



  |
 |
|
Welcome to the GSM-Forum forums. You are currently viewing our boards as a guest which gives you limited access to view most discussions and access our other features. Only registered members may post questions, contact other members or search our database of over 8 million posts. Registration is fast, simple and absolutely free so please - Click to REGISTER! If you have any problems with the registration process or your account login, please contact contact us . |
| |||||||
| Register | FAQ | Donate | Forum Rules | Root any Device | ★iPhone Unlock★ | ★ Direct Codes ★ | Direct Unlock Source | Today's Posts | Search |
 |
| | LinkBack | Thread Tools | Display Modes |
| | #241 (permalink) |
| Freak Poster     Join Date: Oct 2016 Location: Surandai TN India Age: 37
Posts: 471
Member: 2637068 Status: Offline Thanks Meter: 276 | Xiaomi Redmi Note 3 Mi Account Unlock Done  Code: Hydra Qualcomm Tool Ver 1.0.1 Build 30
Windows 7 Service Pack 1 (Version 6.1, Build 7601, 32-bit Edition)
******* Dongle Info *******
Version : Hydra Tool v 1.1
Serial : 190300000278
Initialize : OKAY
Status : Activated
Selected Comport : Auto
Selected Loader : Auto
Searching Qualcomm 9008 Port[FOUND](COM11)
Getting device info.......
Serial No.: 0x03D24211
MSM ID : 0x009B00E1
PBL Ver : 00000000
PK HASH : 57158EAF1814D78FD2B3105ECE4DB18A
817A08AC664A5782A925F3FF8403D39A
Firehose Loader[prog_emmc_firehose_8976_ddr_1.mbn]
Sending ..................Ok
Connecting to Firehose...
Ping... Ok
Configuration......Ok
Chip Configuration :
MemoryName : eMMC
MaxPayloadSizeToTargetInBytes : 1048576
MaxPayloadSizeToTargetInBytesSupported : 1048576
MaxPayloadSizeFromTargetInBytes : 4096
MaxXMLSizeInBytes : 4096
TargetName : 8976
Version : 1
*** STORAGE DEVICE INFO ***
Memory Type : eMMC
Block Size in Bytes : 512
Page Size : 512
Manufacturer ID : 17
Serial Number : 1608991657
Firmware Version : 4
Product Name : 032G34
Physical Partitions : 3
Total Logical Blocks:
Storage [0] 61071360[29.121 GB]
Storage [1] 8192[4 MB]
Storage [2] 8192[4 MB]
Running : Ok
Phone Information.....
Model : Redmi Note 3
Brand : Xiaomi
Android Ver : 6.0.1
Miui Ver : V8
Manufacturer : Xiaomi
Device : kenzo
Mod_device : kenzo_global
Board : msm8952
Display ID : MMB29M
Security Patch : 2017-09-01
Platform : msm8952
Kernel ID : 2017-09-01
FRPPST : /dev/block/bootdevice/by-name/config
======================================
EDL_Resetting Mi Account...
Backing up Partition for safety...Ok
Scanning Patching address...
> Patching address detected [PATCHED]
> Patching address detected [PATCHED]
> Patching address detected [PATCHED]
> Patching address detected [PATCHED]
> Patching address detected [PATCHED]
> Patching address detected [PATCHED]
> Patching address detected [PATCHED]
> Patching address detected [PATCHED]
> Patching address detected [PATCHED]
> Patching address detected [PATCHED]
> Patching address detected [PATCHED]
> Patching address detected [PATCHED]
> Patching address detected [PATCHED]
> Patching address detected [PATCHED]
> Patching address detected [PATCHED]
> Patching address detected [PATCHED]
> Patching address detected [PATCHED]
> Patching address detected [PATCHED]
> Patching address detected [PATCHED]
> Patching address detected [PATCHED]
> Patching address detected [PATCHED]
> Patching address detected [PATCHED]
> Patching address detected [PATCHED]
> Patching address detected [PATCHED]
> Patching address detected [PATCHED]
> Patching address detected [PATCHED]
> Patching address detected [PATCHED]
> Patching address detected [PATCHED]
> Patching address detected [PATCHED]Done!!
Total Items patched : 29
Successfully patched address..Ok
All Done
======================================
Elapsed Time : 00:00:24 |
 |
| The Following 2 Users Say Thank You to johnson1002222 For This Useful Post: |
| | #242 (permalink) | |
| No Life Poster       Join Date: Feb 2012 Age: 39
Posts: 1,395
Member: 1724862 Status: Offline Thanks Meter: 448 | Coolpad 3632A Reset FRP By Hydra Coolpad 3632A Reset FRP By Hydra Quote:
| |
 |
| The Following 2 Users Say Thank You to ceza031 For This Useful Post: |
| | #243 (permalink) | |
| No Life Poster       Join Date: Feb 2012 Age: 39
Posts: 1,395
Member: 1724862 Status: Offline Thanks Meter: 448 | Coolpad 3600I Reset FRP by Hydra Tool Coolpad 3600I Reset FRP by Hydra Tool Quote:
| |
 |
| The Following 2 Users Say Thank You to ceza031 For This Useful Post: |
| | #244 (permalink) |
| No Life Poster       Join Date: Feb 2012 Age: 39
Posts: 1,395
Member: 1724862 Status: Offline Thanks Meter: 448 | Xiaomi Redmi Note 6 Pro Repair IMEI by Hydra Tool 1 - Wipe Security at EDL Mode :  2 - Enable Diag use Reboots tab, Without Root method and Repair by Diag:  3 - Write QCN Which at Support Area by QPST :  4 - any Happy End!   p.s : This method no need unlocked bootloader and Root |
 |
| The Following 3 Users Say Thank You to ceza031 For This Useful Post: |
| | #246 (permalink) |
| Freak Poster     Join Date: Oct 2016 Location: Surandai TN India Age: 37
Posts: 471
Member: 2637068 Status: Offline Thanks Meter: 276 | Mobiistar C1 Lite Frp Unlock Done  Code: Hydra MediaTeK Tool Ver 1.0.1 Build 35 Windows 7 Service Pack 1 (Version 6.1, Build 7601, 32-bit Edition) Installed RAM : 3.372 GB ******* Dongle Info ******* Version : Hydra Tool v 1.1 Serial : 190300000278 Initialize : OKAY Status : Activated Brand : MOBIISTAR Model : C1 Lite ===================================== How To Boot : Power off phone * BROM Mode : Press VOL + * Preloader Mode : Just Insert cable Connection[WAITING]Found Mode[PreLoader] Port[COM35] Status[Opened] Identifying Hardware ID BROM CPUID : 0699 (0000)MT6739[6739] BROM HW_SW_VER : 8A00 CA00 0000 0000 SECURE VERSION : FF BL VERSION : 03 BR Secured : 00 Preparing Download Agent.. Download Agent : Trying default 6739.bin MTK_DOWNLOAD_AGENT -HYDRA MTK_AllInOne_DA_v3.3001.2018-09-18.13:22_452898 Initializing Loader [1] Sending Loader [1] Accepted PROTOCOL[NEW] - eMMC PHONE SYNC[Accepted] DA Mode : preloader Initializing Loader [2] Sending Loader [2] Accepted ERAM Size : 0x0000000040000000 -1024 MB IRAM Size : 0x0000000000020000 -128 KB eMMC BOOT1 : 0x0000000000400000 -4 MB eMMC BOOT2 : 0x0000000000400000 -4 MB eMMC RPMB : 0x0000000000400000 -4 MB eMMC USER : 0x00000001C8000000 -7.125 GB eMMC CID : 7001004548384545380115F466F95513 UNICAL RID : 1F0BD8162CA8E09BDEFC4D221CEA5F45 DA Speed : high-speed DA Speed : high-speed Reading Partition Table[0x00008000] 36 Items Done!!! Reading System Info Model : C1 Lite Brand : mobiistar Android Ver : 8.1.0 Manufacturer : mobiistar Device : C1_Lite Board : C1_Lite Display ID : mobiistar_C1_Lite_IN_V1.15_20180907 Security Patch : 2018-07-05 Platform : mt6739 Kernel ID : 2018-07-05 Autobackup Partitions preloader[0x00000000-0x00080000]512 KB Done Creating Scatter file...C:\Hydra Tool\\Backup\Auto\mobiistar_C1 Lite_0699-mt6739-8.1.0(mobiistar_C1_Lite_IN_V1.15_20180907)_230819151909\\MT6739_Android_scatter.txt nvdata[0x03688000-0x05688000]32 MB Done nvram[0x10700000-0x10C00000]5 MB Done Done!!! C:\Hydra Tool\\Backup\Auto\mobiistar_C1 Lite_0699-mt6739-8.1.0(mobiistar_C1_Lite_IN_V1.15_20180907)_230819151909 MTK Phone Loader is NOW RUNNING. DA Speed : high-speed Reading Partition Table[0x00008000] 36 Items Done!!! Reading System Info Model : C1 Lite Brand : mobiistar Android Ver : 8.1.0 Manufacturer : mobiistar Device : C1_Lite Board : C1_Lite Display ID : mobiistar_C1_Lite_IN_V1.15_20180907 Security Patch : 2018-07-05 Platform : mt6739 Kernel ID : 2018-07-05 ------------------------------------- FRP Security.. Operation : Auto Remove FRP Operation Ok ===================================== Elapsed Time : 00:00:29 |
 |
| The Following 2 Users Say Thank You to johnson1002222 For This Useful Post: |
| | #247 (permalink) |
| Freak Poster     Join Date: Oct 2016 Location: Surandai TN India Age: 37
Posts: 471
Member: 2637068 Status: Offline Thanks Meter: 276 | GIONEE A1 lite Frp Unlock Done  Code: Hydra MediaTeK Tool Ver 1.0.1 Build 35 Windows 7 Service Pack 1 (Version 6.1, Build 7601, 32-bit Edition) Installed RAM : 3.372 GB ******* Dongle Info ******* Version : Hydra Tool v 1.1 Serial : 190300000278 Initialize : OKAY Status : Activated Brand : AUTO Model : AUTO ===================================== How To Boot : Power off phone * BROM Mode : Press VOL + * Preloader Mode : Just Insert cable Connection[WAITING]Found Mode[PreLoader] Port[COM35] Status[Opened] Identifying Hardware ID BROM CPUID : 0337 (0000)MT6753[6735] BROM HW_SW_VER : 8A00 CA00 0000 0000 SECURE VERSION : FF BL VERSION : 01 BR Secured : 00 Preparing Download Agent.. Download Agent : 6735.bin6735.bin MTK_DOWNLOAD_AGENT -HYDRA MTK_AllInOne_DA_v3.3001.2018-09-18.13:22_452898 Initializing Loader [1] Sending Loader [1] Accepted PROTOCOL[OLD] - eMMC PRMMCCID : 520001154D423158D9A3074237C30D97 Running DA 4.2 on BBID : 0x9B Init Configuration Ok Initializing Loader [2] Sending Loader [2] Accepted Reading Flashchip data.... eMMC BOOT1 : 0x0000000000400000 -4 MB eMMC BOOT2 : 0x0000000000400000 -4 MB eMMC RPMB : 0x0000000000400000 -4 MB eMMC USER : 0x0000000747C00000 -29.121 GB ERAM Size : 0x00000000C0000000 -3 GB IRAM Size : 0x0000000000020000 -128 KB UNICAL RID : 305E725B5C1D52B6C92AFFFE6B7F25DF eMMC CID : 520001154D423158D9A3074237640D97 Change to HIGH SPEED... Connection[WAITING]Found Mode Port[COM36] Status[Opened] Reading Partition Table SIZE[0x000007E8] 23 Items > Done Reading System Info Model : A1 lite Brand : GIONEE Android Ver : 7.0 Manufacturer : GIONEE Device : GIONEE_SWW1618 Board : A1_lite Display ID : amigo4.0 Security Patch : 2017-07-05 Platform : mt6753 Kernel ID : 2017-07-05 FRPPST : /dev/block/platform/mtk-msdc.0/11230000.msdc0/by-name/frp Autobackup Partitions preloader [0x00000000-0x00040000] 256 KB Done nvram [0x00380000-0x00880000] 5 MB Done nvdata [0x06B00000-0x08B00000] 32 MB Done Done!!! C:\Hydra Tool\\Backup\Auto\GIONEE_A1 lite_0337-mt6753-7.0(amigo4.0)_230819162218 MTK Phone Loader is NOW RUNNING. Reading System Info Model : A1 lite Brand : GIONEE Android Ver : 7.0 Manufacturer : GIONEE Device : GIONEE_SWW1618 Board : A1_lite Display ID : amigo4.0 Security Patch : 2017-07-05 Platform : mt6753 Kernel ID : 2017-07-05 FRPPST : /dev/block/platform/mtk-msdc.0/11230000.msdc0/by-name/frp ------------------------------------- FRP Security.. Operation : Auto Remove FRP Operation Ok ===================================== Elapsed Time : 00:00:22 |
 |
| The Following 2 Users Say Thank You to johnson1002222 For This Useful Post: |
| | #248 (permalink) |
| Freak Poster     Join Date: Oct 2016 Location: Surandai TN India Age: 37
Posts: 471
Member: 2637068 Status: Offline Thanks Meter: 276 | Xiaomi Redmi 5A Mi Account Unlock Done  Code: Hydra Qualcomm Tool Ver 1.0.1 Build 30
Windows 7 Service Pack 1 (Version 6.1, Build 7601, 32-bit Edition)
******* Dongle Info *******
Version : Hydra Tool v 1.1
Serial : 190300000278
Initialize : OKAY
Status : Activated
Selected Comport : Auto
Selected Loader : Auto
Searching Qualcomm 9008 Port[FOUND](COM38)
Getting device info.......
Serial No.: 0x1969B60F
MSM ID : 0x000560E1
PBL Ver : 00000000
PK HASH : 57158EAF1814D78FD2B3105ECE4DB18A
817A08AC664A5782A925F3FF8403D39A
Firehose Loader[mi_2_2.mbn]
Sending ...................Ok
Connecting to Firehose...
Ping... Ok
Configuration......Ok
Chip Configuration :
MemoryName : eMMC
MaxPayloadSizeToTargetInBytes : 1048576
MaxPayloadSizeToTargetInBytesSupported : 1048576
MaxPayloadSizeFromTargetInBytes : 4096
MaxXMLSizeInBytes : 4096
TargetName : 8917
Version : 1
*** STORAGE DEVICE INFO ***
Memory Type : eMMC
Block Size in Bytes : 512
Page Size : 512
Manufacturer ID : 21
Serial Number : 3628111372
Firmware Version : 3
Product Name : QE63MB
Physical Partitions : 3
Total Logical Blocks:
Storage [0] 30535680[14.561 GB]
Storage [1] 8192[4 MB]
Storage [2] 8192[4 MB]
Running : Ok
Phone Information.....
Model : Redmi 5A
Brand : Xiaomi
Android Ver : 7.1.2
Miui Ver : V9
Manufacturer : Xiaomi
Device : riva
Mod_device : riva_global
Board : QC_Reference_Phone
Display ID : N2G47H
Security Patch : 2018-02-01
Platform : msm8937
Kernel ID : 2018-02-01
FRPPST : /dev/block/bootdevice/by-name/config
======================================
EDL_Resetting Mi Account...
Backing up Partition for safety...Ok
Scanning Patching address...
> Patching address detected [PATCHED]
> Patching address detected [PATCHED]
> Patching address detected [PATCHED]
> Patching address detected [PATCHED]
> Patching address detected [PATCHED]
> Patching address detected [PATCHED]Done!!
Total Items patched : 6
Successfully patched address..Ok
All Done
======================================
Elapsed Time : 00:00:24 |
 |
| The Following 2 Users Say Thank You to johnson1002222 For This Useful Post: |
| | #250 (permalink) |
| Freak Poster     Join Date: Aug 2017 Location: Ukraine
Posts: 202
Member: 2750401 Status: Offline Thanks Meter: 134 | Xiaomi Redmi 5 frp done Code: Hydra Qualcomm Tool Ver 1.0.1 Build 30
Windows 10 (Version 10.0, Build 17763, 64-bit Edition)
******* Dongle Info *******
Version : Hydra Tool v 1.1
Serial : 190600001112
Initialize : OKAY
Status : Activated
Selected Comport : Auto
Selected Loader : Auto
Searching Qualcomm 9008 Port[FOUND](COM13)
Getting device info.......
Serial No.: 0x6960BFE3
MSM ID : 0x0009A0E1
PBL Ver : 00000000
PK HASH : 57158EAF1814D78FD2B3105ECE4DB18A
817A08AC664A5782A925F3FF8403D39A
Firehose Loader[prog_emmc_firehose_8953_ddr.mbn]
Sending ..................Ok
Connecting to Firehose...
Ping... Ok
Configuration......Ok
Chip Configuration :
MemoryName : eMMC
MaxPayloadSizeToTargetInBytes : 1048576
MaxPayloadSizeToTargetInBytesSupported : 1048576
MaxPayloadSizeFromTargetInBytes : 4096
MaxXMLSizeInBytes : 4096
TargetName : 8953
Version : 1
*** STORAGE DEVICE INFO ***
Memory Type : eMMC
Block Size in Bytes : 512
Page Size : 512
Manufacturer ID : 21
Serial Number : 1847117356
Firmware Version : 1
Product Name : GD6BMB
Physical Partitions : 3
Total Logical Blocks:
Storage [0] 61071360[29,121 GB]
Storage [1] 8192[4 MB]
Storage [2] 8192[4 MB]
Running : Ok
Phone Information....
020000000C0001022E000000020000000C0002022E2E00000B00000014000A026C6F73742B666F756E6400000C0000000C000302617070005E0100000C00030262696E00B202000014000A016275696C642E70726F700000B302000020001801636F6D7061746962696C6974795F6D61747269782E786D6CB402000010000802646174612D617070BB0200000C00030265746300CF0400001400090266616B652D6C696273000000D104000014000B0266616B652D6C696273363400D304000010000502666F6E747300000088050000140009026672616D65776F726B0000009B0700000C0003026C696200C7090000100005026C696236340000003B0C000014000C016D616E69666573742E786D6C3C0C0000100005026D65646961000000C10D000010000802707269762D617070BF0E00001C0014017265636F766572792D66726F6D2D626F6F742E70C00E00000C00030274747300CE0E00000C00030275737200910F00001000060276656E646F7200000C1D00008C0E04027862696E000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000B0000000C0001022E00000002000000F40F02022E2E000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000.
Model : Redmi 5
Brand : Xiaomi
Android Ver : 8.1.0
Miui Ver : V10
Manufacturer : Xiaomi
Device : rosy
Mod_device : rosy_global
Board : msm8953
Display ID : CUSTOMER_VERSION_rosy
Security Patch : 2019-06-01
Platform : msm8953
Kernel ID : 2019-06-01
FRPPST : /dev/block/bootdevice/by-name/config
======================================
*** FRP Reset ***
Resetting FRP...
Zero Wipe Ok
FRP Operation Done!!
All Done
======================================
Elapsed Time : 00:00:13 |
 |
| The Following 2 Users Say Thank You to dimasc For This Useful Post: |
| | #251 (permalink) | |
| Product Manager      Join Date: Aug 2018 Location: Ukraine / Harkov
Posts: 1,999
Member: 2857401 Status: Offline Thanks Meter: 6,902 | Xiaomi Mi 8 (dipper) UFS Remove Mi Account by Hydra Tool !! Xiaomi Mi 8 (dipper) UFS Remove Mi Account by Hydra Tool !! Quote:
 | |
 |
| The Following User Says Thank You to Hydra Tool For This Useful Post: |
| | #252 (permalink) | |
| Product Manager      Join Date: Aug 2018 Location: Ukraine / Harkov
Posts: 1,999
Member: 2857401 Status: Offline Thanks Meter: 6,902 | Xiaomi Mi 8 (dipper) UFS Remove Mi Account by Hydra Tool !! Xiaomi Mi 8 (dipper) UFS Remove Mi Account by Hydra Tool !! Quote:
 | |
 |
| The Following User Says Thank You to Hydra Tool For This Useful Post: |
| | #253 (permalink) | |
| Product Manager      Join Date: Aug 2018 Location: Ukraine / Harkov
Posts: 1,999
Member: 2857401 Status: Offline Thanks Meter: 6,902 | Lenovo K5 Play L38011 Reset FRP By Hydra Lenovo K5 Play L38011 Reset FRP By Hydra Quote:
| |
 |
| The Following User Says Thank You to Hydra Tool For This Useful Post: |
| | #254 (permalink) |
| Freak Poster     Join Date: Oct 2016 Location: Surandai TN India Age: 37
Posts: 471
Member: 2637068 Status: Offline Thanks Meter: 276 | Oppo A5s (Cph 1909) Pattern Lock Remove By Hydra Tool Without Isp & Tp 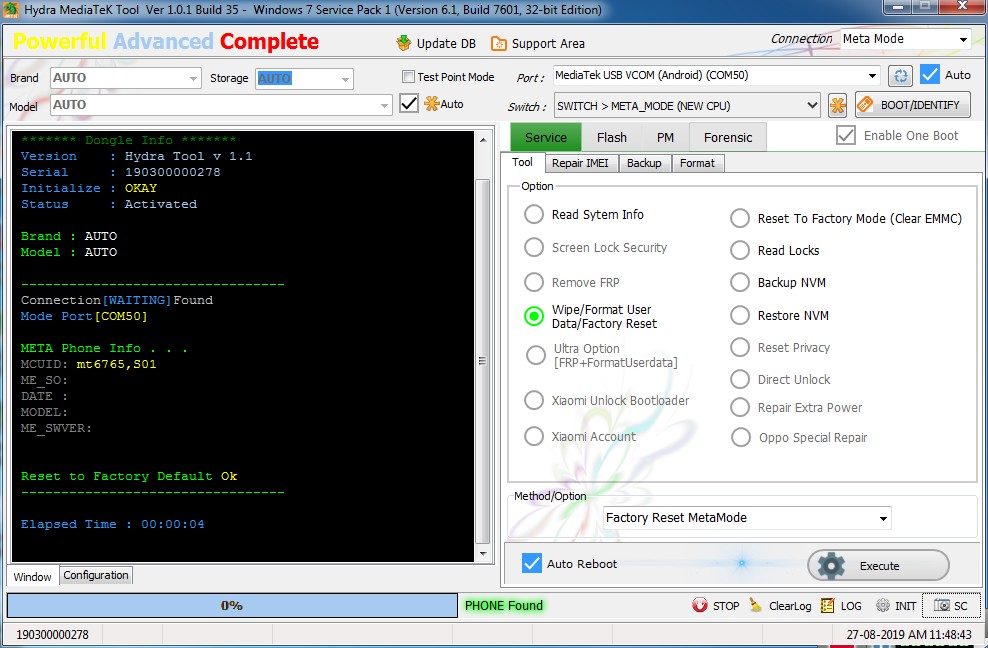 Code: Hydra MediaTeK Tool Ver 1.0.1 Build 35 Windows 7 Service Pack 1 (Version 6.1, Build 7601, 32-bit Edition) Installed RAM : 3.372 GB ******* Dongle Info ******* Version : Hydra Tool v 1.1 Serial : 190300000278 Initialize : OKAY Status : Activated Brand : AUTO Model : AUTO --------------------------------- Connection[WAITING]Found Mode Port[COM50] META Phone Info . . . MCUID: mt6765,S01 ME_SO: DATE : MODEL: ME_SWVER: Reset to Factory Default Ok --------------------------------- Elapsed Time : 00:00:04 |
 |
| The Following 2 Users Say Thank You to johnson1002222 For This Useful Post: |
| | #255 (permalink) |
| Freak Poster     Join Date: Oct 2016 Location: Surandai TN India Age: 37
Posts: 471
Member: 2637068 Status: Offline Thanks Meter: 276 | Xiaomi Redmi 4A Frp Unlock Done  Code: Hydra Qualcomm Tool Ver 1.0.1 Build 30
Windows 7 Service Pack 1 (Version 6.1, Build 7601, 32-bit Edition)
******* Dongle Info *******
Version : Hydra Tool v 1.1
Serial : 190300000278
Initialize : OKAY
Status : Activated
Selected Comport : Auto
Selected Loader : Auto
Searching Qualcomm 9008 Port[FOUND](COM38)
Getting device info.......
Serial No.: 0x270CD5B2
MSM ID : 0x000560E1
PBL Ver : 00000000
PK HASH : 57158EAF1814D78FD2B3105ECE4DB18A
817A08AC664A5782A925F3FF8403D39A
Firehose Loader[mi_2_2.mbn]
Sending ...................Ok
Connecting to Firehose...
Ping... Ok
Configuration......Ok
Chip Configuration :
MemoryName : eMMC
MaxPayloadSizeToTargetInBytes : 1048576
MaxPayloadSizeToTargetInBytesSupported : 1048576
MaxPayloadSizeFromTargetInBytes : 4096
MaxXMLSizeInBytes : 4096
TargetName : 8917
Version : 1
*** STORAGE DEVICE INFO ***
Memory Type : eMMC
Block Size in Bytes : 512
Page Size : 512
Manufacturer ID : 19
Serial Number : 79959237
Firmware Version : 84
Product Name : Q3J96R
Physical Partitions : 3
Total Logical Blocks:
Storage [0] 30777344[14.676 GB]
Storage [1] 8192[4 MB]
Storage [2] 8192[4 MB]
Running : Ok
Phone Information.....
Model : Redmi 4A
Brand : Xiaomi
Android Ver : 7.1.2
Miui Ver : V9
Manufacturer : Xiaomi
Device : rolex
Mod_device : rolex_global
Board : QC_Reference_Phone
Display ID : N2G47H
Security Patch : 2018-03-01
Platform : msm8937
Kernel ID : 2018-03-01
FRPPST : /dev/block/bootdevice/by-name/config
======================================
*** FRP Reset ***
Resetting FRP...
Zero Wipe Ok
FRP Operation Done!!
All Done
======================================
Elapsed Time : 00:00:10 |
 |
| The Following User Says Thank You to johnson1002222 For This Useful Post: |
 |
| Bookmarks |
| |
|
|