



  |
 |
|
Welcome to the GSM-Forum forums. You are currently viewing our boards as a guest which gives you limited access to view most discussions and access our other features. Only registered members may post questions, contact other members or search our database of over 8 million posts. Registration is fast, simple and absolutely free so please - Click to REGISTER! If you have any problems with the registration process or your account login, please contact contact us . |
| |||||||
| Register | FAQ | Donate | Forum Rules | Root any Device | ★iPhone Unlock★ | ★ Direct Codes ★ | Direct Unlock Source |
 |
| | LinkBack | Thread Tools | Display Modes |
| | #1 (permalink) |
| No Life Poster      Join Date: May 2002 Location: dont ask!
Posts: 694
Member: 12411 Status: Offline Sonork: 100.113572 Thanks Meter: 813 | Bugs on mxkey's latest version on UFSx interface 1. good and working N5000 on hand for test 2. universal cable 3. jaf(clone) interface 4. ufsx(clone) interface am using same computer, same cable and same working unit first bus check with ufs interface but if i try to scan the unit, mxkey does detect it with ufsx interface ufsx scan info: Code: Phone Type: RM-362 (Nokia 5000d-2) SW Version: V 03.50 11-04-08 RM-362 (c) Nokia Imei plain: 35692403411787-0 Product Code: 0559348 Cellular System: GSM ASIC ID: 0x3162, type: 11 Ppm Id: T Language Pack: - not available. Imei net: 35692403411787 Version: SIMLOCK SERVER Provider: ALL Operator, Country: - Counter: 0/3, 0/10 CONFIG_DATA: 0010100000000000 PROFILE_BITS: 800000000003000B BLOCK 1: 1.OPEN 2.OPEN 3.OPEN 4.OPEN 5.OPEN BLOCK 2: 1.OPEN 2.OPEN 3.OPEN 4.OPEN 5.OPEN BLOCK 3: 1.OPEN 2.OPEN 3.OPEN 4.OPEN 5.OPEN BLOCK 4: 1.OPEN 2.OPEN 3.OPEN 4.OPEN 5.OPEN BLOCK 5: 1.OPEN 2.OPEN 3.OPEN 4.OPEN 5.OPEN BLOCK 6: 1.OPEN 2.OPEN 3.OPEN 4.OPEN 5.OPEN BLOCK 7: 1.OPEN 2.OPEN 3.OPEN 4.OPEN 5.OPEN jaf log info: Code: Using device: J.A.F, FW ver: 01.B2 Library version: 1.0.0.7705(18-02-2010), 1.0.0.12217(18-02-2010) ASIC ID: 0x3162 [UPP_8M ver: 6.2] SecondaryBoot: u3_2nd.fia [DCT4] version: 4.79.0 revision: 0.7 size: 0x9D8 Supported Ids: 3040, 2292, 2293, 3162, 3166, 3168 FlashID0: 0020 883C [ST ] page size: 128 K type: NOR area: 01000000-01FFFFFF FlashID1: 0000 0001 [unused/removed] ExtBUSC: AD7E B61B 00FF 1040 0000 0000 0000 0000 Algorithm: u3_intel.fia [DCT4 ALGORITHM] version: 4.80.0 revision: 0.7 size: 0x5720 Supported Ids: 3040, 2292, 2293, 3162, 3166, 3168 Performing Flash Authentication ...OK UEM ID: 009A158C:DA3BDA66 ASIC type: 11 UEM Imei: 35692403411787 Phone Type: RM-362 (Nokia 5000d-2) SW Version: V 03.50 11-04-08 RM-362 (c) Nokia Imei plain: 35692403411787-0 Imei OTP: 35692403411787 Product Code: 0559348 Cellular System: GSM ASIC ID: 0x3162, type: 11 Ppm Id: T Language Pack: - not available. Imei net: 35692403411787 Version: SIMLOCK SERVER Provider: ALL Operator, Country: - Counter: 0/3, 0/10 CONFIG_DATA: 0010100000000000 PROFILE_BITS: 800000000003000B BLOCK 1: 1.OPEN 2.OPEN 3.OPEN 4.OPEN 5.OPEN BLOCK 2: 1.OPEN 2.OPEN 3.OPEN 4.OPEN 5.OPEN BLOCK 3: 1.OPEN 2.OPEN 3.OPEN 4.OPEN 5.OPEN BLOCK 4: 1.OPEN 2.OPEN 3.OPEN 4.OPEN 5.OPEN BLOCK 5: 1.OPEN 2.OPEN 3.OPEN 4.OPEN 5.OPEN BLOCK 6: 1.OPEN 2.OPEN 3.OPEN 4.OPEN 5.OPEN BLOCK 7: 1.OPEN 2.OPEN 3.OPEN 4.OPEN 5.OPEN RPL saved to "C:\mobileEx\3.3\data\backup\35692403411787_1266659349_BACK.RPL" so there for i conclude it really has a bug on DCT4 flashing and unlocking dct4 with patching if you use UFSx interface.. i hope mr.alim hape fix this one.. br freddy www.gsmph.com |
 |
| The Following 11 Users Say Thank You to fred For This Useful Post: |
| | #5 (permalink) | |
| No Life Poster      Join Date: May 2002 Location: dont ask!
Posts: 694
Member: 12411 Status: Offline Sonork: 100.113572 Thanks Meter: 813 | @ all i just want to correct my self on my first post Quote:
br freddy | |
 |
| | #6 (permalink) |
| Freak Poster     Join Date: May 2007 Location: BetaMax Tester
Posts: 173
Member: 516470 Status: Offline Thanks Meter: 70 | Same here... Unit: Nokia 1680c Upgrade version/Flashing Code: Using device: UFS_USB V2.8 (c) SarasSoft 2007. Library version: 1.0.0.7705(18-02-2010), 1.0.0.12217(18-02-2010) ASIC ID: 0x3162 [UPP_8M ver: 6.2] SecondaryBoot: u3_2nd.fia [DCT4] version: 4.76.0 revision: 0.7 size: 0x9A8 Supported Ids: 3040, 2292, 2293, 3162, 3166, 3168 FlashID0: 0001 317E [AMD S29NS256P,256 Mbits] page size: 128 K type: NOR area: 01000000-02FFFFFF FlashID1: 0000 0001 [unused/removed] ExtBUSC: AD7E B61B 00FF 1040 0000 0000 0000 0000 Algorithm: u3_amd.fia [DCT4 ALGORITHM] version: 4.76.0 revision: 0.7 size: 0x78C0 Supported Ids: 3040, 2292, 2293, 3162, 3166, 3168 Performing Flash Authentication ...OK UEM ID: 00949EAA:DA3BDA66 ASIC type: 11 UEM Imei: 35640902986*** Flash Imei: 35640902986*** RPL saved to "C:\mobileEx\3.3\data\backup\RPL\35640902986***_BACK.rpl" Processing file: rm394__05.61.mcusw as MCU [DCT4,DCT4 ALGORITHM] size: 10.18 MB Supported Ids: 3160, 3161, 3162, 3164, 3166 ASIC ID: 0x3162 [UPP_8M ver: 6.2] SecondaryBoot: u3_2nd.fia [DCT4] version: 4.76.0 revision: 0.7 size: 0x9A8 Supported Ids: 3040, 2292, 2293, 3162, 3166, 3168 FlashID0: 0001 317E [AMD S29NS256P,256 Mbits] page size: 128 K type: NOR area: 01000000-02FFFFFF - COMBO FLASH ExtBUSC: AD7E B61B 00FF 1040 0000 0000 0000 0000 Algorithm: u3_amd.fia [DCT4 ALGORITHM] version: 4.76.0 revision: 0.7 size: 0x78C0 Supported Ids: 3040, 2292, 2293, 3162, 3166, 3168 Performing Flash Authentication ...OK UEM ID: 00949EAA:3B8ADA60 Area [01000000-0101FFFF] erased in 0.437 s Area [01020000-01C3FFFF] erased in 53.656 s Flash programming ... Programming completed in 3 min 40.016 s File Processed in 4 min 42.937 s Processing file: rm394__05.61.image_el as CNT [DCT4,DCT4 ALGORITHM] page size: 128 K size: 4.13 MB Supported Ids: 3160, 3161, 3162, 3164, 3166 ASIC ID: 0x3162 [UPP_8M ver: 6.2] SecondaryBoot: u3_2nd.fia [DCT4] version: 4.76.0 revision: 0.7 size: 0x9A8 Supported Ids: 3040, 2292, 2293, 3162, 3166, 3168 FlashID0: 0001 317E [AMD S29NS256P,256 Mbits] page size: 128 K type: NOR area: 01000000-02FFFFFF - COMBO FLASH ExtBUSC: AD7E B61A 1BBE 0BE2 7D58 6BE4 DBEE 6514 Algorithm: u3_amd.fia [DCT4 ALGORITHM] version: 4.76.0 revision: 0.7 size: 0x78C0 Supported Ids: 3040, 2292, 2293, 3162, 3166, 3168 Performing Flash Authentication ...OK UEM ID: 00949EAA:C5A4DA78 Area [02000000-02DBFFFF] erased in 1 min 1.265 s Area [02DC0000-02F9FFFF] erased in 10.235 s Converting UCP blocks to 128 K. Flash programming ... Programming completed in 1 min 28.157 s Content extract fail, continue anyway ... File Processed in 5 min 47.516 s Processing file: rm394__05.61.ppm_el as PPM [DCT4,DCT4 ALGORITHM] size: 2.45 MB Supported Ids: 3160, 3161, 3162, 3164, 3166 ASIC ID: 0x3162 [UPP_8M ver: 6.2] SecondaryBoot: u3_2nd.fia [DCT4] version: 4.76.0 revision: 0.7 size: 0x9A8 Supported Ids: 3040, 2292, 2293, 3162, 3166, 3168 BootLoader not responding, mostly RAM problem ! flashing terminated ! Flashing terminated with error(s) in 12 min 5.282 s RX Buffer: F372 |
 |
| | #13 (permalink) |
| Freak Poster     Join Date: May 2007
Posts: 272
Member: 507861 Status: Offline Thanks Meter: 69 | brother try this solution.. mxkey v3.3rev 1.6 dct4 flash fixer download and install.. this files is the exe of 3.3rev1.2...i think the bugs of 3.3rev1.6 is in exe...try and post result logs Using device: UFS_USB V2.8 (c) SarasSoft 2007. Library version: 1.0.0.7548(21-01-2010), 1.0.0.12217(18-02-2010) Rpl backup already exist (C:\mobileEx\3.3\data\backup\35135500417363_BACK.r pl). Processing file: rh3010pra05.340 as MCU [DCT4,DCT4 ALGORITHM] size: 5.48 MB Supported Ids: 0120, 0121, 1120, 1130, 1131, 2142, 2140 ASIC ID: 0x1130 [UPP_8M ver: 3.0 or 3.01 or 3.1] SecondaryBoot: u_2nd.fia [DCT4] version: 4.76.0 revision: 0.7 size: 0x9A0 Supported Ids: 0011, 0010, 0121, 0120, 1120, 1131, 1130, 2141, 2140, 2142, 2151, 1141, 1181, 1015, 1021, 2031, 2030, 3041, 1201, 2201, 2291, 3161, 3160, 3164 FlashID0: 00EC 22F2 [Samsung K8S64158TM,64 Mbits] page size: 64 K type: NOR area: 01000000-017FFFFF FlashID1: 0000 0001 [unused/removed] ExtBUSC: AD7E B61A 1BBE 0BE2 7D58 6BE4 DBEE 6514 Algorithm: u_amd.fia [DCT4 ALGORITHM] version: 4.76.0 revision: 0.7 size: 0x78B8 Supported Ids: 0011, 0010, 0121, 0120, 1120, 1131, 1130, 2141, 2140, 2142, 2151, 1141, 1181, 1015, 1021, 2031, 2030, 3041, 1201, 2201, 2291, 3161, 3160, 3164 Performing Flash Authentication ...OK UEM ID: 008D66BC:C421DA60 Area [01000000-0100FFFF] erased in 0.531 s Area [01010000-0157FFFF] erased in 43.923 s Area [01580000-0168FFFF] erased in 8.392 s Area [01690000-017EFFFF] erased in 10.796 s Area [01E90000-01FEFFFF] erased in 0.420 s Flash programming ... Programming completed in 52.586 s File Processed in 2 min 6.742 s Processing file: rh3010_05.34.ucp_c as CNT [DCT4,DCT4 ALGORITHM] size: 165.37 KB Supported Ids: 0120, 0121, 1120, 1130, 1131, 2142, 2140 ASIC ID: 0x1130 [UPP_8M ver: 3.0 or 3.01 or 3.1] SecondaryBoot: u_2nd.fia [DCT4] version: 4.76.0 revision: 0.7 size: 0x9A0 Supported Ids: 0011, 0010, 0121, 0120, 1120, 1131, 1130, 2141, 2140, 2142, 2151, 1141, 1181, 1015, 1021, 2031, 2030, 3041, 1201, 2201, 2291, 3161, 3160, 3164 FlashID0: 00EC 22F2 [Samsung K8S64158TM,64 Mbits] page size: 64 K type: NOR area: 01000000-017FFFFF FlashID1: 0000 0001 [unused/removed] ExtBUSC: AD7E B61A 1BBE 0BE2 7D58 6BE4 DBEE 6514 Algorithm: u_amd.fia [DCT4 ALGORITHM] version: 4.76.0 revision: 0.7 size: 0x78B8 Supported Ids: 0011, 0010, 0121, 0120, 1120, 1131, 1130, 2141, 2140, 2142, 2151, 1141, 1181, 1015, 1021, 2031, 2030, 3041, 1201, 2201, 2291, 3161, 3160, 3164 Performing Flash Authentication ...OK UEM ID: 008D66BC:C421DA60 Area [01580000-0168FFFF] erased in 8.643 s Flash programming ... Programming completed in 1.452 s Extracting Content Pack, (c) Nokia File Server Content Pack extracted successfully in 2.234 s File Processed in 29.072 s Processing file: rh3010_05.34c as PPM [DCT4,DCT4 ALGORITHM] size: 1.02 MB Supported Ids: 0120, 0121, 1120, 1130, 1131, 2142, 2140 ASIC ID: 0x1130 [UPP_8M ver: 3.0 or 3.01 or 3.1] SecondaryBoot: u_2nd.fia [DCT4] version: 4.76.0 revision: 0.7 size: 0x9A0 Supported Ids: 0011, 0010, 0121, 0120, 1120, 1131, 1130, 2141, 2140, 2142, 2151, 1141, 1181, 1015, 1021, 2031, 2030, 3041, 1201, 2201, 2291, 3161, 3160, 3164 FlashID0: 00EC 22F2 [Samsung K8S64158TM,64 Mbits] page size: 64 K type: NOR area: 01000000-017FFFFF FlashID1: 0000 0001 [unused/removed] ExtBUSC: AD7E B61A 1BBE 0BE2 7D58 6BE4 DBEE 6514 Algorithm: u_amd.fia [DCT4 ALGORITHM] version: 4.76.0 revision: 0.7 size: 0x78B8 Supported Ids: 0011, 0010, 0121, 0120, 1120, 1131, 1130, 2141, 2140, 2142, 2151, 1141, 1181, 1015, 1021, 2031, 2030, 3041, 1201, 2201, 2291, 3161, 3160, 3164 Performing Flash Authentication ...OK UEM ID: 008D66BC:C421DA60 Area [01580000-0168FFFF] erased in 8.612 s Flash programming ... Programming completed in 8.682 s File Processed in 25.486 s Flashing completed in 3 min 2.493 s After Flash Processing ... Updating SIMLOCK ...OK Phone Type: RH-30 (Nokia 3200) SW Version: V 5.34 11-02-05 RH-30 3200 (c) Nokia Imei plain: 35135500417363-2 Imei OTP: 35135500417363 Product Code: 0511998 Cellular System: GSM ASIC ID: 0x1130, type: 2 Ppm Id: C Language Pack: English,German,French,Italian,Dutch,Spanish,Turkis h,Portuguese Imei net: 35135500417363 Version: SIMLOCK SERVER VERSION 40 - Extended number of TDS-6 boxes Provider: ALL Operator, Country: - Counter: 0/3, 0/10 CONFIG_DATA: 0010100000000000 PROFILE_BITS: 0000000000000002 BLOCK 1: 1.OPEN 2.OPEN 3.OPEN 4.OPEN 5.OPEN BLOCK 2: 1.OPEN 2.OPEN 3.OPEN 4.OPEN 5.OPEN BLOCK 3: 1.OPEN 2.OPEN 3.OPEN 4.OPEN 5.OPEN BLOCK 4: 1.OPEN 2.OPEN 3.OPEN 4.OPEN 5.OPEN BLOCK 5: 1.OPEN 2.OPEN 3.OPEN 4.OPEN 5.OPEN BLOCK 6: 1.OPEN 2.OPEN 3.OPEN 4.OPEN 5.OPEN BLOCK 7: 1.OPEN 2.OPEN 3.OPEN 4.OPEN 5.OPEN Total time to process is 3 min 13.098 s 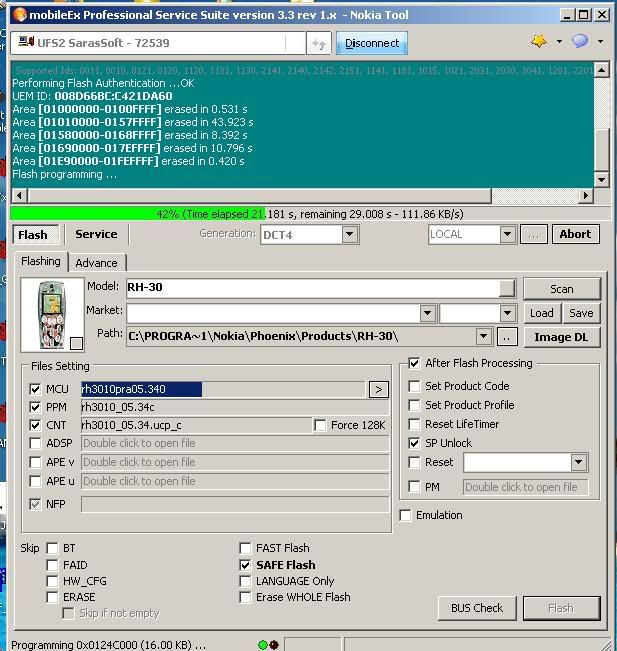 |
 |
| | #14 (permalink) | |
| No Life Poster       Join Date: Jan 2006 Location: HWKBOX,MX-KEY,CYCLONE SL3 ;-)
Posts: 1,273
Member: 217461 Status: Offline Thanks Meter: 150 | Quote:
BR. | |
 |
| | #15 (permalink) |
| Freak Poster     Join Date: Sep 2007
Posts: 423
Member: 594881 Status: Offline Thanks Meter: 77 | i experienced the same problem...... with ufs interface....(no hwk) better to use jaf interface... but if you dont have one... ufs will do.... you just have to be patient... just repeat the procedure over and over until the operation is successful.. tried in 2680s..... but it wud be better if this bug will be fixed..... |
 |
 |
| Bookmarks |
| |
 Similar Threads
Similar Threads | ||||
| Thread | Thread Starter | Forum | Replies | Last Post |
| Problem on upgrade latest version BOX | blue_life1111 | Smart-Clip | 4 | 05-06-2005 09:06 |
|
|