr 2008 Location: Whitehole throught Blackhole!
Posts: 9,582
Member: 747989 Status: Offline Sonork: 100.1593052 Thanks Meter: 8,621 | Oppo A37m (Neo 9) Rebuilding user Data successfully Done by Hydra Tool Oppo A37m (Neo 9) Rebuilding user Data successfully Done by Hydra Tool Screen Short:  Logs: Quote:
Dipendra Pathak | |
 |
| The Following User Says Thank You to Dipendra Pathak For This Useful Post: |
| | #1493 (permalink) |
| No Life Poster        Join Date: Aug 2011 Location: bagmati pradesh
Posts: 3,296
Member: 1626780 Status: Offline Thanks Meter: 1,275 | --------------------------------- Searching for MTK Device...Found Port Identification :METAMODE Preloader FriendlyName :MediaTek USB VCOM (Android) (COM55) SymbolicName :\??\USB#VID_0E8D&PID_2007#5&147efee4&0&2#{a5dcbf1 0-6530-11d2-901f-00c04fb951ed} Driver Ver :01/22/2015,3.0.1504.0 META Phone Info . . . MCUID: 8U ` mt6771 ME_SO: DATE : Tue Jan 26 23:59:16 CST 2021 MODEL: CPH1823EX_11_F.17 ME_SWVER: CPH1823_11_F.17_210126_cc65c34e Reset to Factory Default Ok Rebooting.... Done!!! Elapsed Time : 00:00:01 |
 |
| The Following User Says Thank You to malka4u For This Useful Post: |
| | #1494 (permalink) | |
| Product Manager      Join Date: Apr 2008 Location: Whitehole throught Blackhole!
Posts: 9,582
Member: 747989 Status: Offline Sonork: 100.1593052 Thanks Meter: 8,621 | Oppo A37m (Neo 9) Rebuilding user Data successfully Done by Hydra Tool Oppo A37m (Neo 9) Rebuilding user Data successfully Done by Hydra Tool Screen Short:  Logs: Quote:
Dipendra Pathak | |
 |
| | #1495 (permalink) | |
| Product Manager      Join Date: Apr 2008 Location: Whitehole throught Blackhole!
Posts: 9,582
Member: 747989 Status: Offline Sonork: 100.1593052 Thanks Meter: 8,621 | Vivo Y91 FRP successfully removed by Hydra Tool Vivo Y91 FRP successfully removed by Hydra Tool Screen Short:  Logs: Quote:
Dipendra Pathak | |
 |
| | #1496 (permalink) | |
| Product Manager      Join Date: Apr 2008 Location: Whitehole throught Blackhole!
Posts: 9,582
Member: 747989 Status: Offline Sonork: 100.1593052 Thanks Meter: 8,621 | Oppo Realme 6 (RMX2001) Safe Format Master Clear 1 Successfully done by Hydra Tool Oppo Realme 6 (RMX2001) Safe Format Master Clear 1 Successfully done by Hydra Tool Screen Short:  Logs: Quote:
Dipendra Pathak | |
 |
| | #1497 (permalink) |
| No Life Poster      Join Date: Jan 2020 Location: Algeria
Posts: 814
Member: 2944109 Status: Offline Thanks Meter: 656 | Condor Plume H1 (SP620) Ultra Power Option Condor Plume H1 (SP620) Ultra Power Option successfully done by Hydra Tool 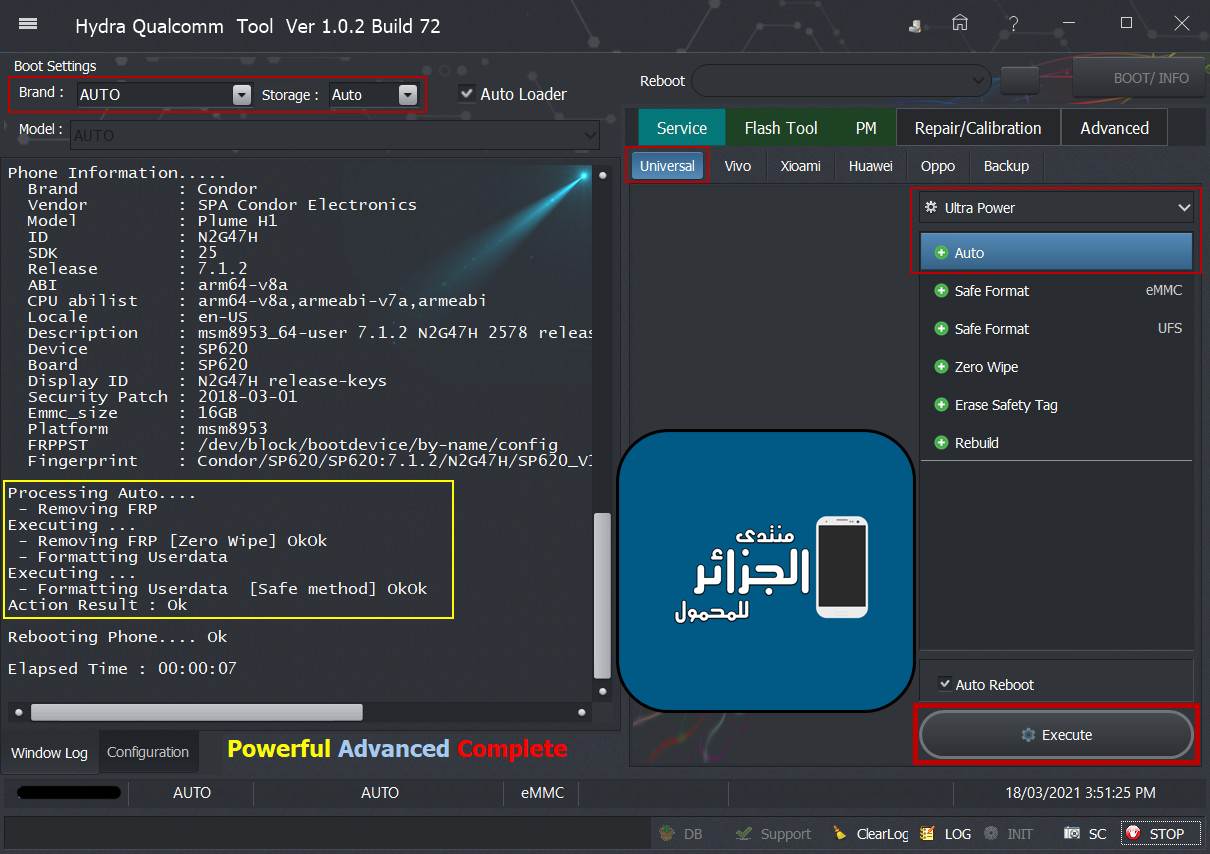 Code: PreOperation Configuration
Brand : AUTO Model : AUTO Storage : Auto
Loader: Auto
Port : Auto
Connection :
Searching for Qualcomm 9008 Device...Found
FriendlyName :Qualcomm HS-USB QDLoader 9008 (COM9)
SymbolicName :\??\USB#VID_05C6&PID_9008#6&12e3c9ed&0&1#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :08/02/2017,2.1.2.7
Getting device info..Ok
Device MODE : Firehose
Connecting to Firehose...
Ping.. Ok
Configuration......
Identifying Chip....
Ok
Chip Configuration :
MemoryName : eMMC
MaxPayloadSizeToTargetInBytes : 1048576
MaxPayloadSizeToTargetInBytesSupported : 1048576
MaxPayloadSizeFromTargetInBytes : 4096
MaxXMLSizeInBytes : 4096
TargetName : 8953
Version : 1
*** STORAGE DEVICE INFO ***
Memory Type : eMMC
Block Size in Bytes : 512
Page Size : 512
Manufacturer ID : 144
Serial Number : 934817224
Firmware Version : 165
Product Name : HAG4a2
Physical Partitions : 3
Total Logical Blocks:
Drive [0] 30777344[14,676 GB]
Drive [1] 8192[4 MB]
Drive [2] 8192[4 MB]
Protocol : Universal
Running : Ok
Reading GPT[3]
Drive [0] 48 Items
Drive [1] 0 Items
Drive [2] 0 Items
Phone Information.....
Brand : Condor
Vendor : SPA Condor Electronics
Model : Plume H1
ID : N2G47H
SDK : 25
Release : 7.1.2
ABI : arm64-v8a
CPU abilist : arm64-v8a,armeabi-v7a,armeabi
Locale : en-US
Description : msm8953_64-user 7.1.2 N2G47H 2578 release-keys
Device : SP620
Board : SP620
Display ID : N2G47H release-keys
Security Patch : 2018-03-01
Emmc_size : 16GB
Platform : msm8953
FRPPST : /dev/block/bootdevice/by-name/config
Fingerprint : Condor/SP620/SP620:7.1.2/N2G47H/SP620_V11.0_20170925:user/release-keys
Processing Auto....
- Removing FRP
Executing ...
- Removing FRP [Zero Wipe] OkOk
- Formatting Userdata
Executing ...
- Formatting Userdata [Safe method] OkOk
Action Result : Ok
Rebooting Phone.... Ok
Elapsed Time : 00:00:07 |
 |
| | #1498 (permalink) |
| No Life Poster      Join Date: Jan 2020 Location: Algeria
Posts: 814
Member: 2944109 Status: Offline Thanks Meter: 656 | Ace Buzz 2 lite Ultra Power Option Ace Buzz 2 lite Ultra Power Option successfully done by Hydra Tool 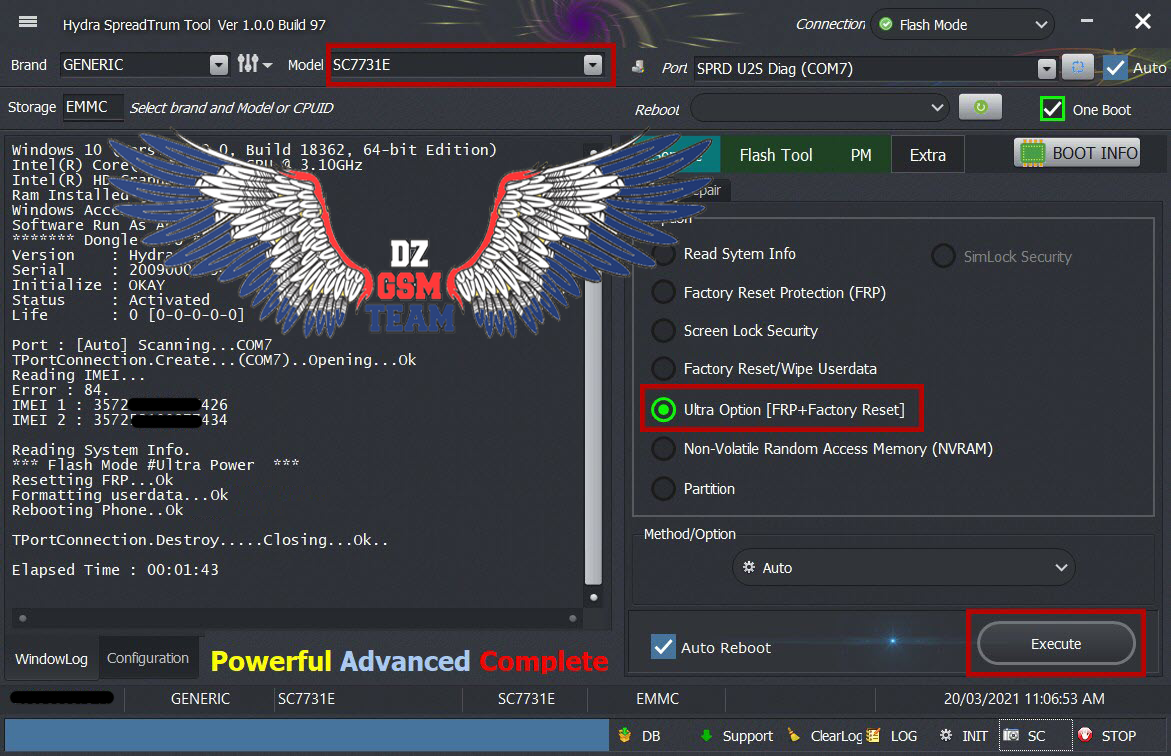 Code: Port : [Auto] Scanning...COM7 TPortConnection.Create...(COM7)..Opening...Ok Reading IMEI... Error : 84. IMEI 1 : 35725XXXXXXX426 IMEI 2 : 35725XXXXXXX434 Reading System Info. *** Flash Mode #Ultra Power *** Resetting FRP...Ok Formatting userdata...Failed Rebooting Phone..Failed TPortConnection.Destroy.....Closing...Ok.. Elapsed Time : 00:01:43 |
 |
| The Following User Says Thank You to Gsm-Ahmed For This Useful Post: |
| | #1499 (permalink) |
| No Life Poster      Join Date: Jan 2020 Location: Algeria
Posts: 814
Member: 2944109 Status: Offline Thanks Meter: 656 | Oppo A1k CPH1923 Pin Unlock MetaMode Oppo A1k CPH1923 Pin Unlock MetaMode Done Hydra Tool 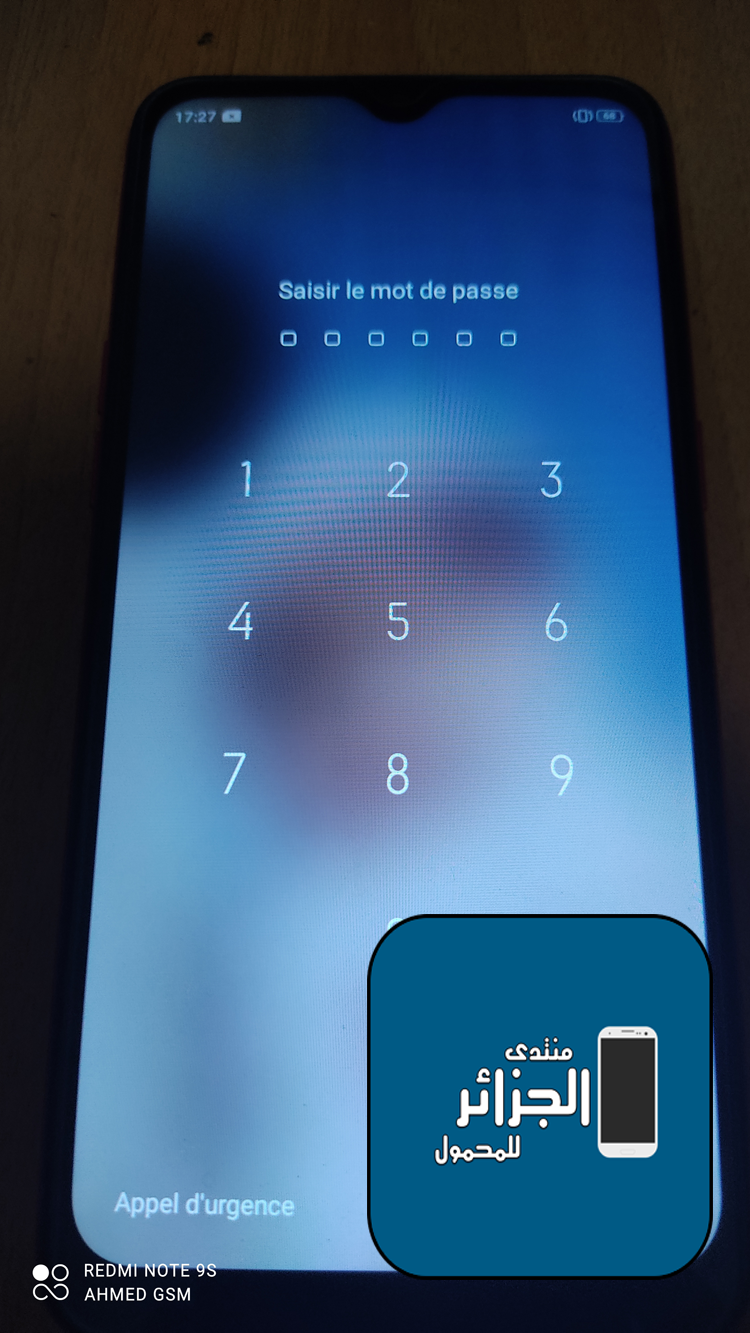  Code: ---------------------------------
Searching for MTK Device...Found
Port Identification :METAMODE Preloader
FriendlyName :MediaTek PreLoader USB VCOM_V1632 (Android) (COM11)
SymbolicName :\??\USB#VID_22D9&PID_0006#6&12e3c9ed&0&1#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :01/22/2015,3.0.1504.0
META Phone Info . . .
MCUID: 8U ` mt6765
ME_SO:
DATE : Mon Dec 21 13:37:55 CST 2020
MODEL: CPH1923EX_11_A.38
ME_SWVER: CPH1923_11_A.38_201221_de900167
MANUFACTURER : OPPO
BOARD : oppo6762_18540
MODEL : CPH1923
NAME : unknown
BUILD.DISPLAY.ID : CPH1923EX_11_A.38
USB.MODEL : unknown
BUILD.VERSION.RELEASE : 9
BUILD.VERSION.SECURITY_PATCH : 2021-01-05
DEVICE : unknown
BRAND : OPPO
SERVICE CALL IPHONESUBINFO 1 : unknown
PERSIST.MTK.WCN.COMBO.CHIPID : unknown
SERIALNO : unknown
MEDIATEK.PLATFORM : unknown
MEDIATEK.CHIP_VER : unknown
HARDWARE : mt6765
MEDIATEK.VERSION.RELEASE : CPH1923_11_A.38_201221
OEM_UNLOCK_SUPPORTED : unknown
EXPECT.RECOVERY_ID : unknown
FRP.PST : /dev/block/platform/bootdevice/by-name/frp
BUILD.FINGERPRINT : unknown
GSM.VERSION.BASEBAND : unknown
SW.BUILDID : unknown
RIL.IMEI : unknown
SYS.USB.CONFIG : unknown
IMEI 1 :
IMEI 2 :
Elapsed Time : 00:00:03 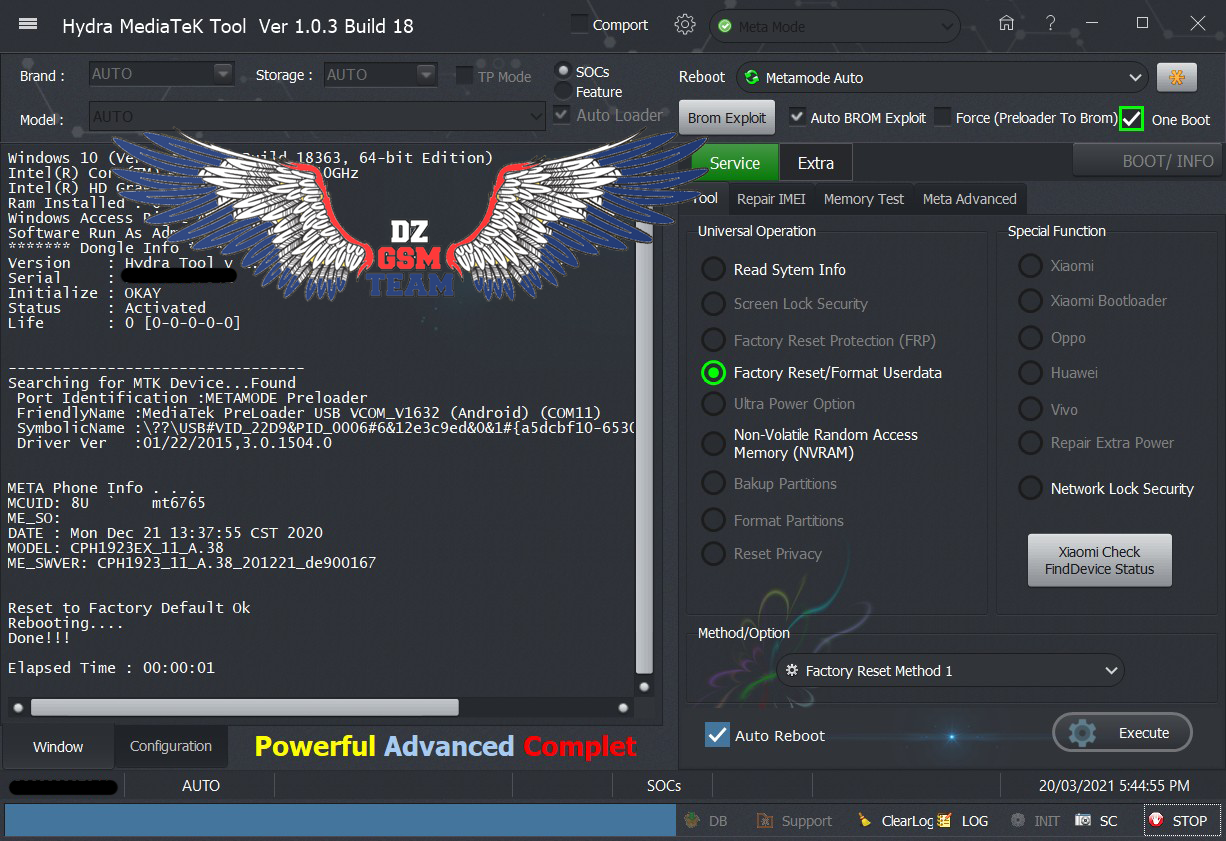 Code: ---------------------------------
Searching for MTK Device...Found
Port Identification :METAMODE Preloader
FriendlyName :MediaTek PreLoader USB VCOM_V1632 (Android) (COM11)
SymbolicName :\??\USB#VID_22D9&PID_0006#6&12e3c9ed&0&1#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :01/22/2015,3.0.1504.0
META Phone Info . . .
MCUID: 8U ` mt6765
ME_SO:
DATE : Mon Dec 21 13:37:55 CST 2020
MODEL: CPH1923EX_11_A.38
ME_SWVER: CPH1923_11_A.38_201221_de900167
Reset to Factory Default Ok
Rebooting....
Done!!!
Elapsed Time : 00:00:01  |
 |
| The Following User Says Thank You to Gsm-Ahmed For This Useful Post: |
| | #1500 (permalink) |
| No Life Poster      Join Date: Jan 2020 Location: Algeria
Posts: 814
Member: 2944109 Status: Offline Thanks Meter: 656 | Wiko Tommy 3 FRP Remove Wiko Tommy 3 FRP Remove Successfully done by Hydra Tool 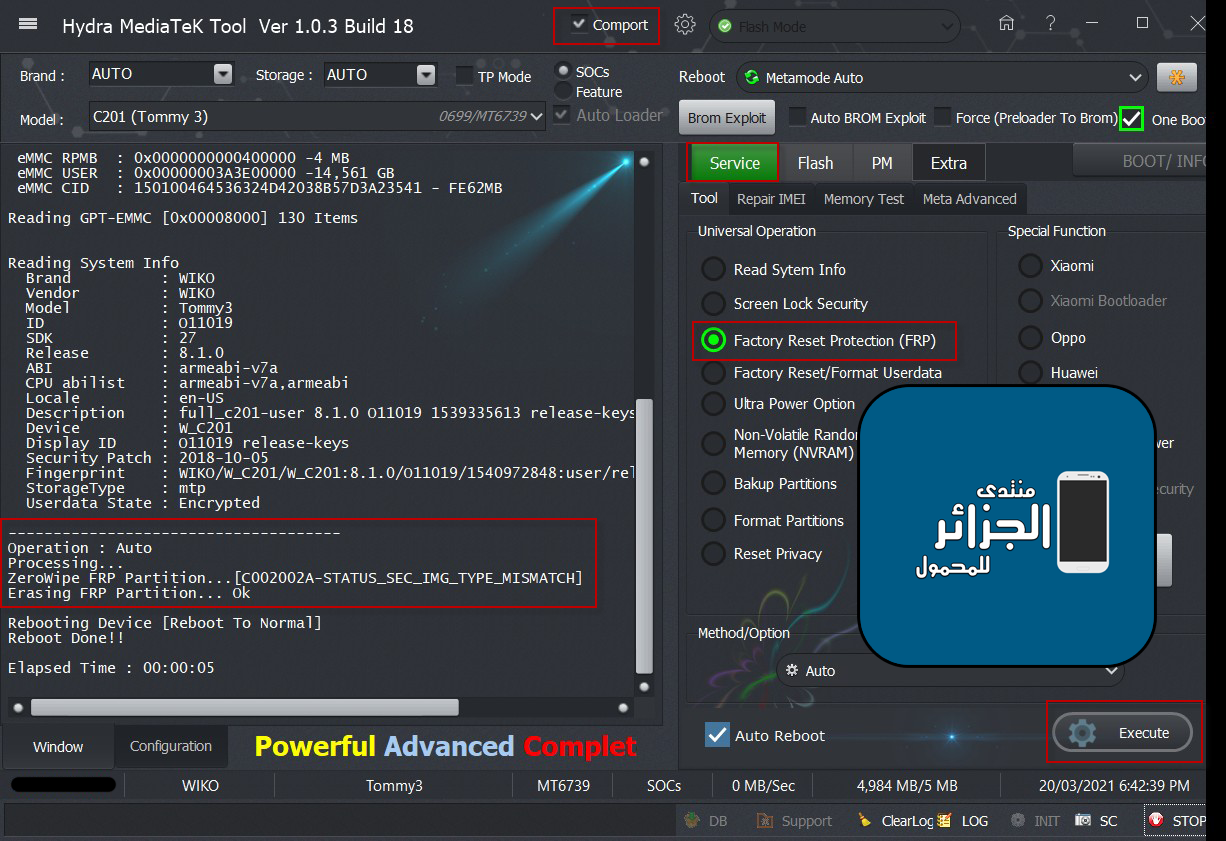 Code: =====================================
Searching for MTK Device...Found
Port Identification :Flashmode Preloader
FriendlyName :MediaTek PreLoader USB VCOM (Android) (COM4)
SymbolicName :\??\USB#VID_0E8D&PID_2000#6&12e3c9ed&0&1#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :01/22/2015,3.0.1504.0
Reading Device UniqueID, RAM and Flash Chip Info...
UNIQUE ID : F67CAE3861FF9F9B8CB719C4559E0C8B
ERAM Size : 0x0000000000040000 -256 KB
IRAM Size : 0x0000000040000000 -1024 MB
eMMC BOOT1 : 0x0000000000400000 -4 MB
eMMC BOOT2 : 0x0000000000400000 -4 MB
eMMC RPMB : 0x0000000000400000 -4 MB
eMMC USER : 0x00000003A3E00000 -14,561 GB
eMMC CID : 150100464536324D42038B57D3A23541 - FE62MB
Reading GPT-EMMC [0x00008000] 130 Items
Reading System Info
Brand : WIKO
Vendor : WIKO
Model : Tommy3
ID : O11019
SDK : 27
Release : 8.1.0
ABI : armeabi-v7a
CPU abilist : armeabi-v7a,armeabi
Locale : en-US
Description : full_c201-user 8.1.0 O11019 1539335613 release-keys
Device : W_C201
Display ID : O11019 release-keys
Security Patch : 2018-10-05
Fingerprint : WIKO/W_C201/W_C201:8.1.0/O11019/1540972848:user/release-keys
StorageType : mtp
Userdata State : Encrypted
-------------------------------------
Operation : Auto
Processing...
ZeroWipe FRP Partition...[C002002A-STATUS_SEC_IMG_TYPE_MISMATCH]
Erasing FRP Partition... Ok
Rebooting Device [Reboot To Normal]
Reboot Done!!
Elapsed Time : 00:00:05 |
 |
| The Following User Says Thank You to Gsm-Ahmed For This Useful Post: |
 |
| Bookmarks |
| |
|
|