



  |
 |
|
Welcome to the GSM-Forum forums. You are currently viewing our boards as a guest which gives you limited access to view most discussions and access our other features. Only registered members may post questions, contact other members or search our database of over 8 million posts. Registration is fast, simple and absolutely free so please - Click to REGISTER! If you have any problems with the registration process or your account login, please contact contact us . |
| |||||||
| Register | FAQ | Donate | Forum Rules | Root any Device | ★iPhone Unlock★ | ★ Direct Codes ★ | Direct Unlock Source |
 |
| | LinkBack | Thread Tools | Display Modes |
| | #2776 (permalink) | |
| No Life Poster       Join Date: Feb 2012 Age: 39
Posts: 1,395
Member: 1724862 Status: Offline Thanks Meter: 448 | Redmi 9C (angelica) Bootloader Unlock With by hydra 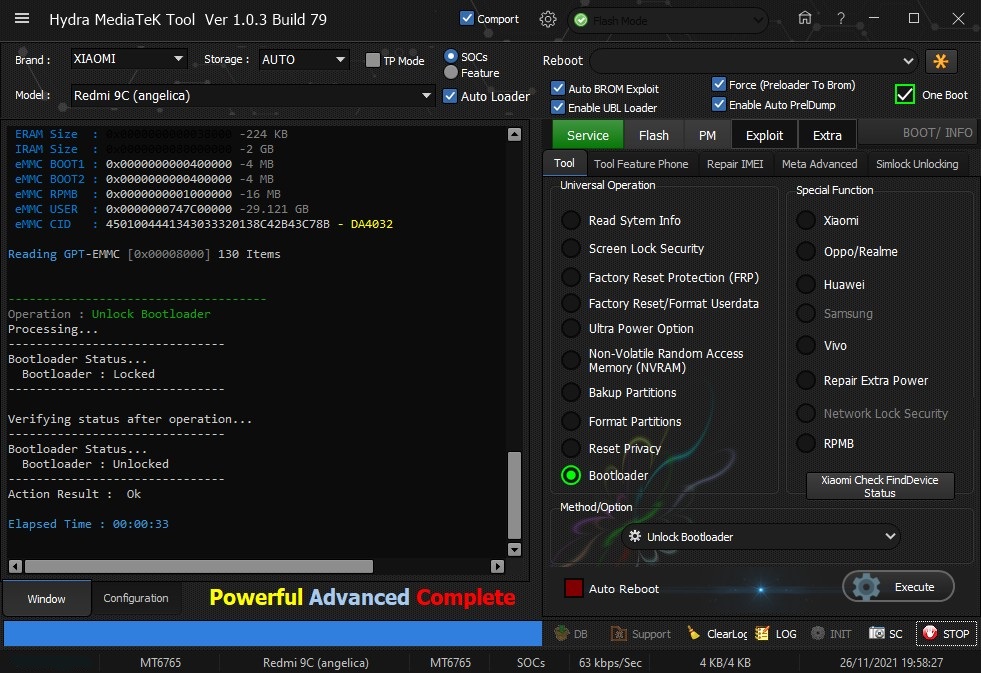 Quote:
| |
 |
| | #2777 (permalink) | |
| No Life Poster       Join Date: Feb 2012 Age: 39
Posts: 1,395
Member: 1724862 Status: Offline Thanks Meter: 448 | Mi A1 (Tissot) Edl Frp Remove done by Hydra 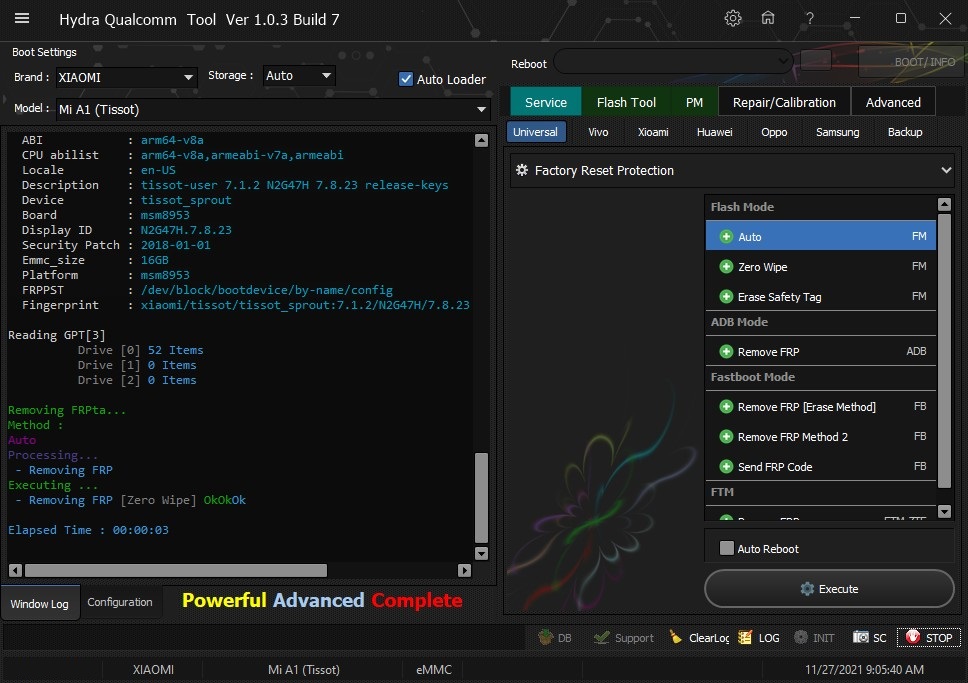 Quote:
| |
 |
| | #2778 (permalink) |
| Freak Poster     | General mobile gm8 d repair on andriod 9 the device, first of all, back up your information, then you need to crack the boot lock of the device, for this, put the device in fastboot mode and enter the fastboot oem unlock-go for unlock bootloader then download twrp and copy to minimal adb folder ****************************/file/f9avc...rpfeb.img/file after flash twrp with this command fastboot flash boot twrp.img know go to twrp by volum up and power formate data yes install magasik and reboot u r rooted know enable diag with command or box repair and reboot don |
 |
| | #2779 (permalink) | |
| No Life Poster       Join Date: Feb 2012 Age: 39
Posts: 1,395
Member: 1724862 Status: Offline Thanks Meter: 448 | Huawei Y7 2019 (DUB-LX1) Fix Sound Problem done With by Hydra Edl FLashıng Huawei Y7 2019 (DUB-LX1) Fix Sound Problem done With by Hydra Edl FLashıng 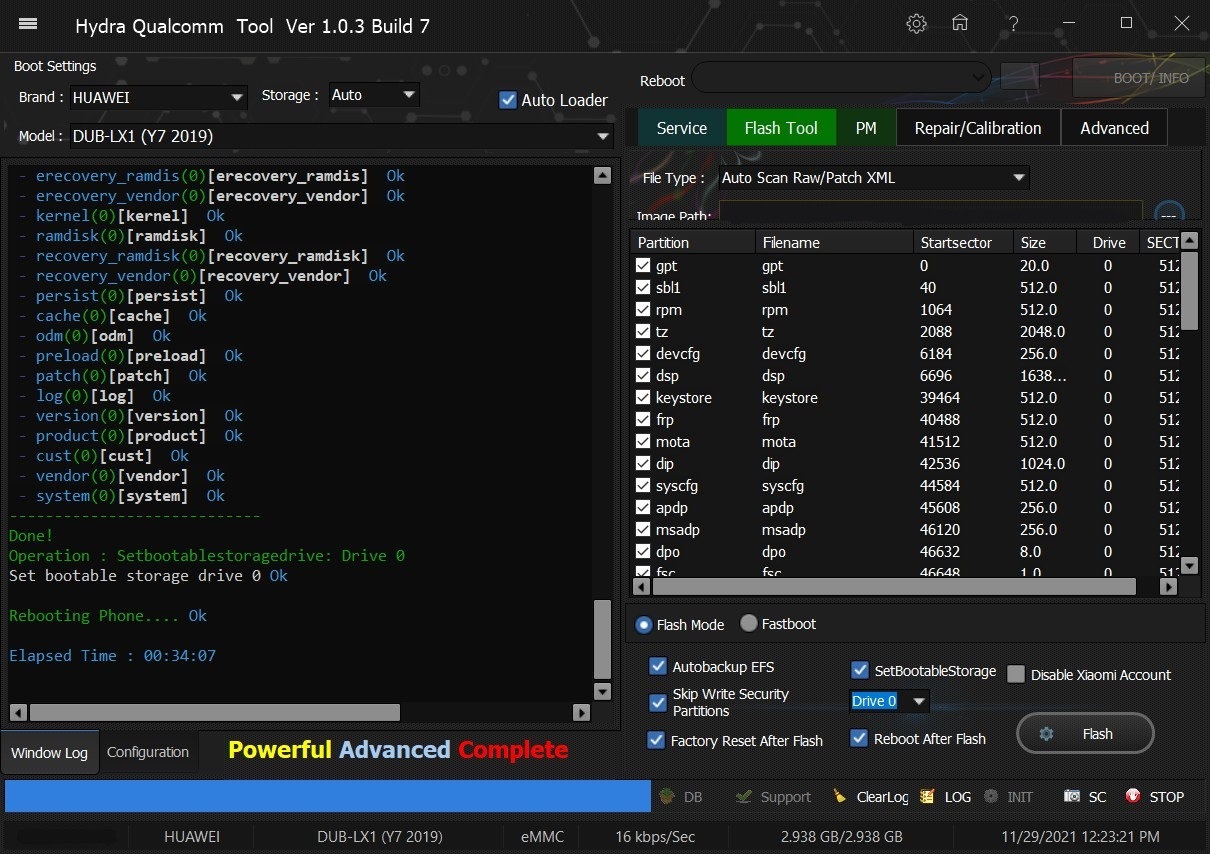 Quote:
| |
 |
| | #2780 (permalink) | |
| No Life Poster       Join Date: Feb 2012 Age: 39
Posts: 1,395
Member: 1724862 Status: Offline Thanks Meter: 448 | Huawei Y7 2019 (DUB-LX1) Fix Sound Problem done With by Hydra Edl FLashıng Huawei Y7 2019 (DUB-LX1) Fix Sound Problem done With by Hydra Edl FLashıng  Quote:
| |
 |
| | #2781 (permalink) | |
| No Life Poster       Join Date: Feb 2012 Age: 39
Posts: 1,395
Member: 1724862 Status: Offline Thanks Meter: 448 | Realme C25 (RMX3191) Unlock Bootlaoder With by Hydra Realme C25 (RMX3191) Unlock Bootlaoder With by Hydra 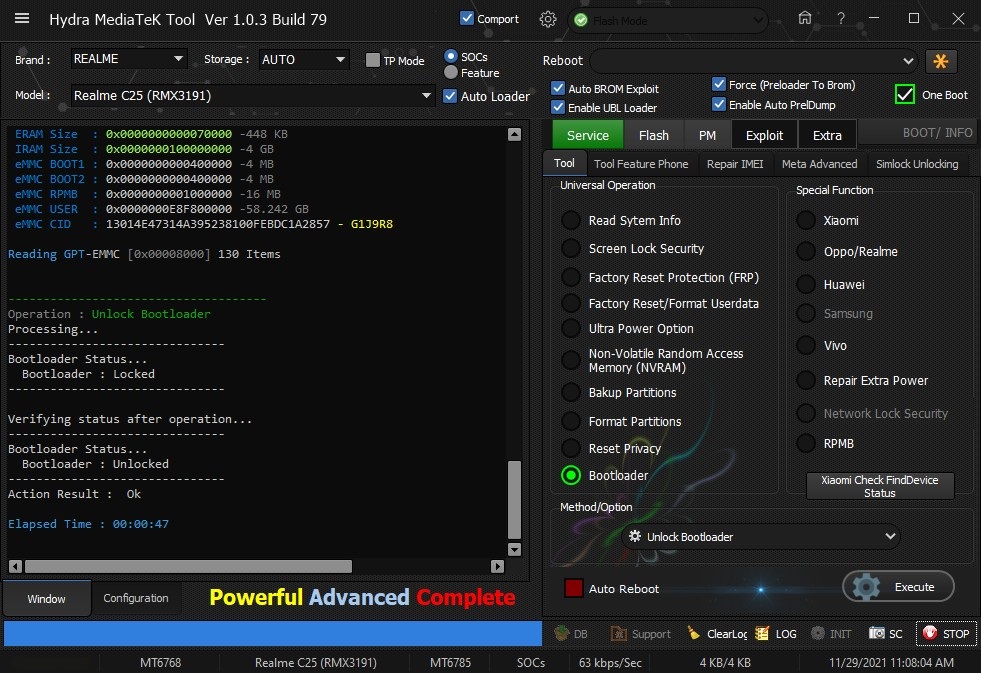 Quote:
| |
 |
| | #2782 (permalink) | |
| No Life Poster       Join Date: Feb 2012 Age: 39
Posts: 1,395
Member: 1724862 Status: Offline Thanks Meter: 448 | Mi Max 3 (Nitrogen) Edl Frp Remove done by Hydra Mi Max 3 (Nitrogen) Edl Frp Remove done by Hydra 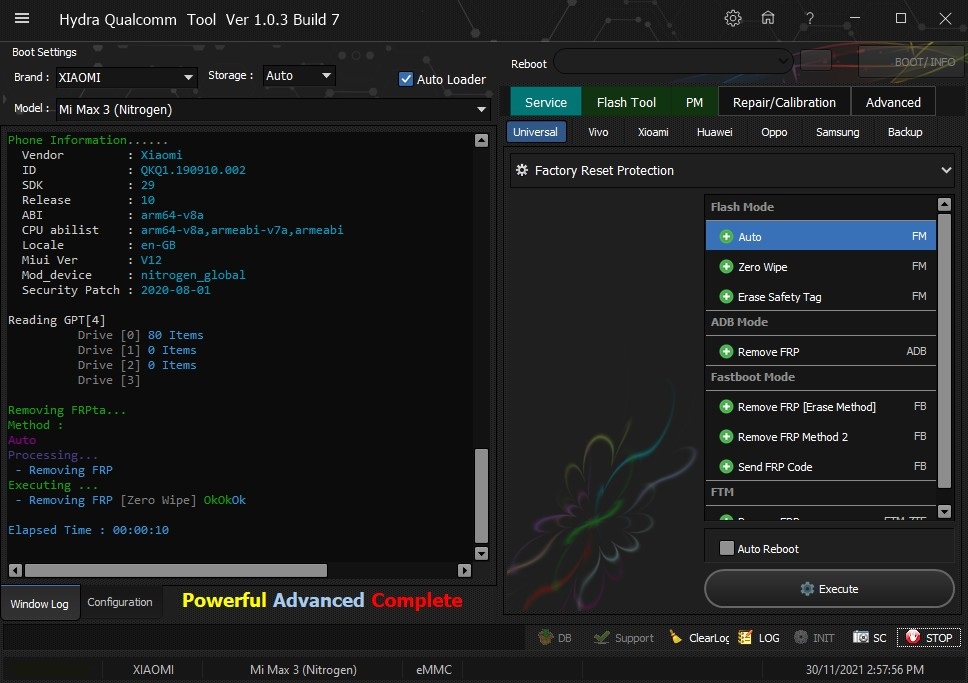 Quote:
| |
 |
| | #2783 (permalink) | |
| No Life Poster       Join Date: Feb 2012 Age: 39
Posts: 1,395
Member: 1724862 Status: Offline Thanks Meter: 448 | Oppo F1s Pattern lock read code Without data loss by Hydra Oppo F1s Pattern lock read code Without data loss by Hydra 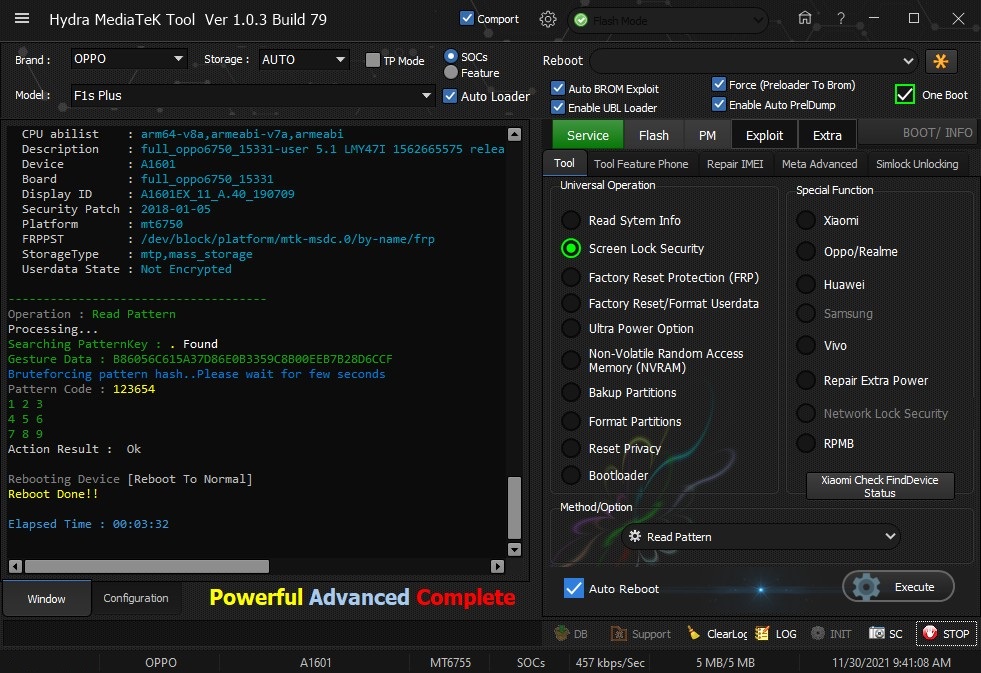 Quote:
| |
 |
| | #2784 (permalink) | |
| No Life Poster       Join Date: Feb 2012 Age: 39
Posts: 1,395
Member: 1724862 Status: Offline Thanks Meter: 448 | Redmi 9 (lancelot) Unlock Bootloader With by Hydra Redmi 9 (lancelot) Unlock Bootloader With by Hydra 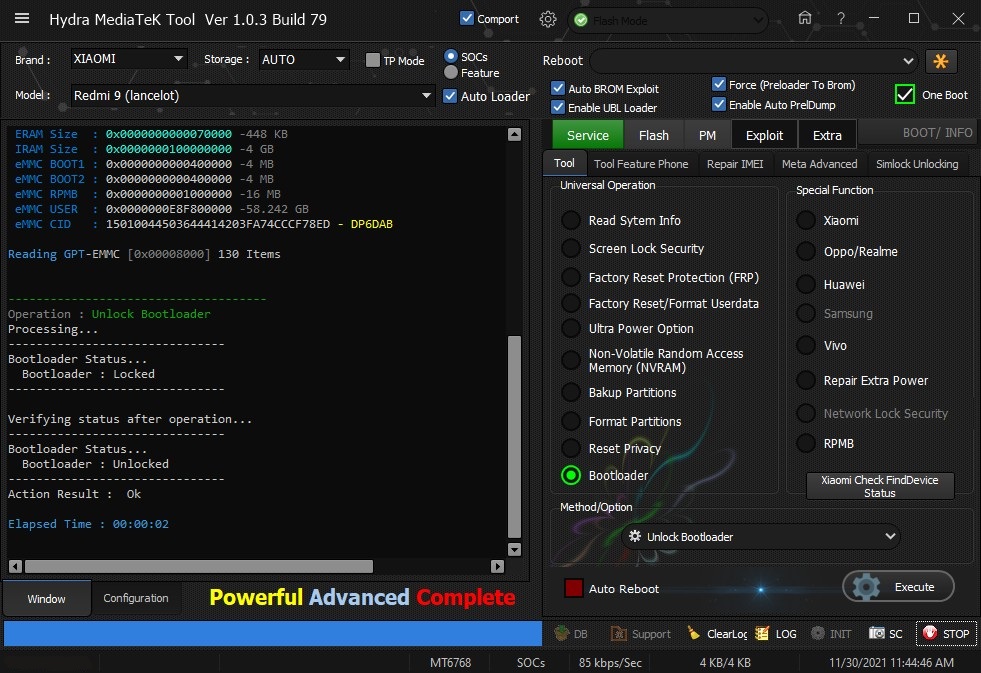 Quote:
| |
 |
| | #2785 (permalink) | |
| No Life Poster       Join Date: Feb 2012 Age: 39
Posts: 1,395
Member: 1724862 Status: Offline Thanks Meter: 448 | Redmi 9A (dandelion) Bootloader Unlock Done with by Hydra Redmi 9A (dandelion) Bootloader Unlock Done with by Hydra 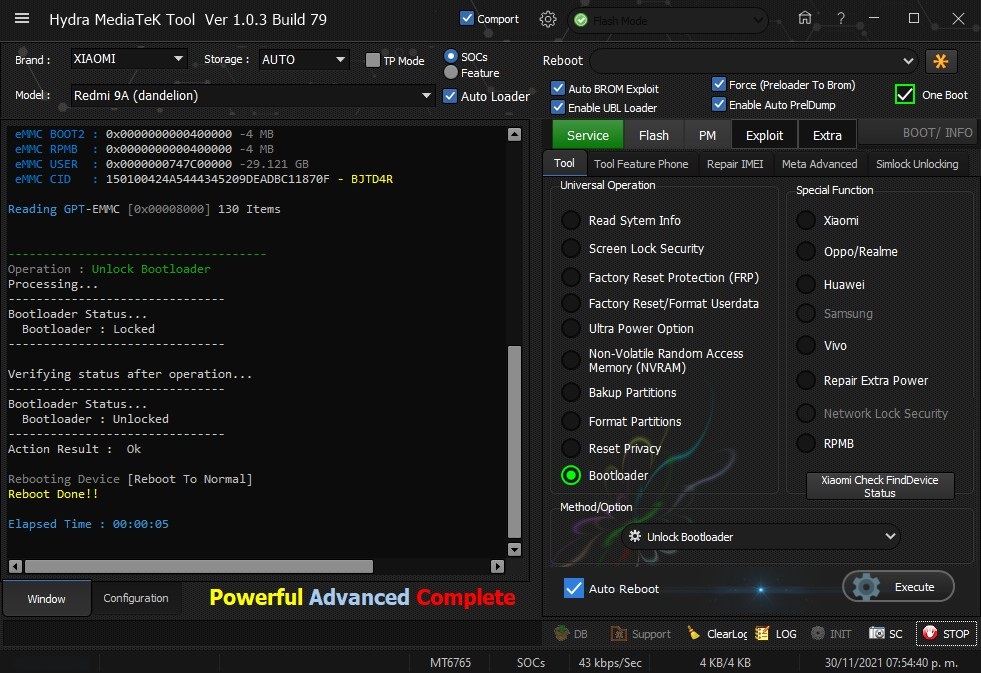 Quote:
| |
 |
| | #2786 (permalink) | |
| No Life Poster       Join Date: Feb 2012 Age: 39
Posts: 1,395
Member: 1724862 Status: Offline Thanks Meter: 448 | Redmi 8A (olivelite) Edl Frp Remove with by Hydra Redmi 8A (olivelite) Edl Frp Remove with by Hydra 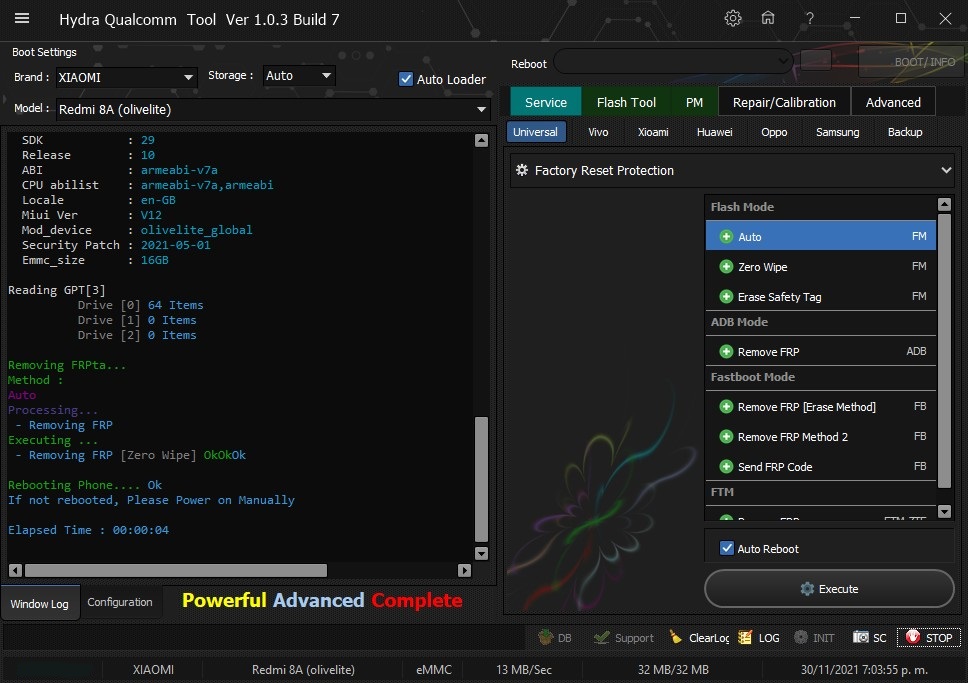 Quote:
| |
 |
| | #2787 (permalink) | |
| No Life Poster       Join Date: Feb 2012 Age: 39
Posts: 1,395
Member: 1724862 Status: Offline Thanks Meter: 448 | Vivo Y53 Format Userdata One click done by Hydra Vivo Y53 Format Userdata One click done by Hydra 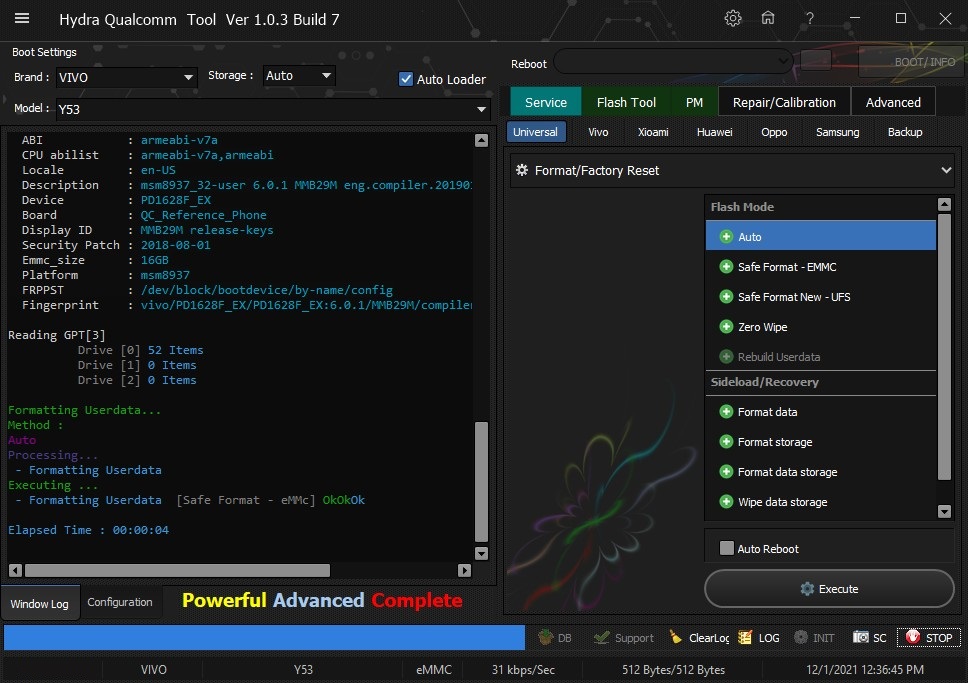 Quote:
| |
 |
| | #2789 (permalink) | |
| No Life Poster       Join Date: Feb 2012 Age: 39
Posts: 1,395
Member: 1724862 Status: Offline Thanks Meter: 448 | Redmi Note 9 (merlin) Bootlaoder Unlock With by Hydra Redmi Note 9 (merlin) Bootlaoder Unlock With by Hydra 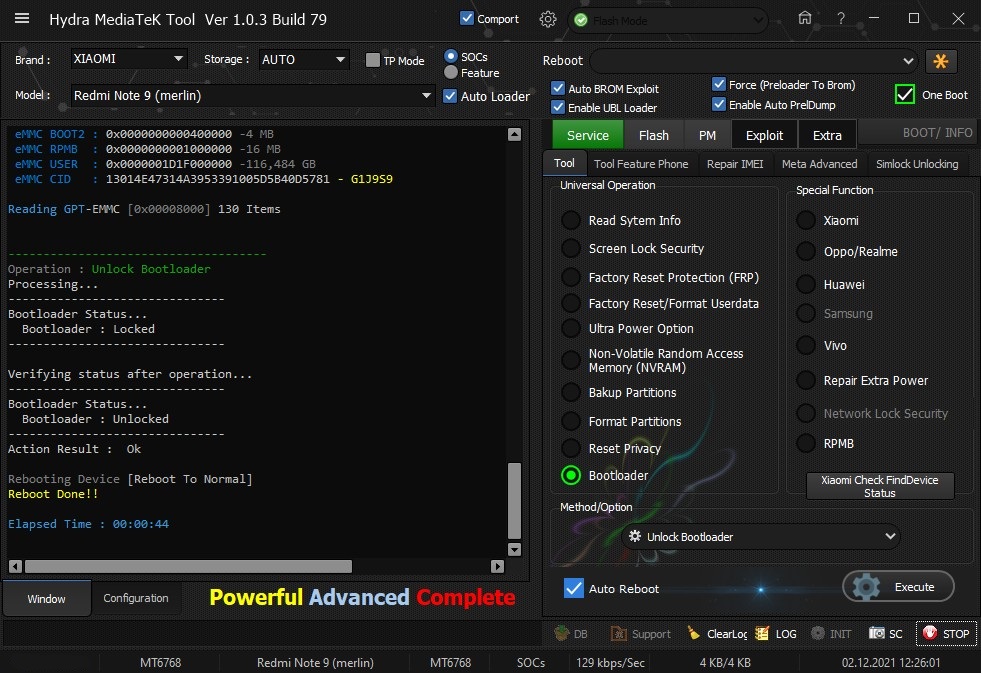 Quote:
| |
 |
| | #2790 (permalink) | |
| No Life Poster       Join Date: Feb 2012 Age: 39
Posts: 1,395
Member: 1724862 Status: Offline Thanks Meter: 448 | Redmi Note 8 (ginkgo) Edl Frp Remove With by Hydra Redmi Note 8 (ginkgo) Edl Frp Remove With by Hydra 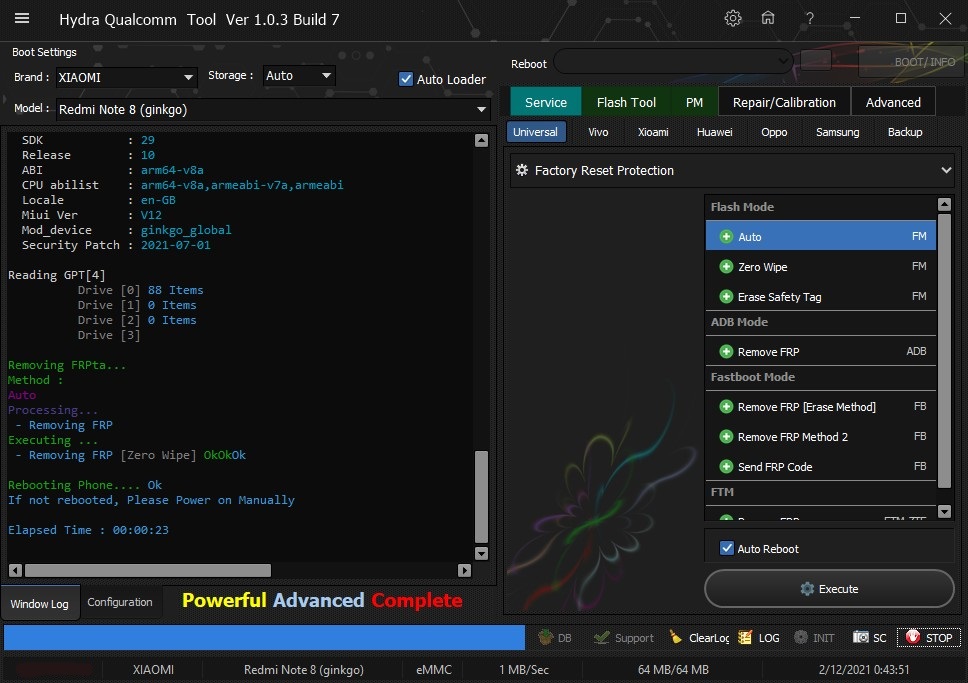 Quote:
| |
 |
 |
| Bookmarks |
| |
|
|