



  |
 |
|
Welcome to the GSM-Forum forums. You are currently viewing our boards as a guest which gives you limited access to view most discussions and access our other features. Only registered members may post questions, contact other members or search our database of over 8 million posts. Registration is fast, simple and absolutely free so please - Click to REGISTER! If you have any problems with the registration process or your account login, please contact contact us . |
| |||||||
| Register | FAQ | Donate | Forum Rules | Root any Device | ★iPhone Unlock★ | ★ Direct Codes ★ | Direct Unlock Source |
 |
| | LinkBack | Thread Tools | Display Modes |
| | #31 (permalink) | |
| Product Supporter    Join Date: Dec 2016
Posts: 2,106
Member: 2665389 Status: Offline Thanks Meter: 2,342 | Quote:
The RPMB (Replay Protected Memory Block) partition is a partition with security features in eMMC. When eMMC writes data to RPMB, it will verify the validity of the data. Only the specified Host can write them. When reading data, it also provides a signature mechanism to ensure that the data read by the Host is the internal RPMB data. It is not data forged by an attacker. In practical applications, RPMB is generally used to store data that should prevent illegal manipulation, such as public keys and serial numbers related to fingerprint payments on mobile phones. RPMB can authenticate write operations, but reading does not require authentication. Anyone can perform read operations. Therefore, data stored in RPMB is generally encrypted before being stored. Playback protection principle: For products using eMMC, during production on the production line, a unique 256-bit secure key will be generated for each product, which will be recorded in the OTP area of eMMC (the area that can only be recorded once), and the Host is in the secure area (ex: TEE) will also retain the secure key. Within eMMC, there is also an RPMB write counter. Every time RPMB performs a legal write operation, the write counter will automatically increment by one. By applying Secure Key and Write Counter, RMBB can perform Replay Protect for data reading and writing. 1. Reading RPMB data The RPMB data reading process is as follows:  1) The host initiates a request to read RPMB from eMMC and at the same time generates a 16-byte random number and sends it to eMMC. 2) eMMC reads the requested data from the RPMB and uses the secure key to use the SHA-256 HMAC (hash message verification code) algorithm to calculate the signature after the data read and the received random number are joined. Then eMMC sends the read data, the received random number, and the calculated signature to the Host. 3) Once the Host receives the RPMB data, the random number and the signature, it first compares whether the random number is consistent with the one sent by itself. If consistent, use the same strong key to combine the data and the random number using the HMAC SHA-256 algorithm Signature: If the signature is consistent with the signature sent by eMMC, then the data can be determined to be the correct data read from the RPMB, not the data spoofed by the attacker. Through the read process mentioned above, it can be ensured that the Host can read the RPMB data correctly. 2. Write RPMB data The RPMB data writing process is as follows: 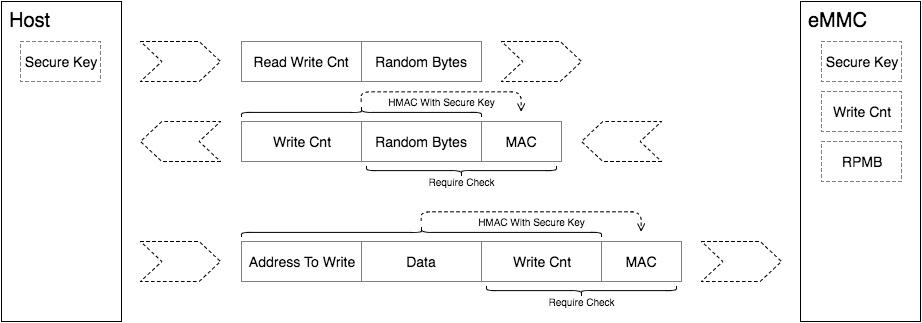 1) The host reads the RPMB write counter according to the above data reading process. 2) The host splices the data to be written with the write counter and calculates the signature, and then sends the data, the write counter and the signature to eMMC. After eMMC receives the data, it first checks whether the write counter is the same as the current value. If it is the same, then sign the combination of the data and the write counter, and then compare it with the signature sent by the host. If the signatures are the same, authentication is passed and the data is written to the RPMB. Through the above writing process, it can be ensured that the RPMB will not be tampered with illegally. BR | |
 |
| The Following 3 Users Say Thank You to Franky_36 For This Useful Post: |
| | #32 (permalink) |
| No Life Poster      | Quote: Sent from my M2101K7AG using Tapatalk |
 |
| The Following 2 Users Say Thank You to otherboy123 For This Useful Post: |
| | #34 (permalink) |
| Product Supporter    Join Date: Dec 2016
Posts: 2,106
Member: 2665389 Status: Offline Thanks Meter: 2,342 | Hi, click on this link and see if there is a seller from your country, if not, contact the amt dongle product manager and he will give you the solution, thank you very much. https://forum.gsmhosting.com/vbb/f10...-list-2884734/ BR |
 |
| The Following User Says Thank You to Franky_36 For This Useful Post: |
| | #35 (permalink) |
| Junior Member   Join Date: Dec 2017
Posts: 27
Member: 2788932 Status: Offline Thanks Meter: 3 | Thank you very much ATM has unlocked redmi 9A today ------------ Sending certificate file... Sending usb control data... Dumping Bloader info from sram... ● Chipset MT6765 {8A00_CA00}(Helio P35) Sending download agent... Executing download agent... Wiat for 1st DA sync cahr... Successfully received DA sync cahr Setup device enviroment... Setup device parametres... Successfully received 1nd DA sync signal Start init ext_ram... Booting DA and get RamInfo... ● SRAM Type:None(Size:224,00KB) ● DRAM Type:GENERAL_DRAM(Size:2,00GB) Sync with DA... ● Storage eMMC ===== wait for DA H/W detection report ===== ● CID 450100444134303332015F4D83134751 ● eMMCID DA4032 ● Boot1 4,00MB ● Boot1 4,00MB ● Rpmb 16,00MB ● Userarea 29,12GB Decrypt Secure bootloader data Bootloader Unlock Done Rebooting device... Done operation finished in : [00:min:20:sec] Log file saved to : C:/AMT-Dongle/AMT/AMT/Data/Logs/Log_Info_2021_08_17_11_22_38.txt |
 |
| The Following 2 Users Say Thank You to Flamastermaster For This Useful Post: |
 |
| Bookmarks |
| |
|
|