



  |
 |
|
Welcome to the GSM-Forum forums. You are currently viewing our boards as a guest which gives you limited access to view most discussions and access our other features. Only registered members may post questions, contact other members or search our database of over 8 million posts. Registration is fast, simple and absolutely free so please - Click to REGISTER! If you have any problems with the registration process or your account login, please contact contact us . |
| |||||||
| Register | FAQ | Donate | Forum Rules | Root any Device | ★iPhone Unlock★ | ★ Direct Codes ★ | Direct Unlock Source |
 |
| | LinkBack | Thread Tools | Display Modes |
| | #1606 (permalink) | |
| Product Manager      Join Date: Apr 2008 Location: Whitehole throught Blackhole!
Posts: 9,582
Member: 747989 Status: Offline Sonork: 100.1593052 Thanks Meter: 8,623 | Xiaomi Mi 8 Dipper Successfully Flashed By Hydra Tool Xiaomi Mi 8 Dipper Successfully Flashed By Hydra Tool Screen Short:  Logs: Quote:
Dipendra Pathak | |
 |
| | #1607 (permalink) | |
| Product Manager      Join Date: Apr 2008 Location: Whitehole throught Blackhole!
Posts: 9,582
Member: 747989 Status: Offline Sonork: 100.1593052 Thanks Meter: 8,623 | Xiaomi Redmi Note 8 Pro Begonia successfully Flashed by Hydra Tool Xiaomi Redmi Note 8 Pro Begonia successfully Flashed by Hydra Tool Screen Short:  Logs: Quote:
Dipendra Pathak | |
 |
| | #1608 (permalink) | |
| Product Manager      Join Date: Apr 2008 Location: Whitehole throught Blackhole!
Posts: 9,582
Member: 747989 Status: Offline Sonork: 100.1593052 Thanks Meter: 8,623 | Xiaomi Redmi 6 Cereus Removing Mi Account and FRP with Erase method successfully done Xiaomi Redmi 6 Cereus Removing Mi Account and FRP with Erase method successfully done by Hydra Screen Short:  Logs: Quote:
Dipendra Pathak | |
 |
| | #1609 (permalink) | |
| Product Manager      Join Date: Apr 2008 Location: Whitehole throught Blackhole!
Posts: 9,582
Member: 747989 Status: Offline Sonork: 100.1593052 Thanks Meter: 8,623 | Xiaomi Redmi 7A Pine Safe Format user data successfully done by Hydra Tool Xiaomi Redmi 7A Pine Safe Format user data successfully done by Hydra Tool Screen Short:  Logs: Quote:
Dipendra Pathak | |
 |
| | #1610 (permalink) | |
| Product Manager      Join Date: Apr 2008 Location: Whitehole throught Blackhole!
Posts: 9,582
Member: 747989 Status: Offline Sonork: 100.1593052 Thanks Meter: 8,623 | Asus ZB5552KL zero wipe FRP successfully done by Hydra Tool Asus ZB5552KL zero wipe FRP successfully done by Hydra Tool Screen Short:  Logs: Quote:
Dipendra Pathak | |
 |
| The Following User Says Thank You to Dipendra Pathak For This Useful Post: |
| | #1611 (permalink) |
| No Life Poster       Join Date: Jan 2013 Location: gsmhosting Age: 29
Posts: 1,148
Member: 1876736 Status: Offline Thanks Meter: 735 | TECNO BB4k imei repair done Code: ***IMEI REPAIR FUNCTION**** New Method Searching for MTK Device...Found Port Identification :METAMODE BROM FriendlyName :MediaTek USB VCOM (Android) (COM79) SymbolicName :\??\COM79 Driver Ver :01/22/2015,3.0.1504.0 Rebooting Phone into META Mode... Connecting to META Device...Ok Getting Device Information... Brand : TECNO MOBILE LIMITED Product Board : unknown Model : TECNO-BB4k Model Code : TECNO BB4k Android Version : 9 CPU : mt6761 Security Patch : 2020-11-05 ARM CPU : armeabi-v7a Read Information Succes... Loading MDDB From Phone...Ok IMEI1 : 353yyyyyyy IMEI1 : 353yyyyy Writing IMEI 1Ok Writing IMEI 2Ok Done Elapsed Time : 00:00:03 |
 |
| The Following User Says Thank You to sky73 For This Useful Post: |
| | #1612 (permalink) |
| No Life Poster       Join Date: Jan 2013 Location: gsmhosting Age: 29
Posts: 1,148
Member: 1876736 Status: Offline Thanks Meter: 735 | TECNO BB4k imei repair done Code: ***IMEI REPAIR FUNCTION**** New Method Searching for MTK Device...Found Port Identification :METAMODE BROM FriendlyName :MediaTek USB VCOM (Android) (COM79) SymbolicName :\??\COM79 Driver Ver :01/22/2015,3.0.1504.0 Rebooting Phone into META Mode... Connecting to META Device...Ok Getting Device Information... Brand : TECNO MOBILE LIMITED Product Board : unknown Model : TECNO-BB4k Model Code : TECNO BB4k Android Version : 9 CPU : mt6761 Security Patch : 2020-11-05 ARM CPU : armeabi-v7a Read Information Succes... Loading MDDB From Phone...Ok IMEI1 : 353yyyyyyy IMEI1 : 353yyyyy Writing IMEI 1Ok Writing IMEI 2Ok Done Elapsed Time : 00:00:03 |
 |
| The Following User Says Thank You to sky73 For This Useful Post: |
| | #1613 (permalink) | |
| Product Manager      Join Date: Aug 2018 Location: Ukraine / Harkov
Posts: 1,986
Member: 2857401 Status: Offline Thanks Meter: 6,861 | Xiaomi Qualcomm Mi Account Remove Without Relock and BL Locked Xiaomi Qualcomm Mi Account Remove Without Relock and BL Locked Mi Account Remove of Xiaomi Qualcomm devices by EDL Mode, Without any VPN App, No Relocked after Reset, Bootloader locked or locked not matter, Which device emabed auth can direct erase, With this method device will not relocked after factory reset. Video Guide : Quote:
| |
 |
| | #1614 (permalink) |
| No Life Poster      Join Date: Jan 2020 Location: Algeria
Posts: 814
Member: 2944109 Status: Offline Thanks Meter: 656 | Condor Allure A8 (PGN611) Ultra power option Condor Allure A8 (PGN611) Ultra power option 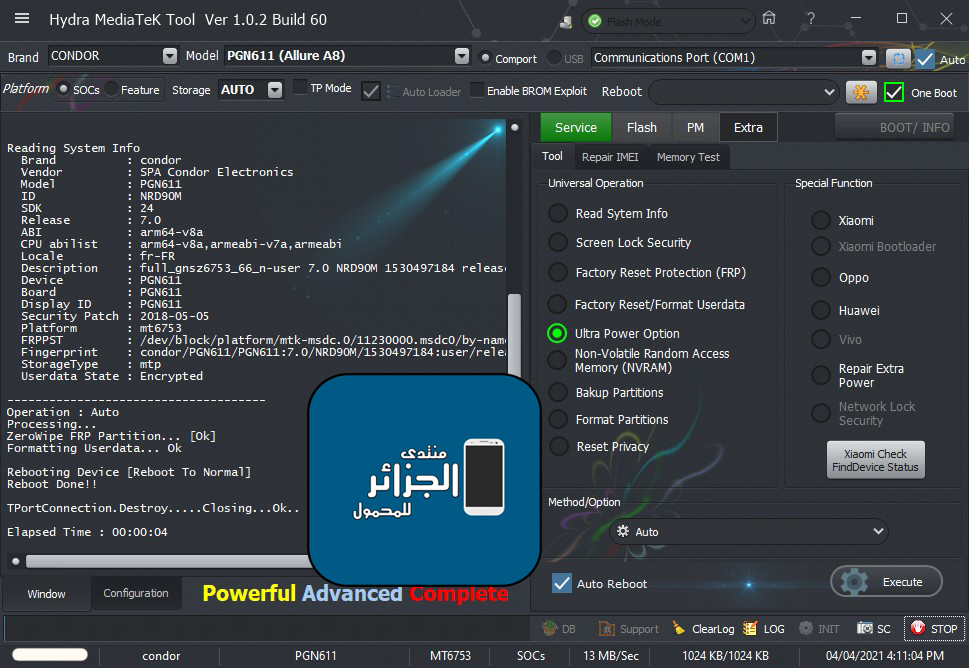 Code: Brand : CONDOR Model : PGN611 (Allure A8) Connection : Flash Mode ===================================== Connection -Please wait... -Found...[COM5] TPortConnection.Create...(COM5)..Opening...Ok Reading System Info Brand : condor Vendor : SPA Condor Electronics Model : PGN611 ID : NRD90M SDK : 24 Release : 7.0 ABI : arm64-v8a CPU abilist : arm64-v8a,armeabi-v7a,armeabi Locale : fr-FR Description : full_gnsz6753_66_n-user 7.0 NRD90M 1530497184 release-keys Device : PGN611 Board : PGN611 Display ID : PGN611 Security Patch : 2018-05-05 Platform : mt6753 FRPPST : /dev/block/platform/mtk-msdc.0/11230000.msdc0/by-name/frp Fingerprint : condor/PGN611/PGN611:7.0/NRD90M/1530497184:user/release-keys StorageType : mtp Userdata State : Encrypted ------------------------------------- Operation : Auto Processing... ZeroWipe FRP Partition... [Ok] Formatting Userdata... Ok Rebooting Device [Reboot To Normal] Reboot Done!! TPortConnection.Destroy.....Closing...Ok.. Elapsed Time : 00:00:04 |
 |
| The Following User Says Thank You to Gsm-Ahmed For This Useful Post: |
| | #1615 (permalink) |
| No Life Poster      Join Date: Jan 2020 Location: Algeria
Posts: 814
Member: 2944109 Status: Offline Thanks Meter: 656 | Condor Griffe G5 (PHQ520) Ultra Power Option Condor Griffe G5 (PHQ520) Ultra Power Option  |
 |
| The Following User Says Thank You to Gsm-Ahmed For This Useful Post: |
| | #1616 (permalink) |
| No Life Poster      Join Date: Jan 2020 Location: Algeria
Posts: 814
Member: 2944109 Status: Offline Thanks Meter: 656 | Huawei Y3II (LUA-U22) Remove Lock Without Data Loss Huawei Y3II (LUA-U22) Remove Lock Without Data Loss 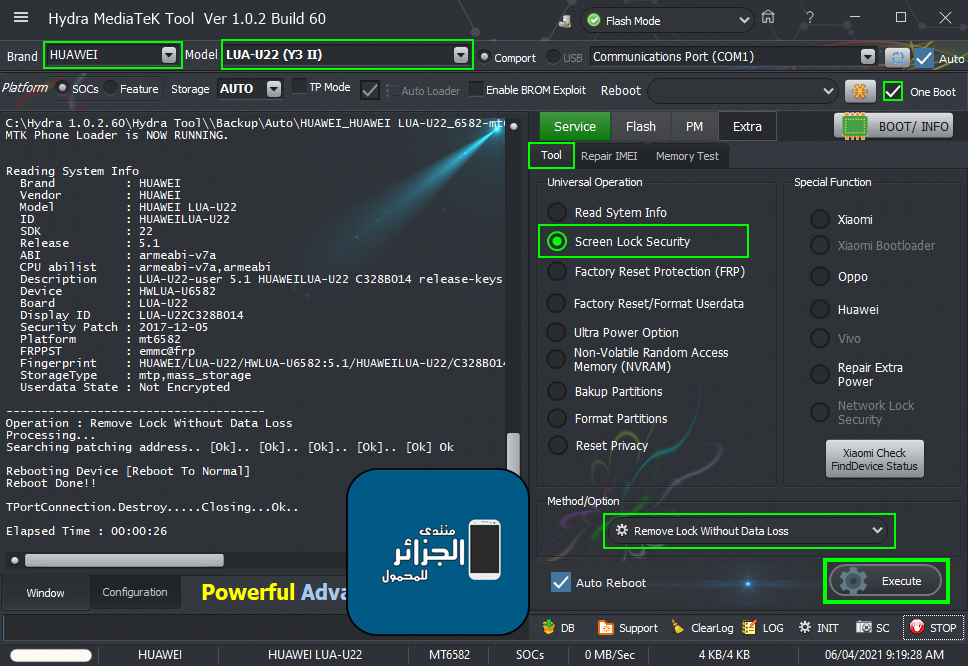 Code: Brand : HUAWEI Model : LUA-U22 (Y3 II) Connection : Flash Mode ===================================== Connection -Please wait... -Found... -PreLoader...[COM4] TPortConnection.Create...(COM4)..Opening...Ok Handshaking...Ok Identifying Hardware ID..... BROM CPUID : 6582 (0000)MT6582[6582] BROM HW_SW_VER : 8A00 CA01 0001 0000 Handshaking... Identifying Hardware ID..... BROM CPUID : 6582 (0000)MT6582[6582] BROM HW_SW_VER : 8A00 CA01 0001 0000 FUSEID : 00000380 SECURE VERSION : FF BL VERSION : 01 BR Secured : 00 Preparing Download Agent.. DA : da_mt6582_lua_u22.bin Agent: MTK_DOWNLOAD_AGENT -HYDRA Ver : MTK_AllInOne_DA_v3.3001.00.00 Init : Loader [1] Sending : Accepted Identifying Protocol... Protocol : Old - eMMC 00000000000000000000 PRMMCCID : 150100464E31324D420649FCCAF27329 Init Configuration Running DA 4.2 on BBID : 0x87 Ok Initializing Loader [2] Sending Loader [2] Accepted Reading Flashchip data.... eMMC BOOT1 : 0x0000000000400000 -4 MB eMMC BOOT2 : 0x0000000000400000 -4 MB eMMC RPMB : 0x0000000000080000 -512 KB eMMC USER : 0x00000001D2000000 -7,281 GB ERAM Size : 0x0000000040000000 -1024 MB IRAM Size : 0x0000000000020000 -128 KB UNICAL RID : 9249709E10A1E3A51962F0A1B4ED300A eMMC CID : 460001154D32314EFC4906422973F2CA Change to HIGH SPEED... 5A Connection -Please wait... -Found...[COM5] Reading Partition Table SIZE[0x000008A0] 23 Items > Done Reading System Info Brand : HUAWEI Vendor : HUAWEI Model : HUAWEI LUA-U22 ID : HUAWEILUA-U22 SDK : 22 Release : 5.1 ABI : armeabi-v7a CPU abilist : armeabi-v7a,armeabi Description : LUA-U22-user 5.1 HUAWEILUA-U22 C328B014 release-keys Device : HWLUA-U6582 Board : LUA-U22 Display ID : LUA-U22C328B014 Security Patch : 2017-12-05 Platform : mt6582 FRPPST : emmc@frp Fingerprint : HUAWEI/LUA-U22/HWLUA-U6582:5.1/HUAWEILUA-U22/C328B014:user/release-keys StorageType : mtp,mass_storage Userdata State : Not Encrypted Autobackup Partitions -PRELOADER[0x00000000] 512 KB -> PRELOADER.bin...Ok -> Renaming Preloader.... preloader_wt96582_s96582aa51.bin Creating Scatter file... C:\Hydra 1.0.2.60\Hydra Tool\\Backup\Auto\HUAWEI_HUAWEI LUA-U22_6582-mt6582-5.1_LUA-U22C328B014_060421091902\MT6582_Android_scatter.txt -NVRAM[0x01000000] 5 MB -> NVRAM.bin...Ok -FRP[0x1DD80000] 1024 KB -> FRP.bin...Ok Done!!! C:\Hydra 1.0.2.60\Hydra Tool\\Backup\Auto\HUAWEI_HUAWEI LUA-U22_6582-mt6582-5.1_LUA-U22C328B014_060421091902 MTK Phone Loader is NOW RUNNING. Reading System Info Brand : HUAWEI Vendor : HUAWEI Model : HUAWEI LUA-U22 ID : HUAWEILUA-U22 SDK : 22 Release : 5.1 ABI : armeabi-v7a CPU abilist : armeabi-v7a,armeabi Description : LUA-U22-user 5.1 HUAWEILUA-U22 C328B014 release-keys Device : HWLUA-U6582 Board : LUA-U22 Display ID : LUA-U22C328B014 Security Patch : 2017-12-05 Platform : mt6582 FRPPST : emmc@frp Fingerprint : HUAWEI/LUA-U22/HWLUA-U6582:5.1/HUAWEILUA-U22/C328B014:user/release-keys StorageType : mtp,mass_storage Userdata State : Not Encrypted ------------------------------------- Operation : Remove Lock Without Data Loss Processing... Searching patching address.. [Ok].. [Ok].. [Ok].. [Ok].. [Ok] Ok Rebooting Device [Reboot To Normal] Reboot Done!! TPortConnection.Destroy.....Closing...Ok.. Elapsed Time : 00:00:26 |
 |
| The Following User Says Thank You to Gsm-Ahmed For This Useful Post: |
| | #1617 (permalink) |
| No Life Poster      Join Date: Jan 2020 Location: Algeria
Posts: 814
Member: 2944109 Status: Offline Thanks Meter: 656 | XIAOMI Redmi Note 8T (wiilow) Remove MiAccount [New Method] XIAOMI Redmi Note 8T (wiilow) Remove MiAccount [New Method] No Need To Flash any File No Need APP Or VPN You Can Factory Your Devices (MiAccount No Back)  |
 |
| The Following User Says Thank You to Gsm-Ahmed For This Useful Post: |
| | #1619 (permalink) | |
| Product Manager      Join Date: Apr 2008 Location: Whitehole throught Blackhole!
Posts: 9,582
Member: 747989 Status: Offline Sonork: 100.1593052 Thanks Meter: 8,623 | Xiaomi Redmi Note 5A UGG disanble Mi Account successfully Removed by Hydra Tool Xiaomi Redmi Note 5A UGG disanble Mi Account successfully Removed by Hydra Tool Screen Short:  Logs: Quote:
Dipendra Pathak | |
 |
| | #1620 (permalink) | |
| Product Manager      Join Date: Apr 2008 Location: Whitehole throught Blackhole!
Posts: 9,582
Member: 747989 Status: Offline Sonork: 100.1593052 Thanks Meter: 8,623 | Xiaomi Redmi 4X Santoni Zero Wipe FRP removed successfully done by Hydra Tool Xiaomi Redmi 4X Santoni Zero Wipe FRP removed successfully done by Hydra Tool Screen Short:  Logs: Quote:
Dipendra Pathak | |
 |
 |
| Bookmarks |
| |
|
|