



  |
 |
|
Welcome to the GSM-Forum forums. You are currently viewing our boards as a guest which gives you limited access to view most discussions and access our other features. Only registered members may post questions, contact other members or search our database of over 8 million posts. Registration is fast, simple and absolutely free so please - Click to REGISTER! If you have any problems with the registration process or your account login, please contact contact us . |
| |||||||
| Register | FAQ | Donate | Forum Rules | Root any Device | ★iPhone Unlock★ | ★ Direct Codes ★ | Direct Unlock Source |
 |
| | LinkBack | Thread Tools | Display Modes |
| | #2821 (permalink) | |
| No Life Poster       Join Date: Feb 2012 Age: 39
Posts: 1,395
Member: 1724862 Status: Offline Thanks Meter: 448 | Vivo V11 Pro Remove Screen Lock And Remove Frp With by Hydra  Quote:
| |
 |
| | #2822 (permalink) | |
| No Life Poster       Join Date: Feb 2012 Age: 39
Posts: 1,395
Member: 1724862 Status: Offline Thanks Meter: 448 | Redmi 5 Plus (vince) Edl Frp Remove With by Hydra Redmi 5 Plus (vince) Edl Frp Remove With by Hydra 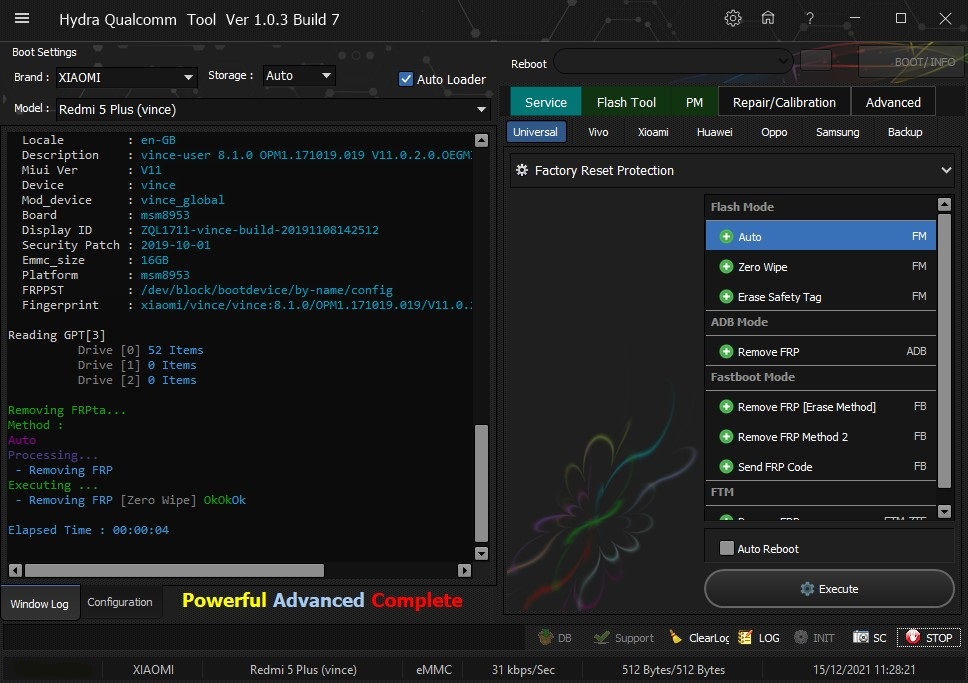 Quote:
| |
 |
| | #2823 (permalink) | |
| No Life Poster       Join Date: Feb 2012 Age: 39
Posts: 1,395
Member: 1724862 Status: Offline Thanks Meter: 448 | Redmi 5A (riva) Factory Reset One click With by Hydra Redmi 5A (riva) Factory Reset One click With by Hydra 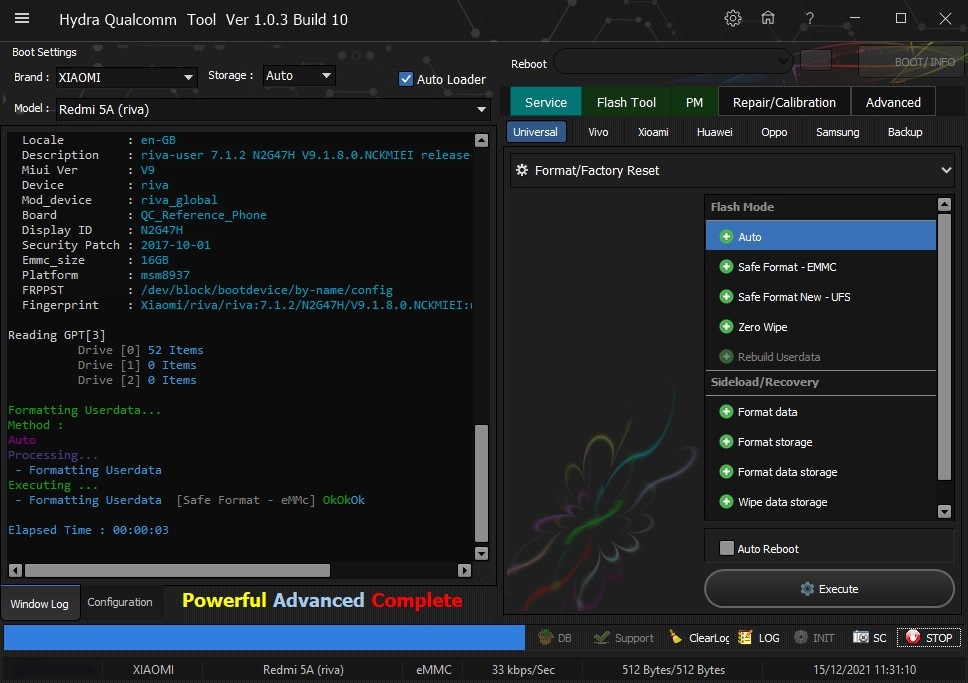 Quote:
| |
 |
| | #2824 (permalink) | |
| No Life Poster       Join Date: Feb 2012 Age: 39
Posts: 1,395
Member: 1724862 Status: Offline Thanks Meter: 448 | Redmi Note 9 (merlin) Bootloader Unlock With by Hydra Redmi Note 9 (merlin) Bootloader Unlock With by Hydra 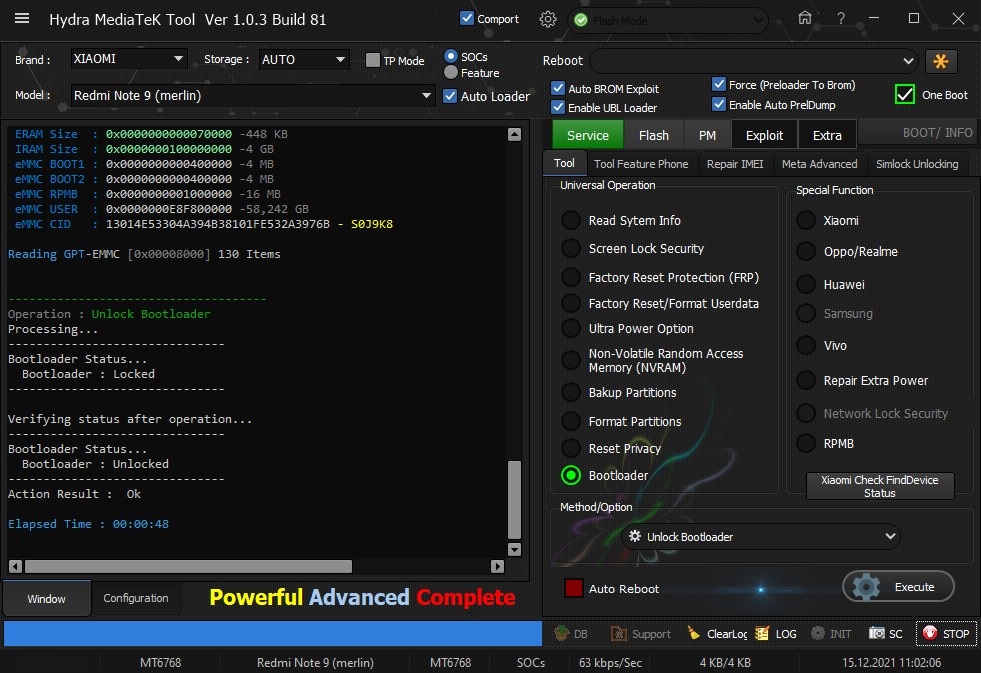 Quote:
| |
 |
| | #2826 (permalink) | |
| No Life Poster       Join Date: Feb 2012 Age: 39
Posts: 1,395
Member: 1724862 Status: Offline Thanks Meter: 448 | Oppo F1s Plus Read Screen Security With by Hydra Oppo F1s Plus Read Screen Security With by Hydra 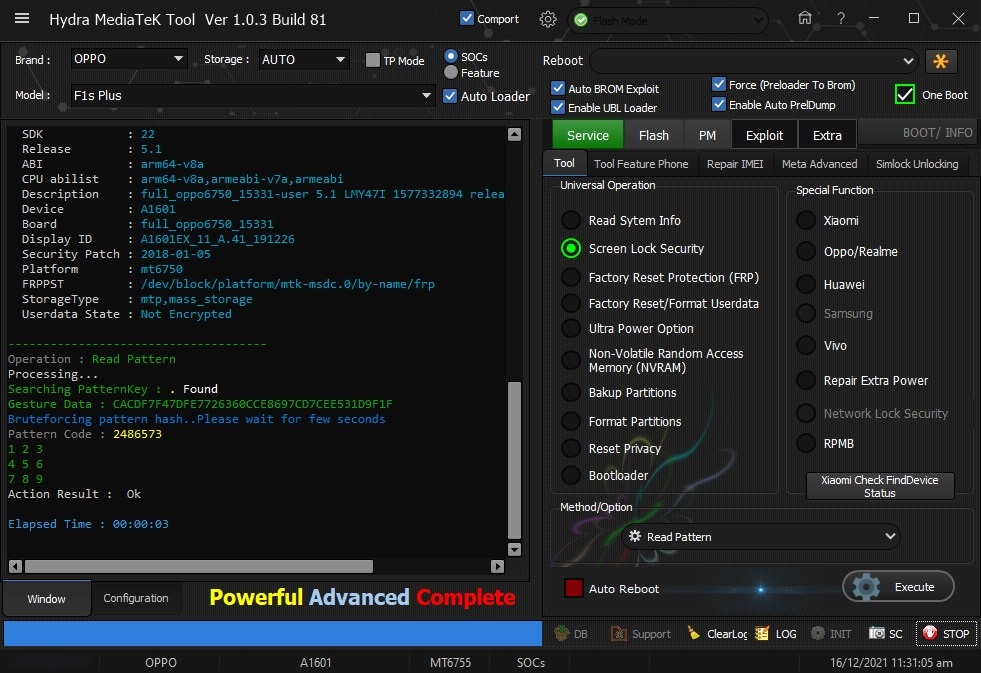 Quote:
| |
 |
| | #2827 (permalink) | |
| No Life Poster       Join Date: Feb 2012 Age: 39
Posts: 1,395
Member: 1724862 Status: Offline Thanks Meter: 448 | Redmi Note 9C NFC (angelican) Bootloader Unlock With by Hydra Redmi Note 9C NFC (angelican) Bootloader Unlock With by Hydra 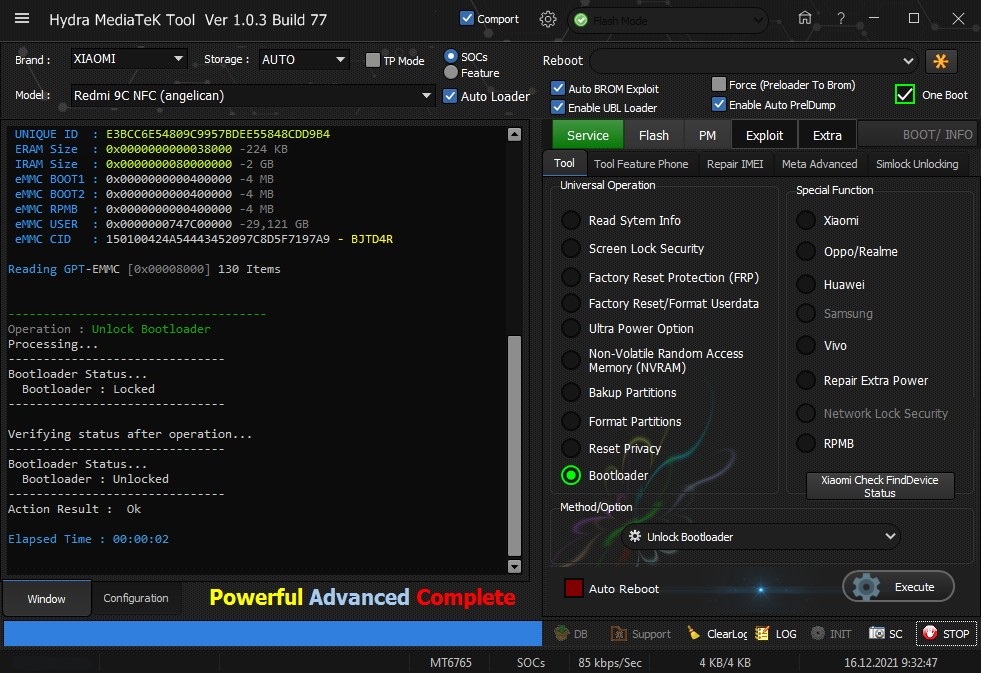 Quote:
| |
 |
| | #2828 (permalink) | |
| No Life Poster       Join Date: Feb 2012 Age: 39
Posts: 1,395
Member: 1724862 Status: Offline Thanks Meter: 448 | Oppo A71 (2018) CPH1801 Edl Format Userdata One Click With by Hydra Oppo A71 (2018) CPH1801 Edl Format Userdata One Click With by Hydra 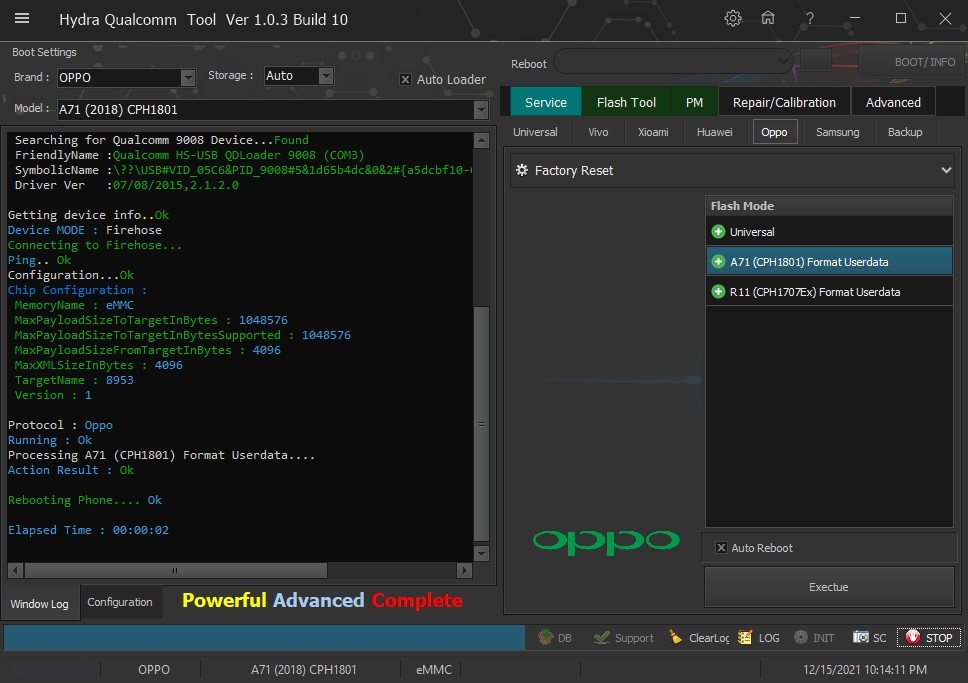 Quote:
| |
 |
| | #2829 (permalink) | |
| No Life Poster       Join Date: Feb 2012 Age: 39
Posts: 1,395
Member: 1724862 Status: Offline Thanks Meter: 448 | Redmi 7A (pine) Edl Frp Remove With by Hydra Redmi 7A (pine) Edl Frp Remove With by Hydra 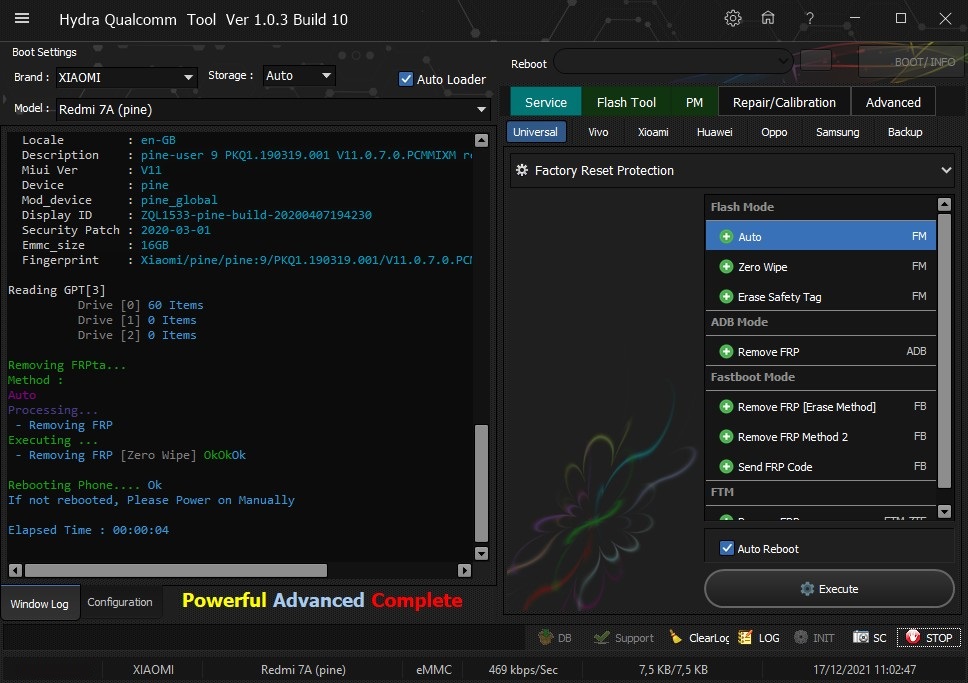 Quote:
| |
 |
| | #2830 (permalink) | |
| No Life Poster       Join Date: Feb 2012 Age: 39
Posts: 1,395
Member: 1724862 Status: Offline Thanks Meter: 448 | Redmi Note 8 Pro (begonia) Bootloader Unlock With By hydra Redmi Note 8 Pro (begonia) Bootloader Unlock With By hydra 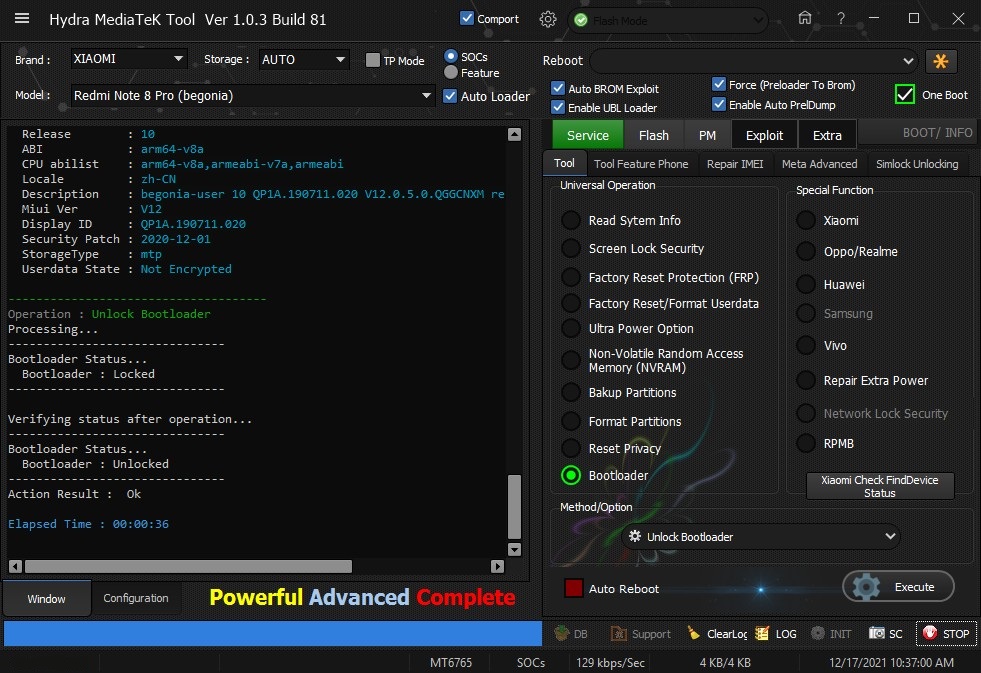 Quote:
| |
 |
| | #2831 (permalink) | |
| No Life Poster       Join Date: Feb 2012 Age: 39
Posts: 1,395
Member: 1724862 Status: Offline Thanks Meter: 448 | Huawei Y7 2019 (DUB-LX3) Edl Flashıng Fix Sound Problem With by Hydra Huawei Y7 2019 (DUB-LX3) Edl Flashıng Fix Sound Problem With by Hydra 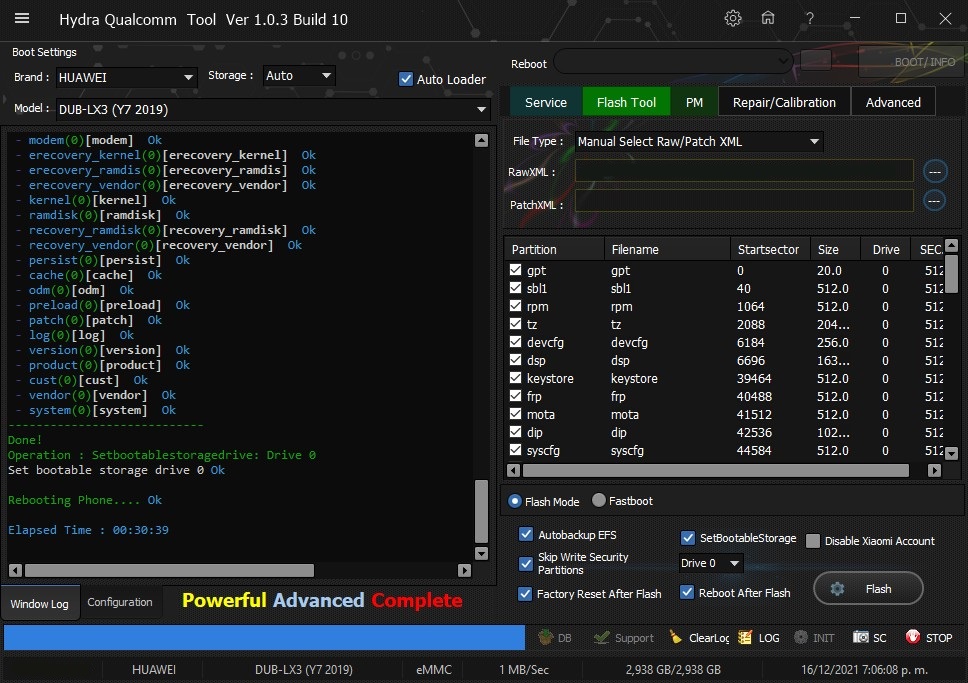 Quote:
| |
 |
| The Following User Says Thank You to ceza031 For This Useful Post: |
| | #2832 (permalink) | |
| No Life Poster       Join Date: Feb 2012 Age: 39
Posts: 1,395
Member: 1724862 Status: Offline Thanks Meter: 448 | Vivo V7 (1718) Edl Frp Remove With by Hydra Vivo V7 (1718) Edl Frp Remove With by Hydra 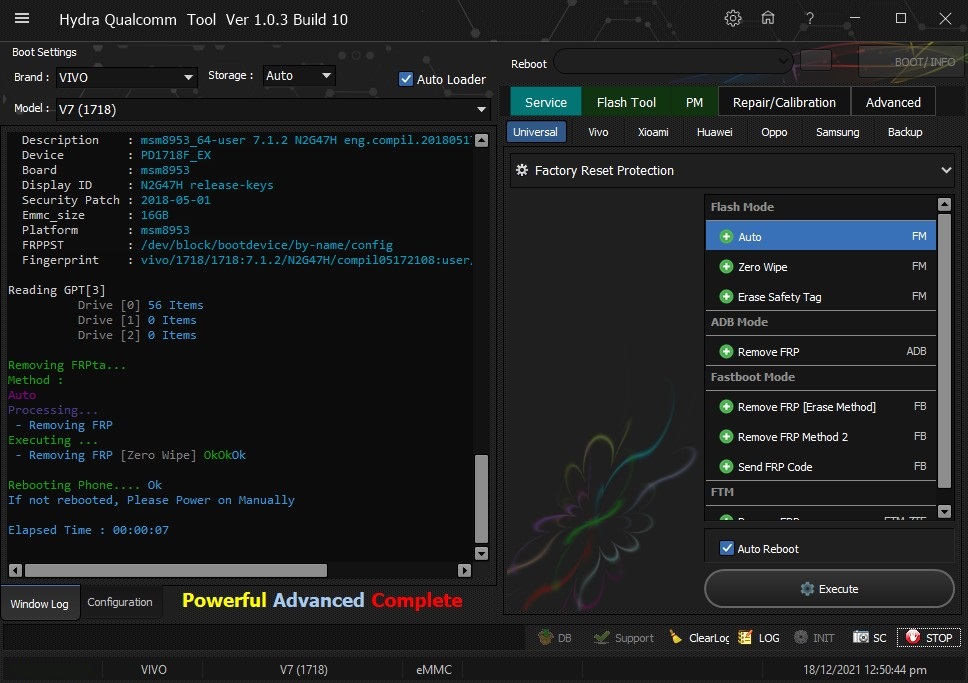 Quote:
| |
 |
| | #2833 (permalink) | |
| No Life Poster       Join Date: Feb 2012 Age: 39
Posts: 1,395
Member: 1724862 Status: Offline Thanks Meter: 448 | Redmi 9A (dandelion) Bootloader Unlock With by Hydra Redmi 9A (dandelion) Bootloader Unlock With by Hydra 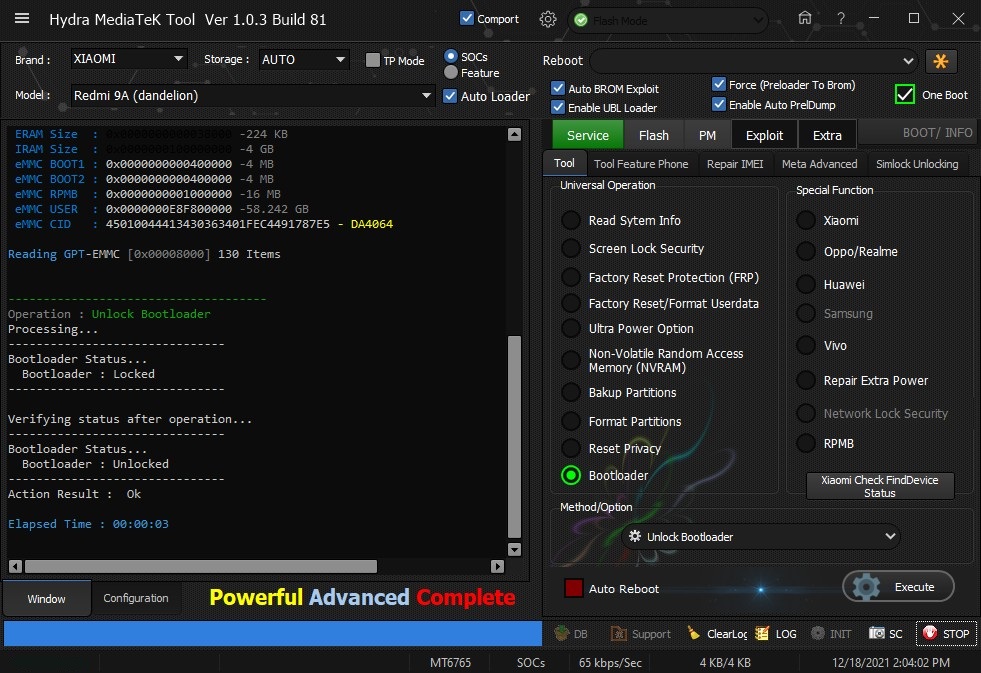 Quote:
| |
 |
| | #2834 (permalink) | |
| No Life Poster       Join Date: Feb 2012 Age: 39
Posts: 1,395
Member: 1724862 Status: Offline Thanks Meter: 448 | Vivo Y12s (PD2036F) Remove Screen Lock &Remove Frp One Click With by Hydra Vivo Y12s (PD2036F) Remove Screen Lock &Remove Frp One Click With by Hydra 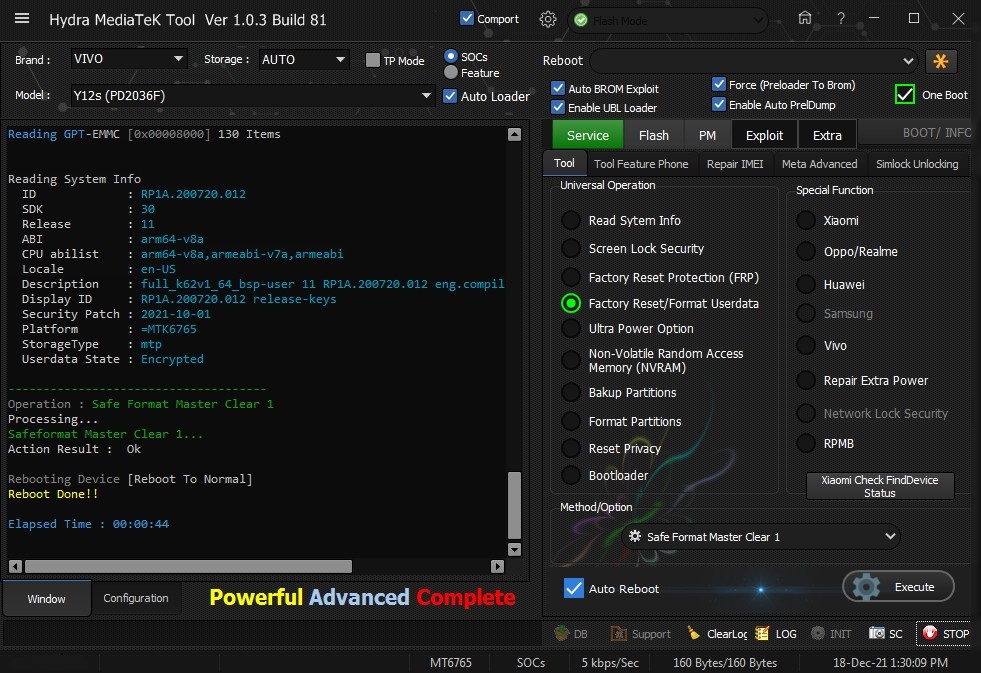 Quote:
| |
 |
| | #2835 (permalink) | |
| No Life Poster       Join Date: Feb 2012 Age: 39
Posts: 1,395
Member: 1724862 Status: Offline Thanks Meter: 448 | Huawei ATU-L22 (Y6 2018) Edl Frp Remove With by Hydra Huawei ATU-L22 (Y6 2018) Edl Frp Remove With by Hydra  Quote:
| |
 |
 |
| Bookmarks |
| |
|
|