



  |
 |
|
Welcome to the GSM-Forum forums. You are currently viewing our boards as a guest which gives you limited access to view most discussions and access our other features. Only registered members may post questions, contact other members or search our database of over 8 million posts. Registration is fast, simple and absolutely free so please - Click to REGISTER! If you have any problems with the registration process or your account login, please contact contact us . |
| |||||||
| Register | FAQ | Donate | Forum Rules | Root any Device | ★iPhone Unlock★ | ★ Direct Codes ★ | Direct Unlock Source |
 |
| | LinkBack | Thread Tools | Display Modes |
| | #2851 (permalink) | |
| No Life Poster       Join Date: Feb 2012 Age: 39
Posts: 1,395
Member: 1724862 Status: Offline Thanks Meter: 448 | Vivo Y11 (1906) Edl Format Userdata &Frp Remove One Click With by Hydra  Quote:
| |
 |
| | #2852 (permalink) | |
| No Life Poster       Join Date: Feb 2012 Age: 39
Posts: 1,395
Member: 1724862 Status: Offline Thanks Meter: 448 | Redmi Note 3 (Kenzo) Edl Frp Remove One click With by Hydra Redmi Note 3 (Kenzo) Edl Frp Remove One click With by Hydra 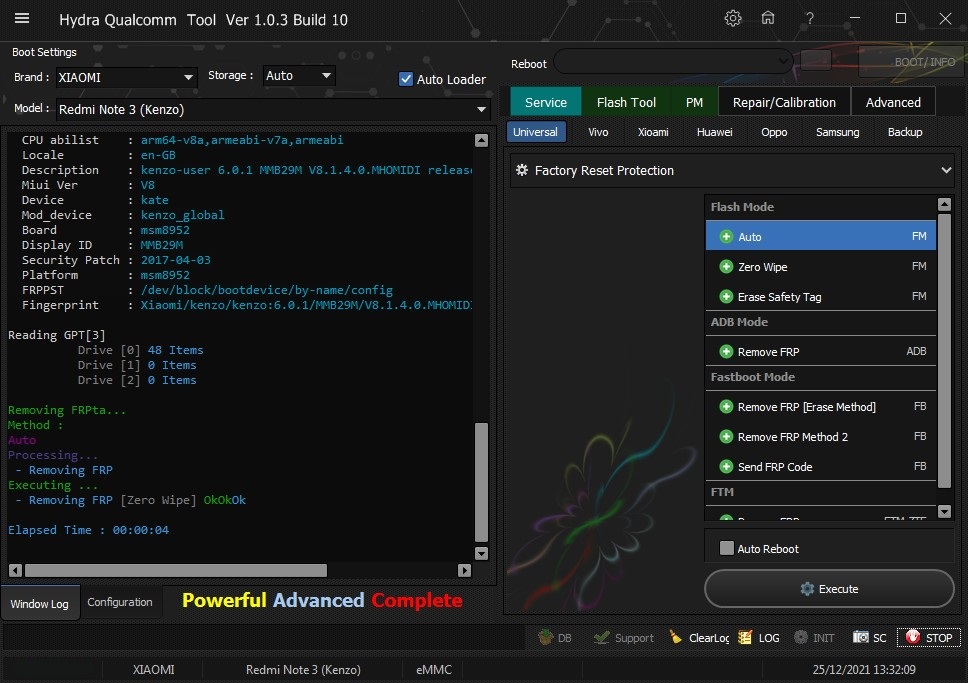 Quote:
| |
 |
| | #2853 (permalink) | |
| No Life Poster       Join Date: Feb 2012 Age: 39
Posts: 1,395
Member: 1724862 Status: Offline Thanks Meter: 448 | Redmi Note 4X (Mido) Edl Frp Remove With by Hydra Redmi Note 4X (Mido) Edl Frp Remove With by Hydra 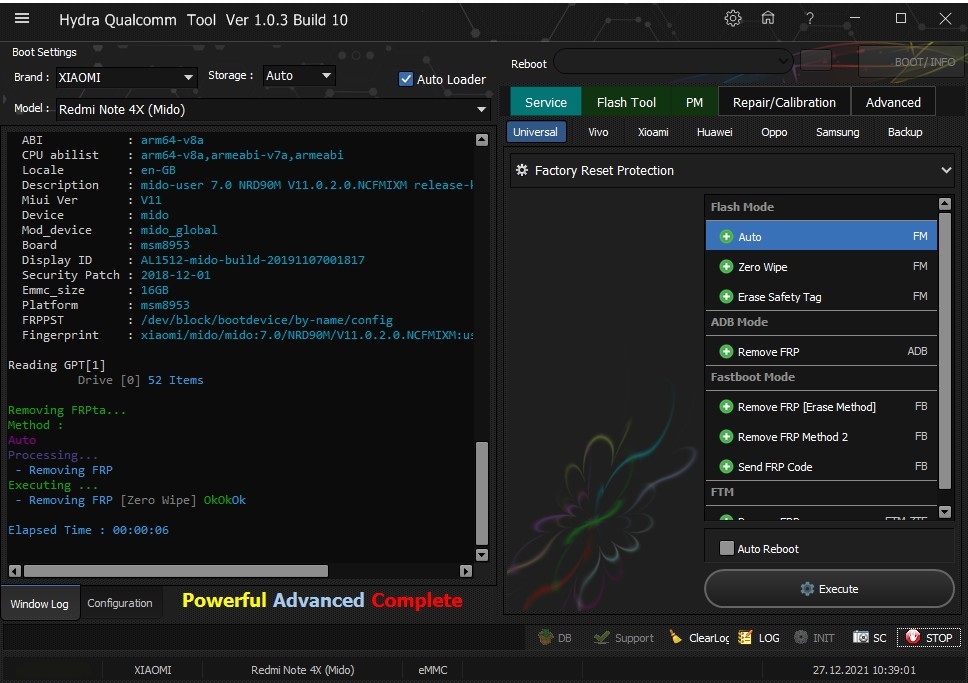 Quote:
| |
 |
| | #2854 (permalink) | |
| No Life Poster       Join Date: Feb 2012 Age: 39
Posts: 1,395
Member: 1724862 Status: Offline Thanks Meter: 448 | Redmi 6A (cactus) Bootloader Unlock With by Hydra Redmi 6A (cactus) Bootloader Unlock With by Hydra 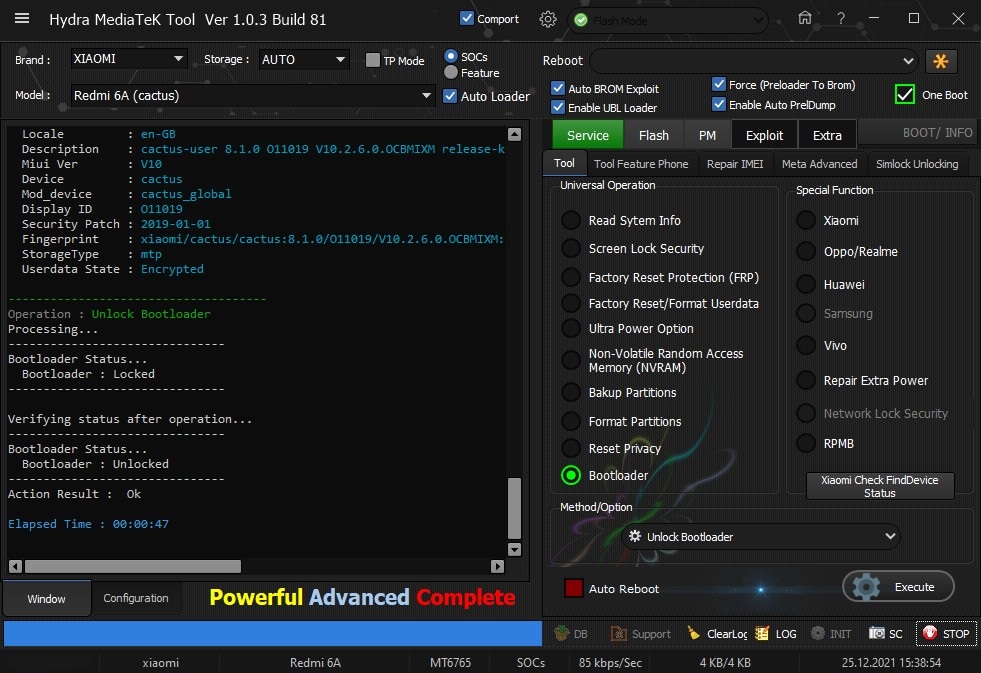 Quote:
| |
 |
| | #2855 (permalink) | |
| No Life Poster       Join Date: Feb 2012 Age: 39
Posts: 1,395
Member: 1724862 Status: Offline Thanks Meter: 448 | Oppo F1s Plus Read Screen Security One Click With by Hydra Oppo F1s Plus Read Screen Security One Click With by Hydra 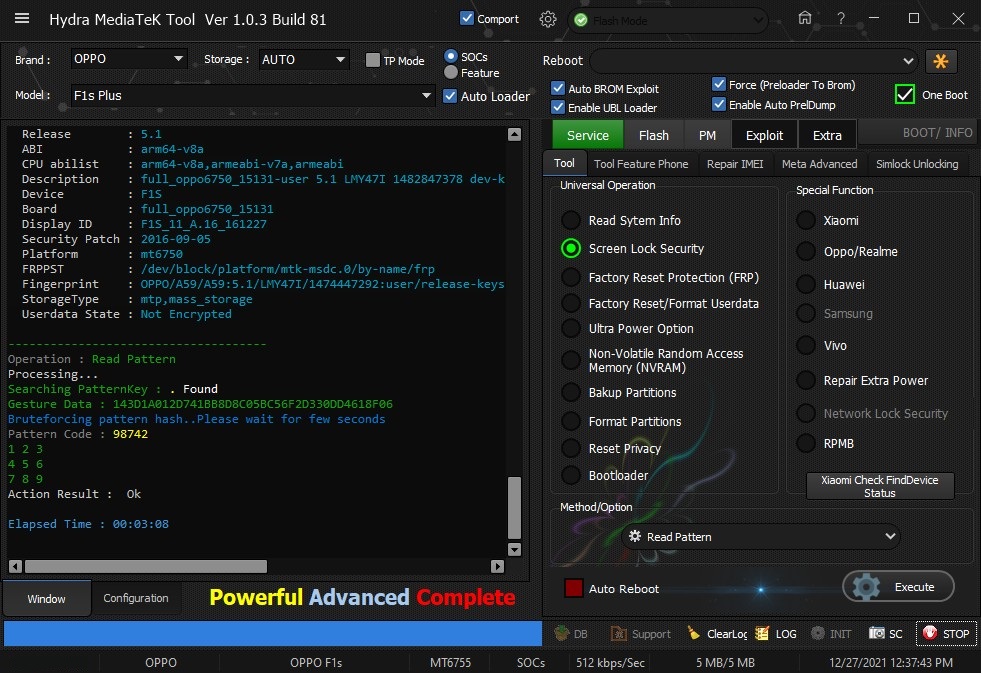 Quote:
| |
 |
| | #2856 (permalink) |
| No Life Poster       Join Date: Jan 2013 Location: gsmhosting Age: 29
Posts: 1,148
Member: 1876736 Status: Offline Thanks Meter: 735 | xiaomi note 8 unlock bootloader 1 click with hydra Code:
XiaomiSpecial_OneClickUBL
PreOperation Configuration
Brand : XIAOMI Model : Redmi Note 8 (ginkgo) Storage : Auto
Loader: 0010A0E100720000_1bebe3863a6781db_76196dc8_XIAOMI.fhprg
Port : Auto
Searching for Qualcomm 9008 Device...Found
FriendlyName :Qualcomm HS-USB QDLoader 9008 (COM5)
SymbolicName :\??\USB#VID_05C6&PID_9008#5&15c311e1&0&9#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :08/02/2017,2.1.2.7
Getting device info......
Serial No.: 0x1BAADAC5
HW_ID : 0010A0E100720000
MSM ID : 0x0010A0E1, SM6125-Qualcomm Snapdragon 665
MODEL_ID : 0x0000
OEM_ID : 0x0072 - XIAOMI
PBL Ver : 00000000
PK HASH : 1bebe3863a6781db4b01086063007334de9e5ca14971c7c4f4358ec9d79cda46
Firehose Loader[0010A0E100720000_1bebe3863a6781db_76196dc8_XIAOMI.fhprg]
--------------------------------------------------
Header Type : New
TargetMSM :
Tag :
Version : 6
Code_size : 816
Signature_size : 256
fhVendor : XIAOMI
HW_ID : 0010A0E100720000
Vendor : XIAOMI
OEM_ID : 0072
MODEL_ID : 0000
SW_ID : 00000003
APP_ID : 00000000
pk_hash : 1bebe3863a6781db4b01086063007334de9e5ca14971c7c4f4358ec9d79cda4692ce5e948c6fd409408f4c919fcadfe3
OEM_VERSION : cibuild
IMAGE_VARIANT : NicobarPkgLAA
QC_VERSION : BOOT.XF.4.0-00149-NICOBARLAZ-1
--------------------------------------------------
SaharaBoot... Ok
Sending ..............................Ok
Connecting to Firehose...
Ping..................... Ok
Configuration.........
Identifying Chip....
Ok
Chip Configuration :
MemoryName : eMMC
MaxPayloadSizeToTargetInBytes : 16384
MaxPayloadSizeToTargetInBytesSupported : 16384
MaxPayloadSizeFromTargetInBytes :
MaxXMLSizeInBytes : 4096
TargetName :
Version : 1
DateTime : Jul 3 2019 - 22:23:56
*** STORAGE DEVICE INFO ***
Memory Type : eMMC
Block Size in Bytes : 512
Page Size : 512
Manufacturer ID : 19
Serial Number : 399840368
Firmware Version : 4
Product Name : S0J9K9
Physical Partitions : 4
Total Logical Blocks:
Drive [0] 244285440[116.484 GB]
Drive [1] 8192[4 MB]
Drive [2] 8192[4 MB]
Drive [3] 32768[16 MB]
Protocol : Universal
Running : Ok
Reading GPT[4]
Drive [0] 88 Items
Drive [1] 0 Items
Drive [2] 0 Items
Drive [3]
Phone Information......
Brand : xiaomi
Vendor : Xiaomi
Model : Redmi Note 8
ID : PKQ1.190616.001
SDK : 28
Release : 9
ABI : arm64-v8a
CPU abilist : arm64-v8a,armeabi-v7a,armeabi
Locale : en-GB
Description : ginkgo-user 9 PKQ1.190616.001 V11.0.12.0.PCOMIXM release-keys
Miui Ver : V11
Device : ginkgo
Mod_device : ginkgo_global
Display ID : PKQ1.190616.001
Security Patch : 2020-11-01
Fingerprint : xiaomi/ginkgo/ginkgo:9/PKQ1.190616.001/V11.0.12.0.PCOMIXM:user/release-keys
Preparing Patching......
- patching... [1]
- patching... [2]
Action Result : Ok
Rebooting Phone.... Ok
Searching Device By Fastboot
Device Found...
Searching Device By Fastboot
Device Found...
Reading Information...getvar:version FAILED (remote: GetVar Variable Not found)
Product : laurel_sprout
version : getvar:version FAILED (remote: GetVar Variable Not found)
Secure : yes
Device Info:
Verity mode: true
Device unlocked: false
Device critical unlocked: false
Charger screen enabled: false
OKAY [ 0.001s]
Finished. Total time: 0.001s
Searching Device By Fastboot
Device Found...
Searching Device By Fastboot
Device Found...
Reading Information...getvar:version FAILED (remote: GetVar Variable Not found)
Product : laurel_sprout
version : getvar:version FAILED (remote: GetVar Variable Not found)
Secure : yes
Device Info:
Verity mode: true
Device unlocked: true
Device critical unlocked: true
Charger screen enabled: false
OKAY [ 0.001s]
Finished. Total time: 0.001s
Elapsed Time : 00:04:32 |
 |
| | #2857 (permalink) | |
| No Life Poster       Join Date: Feb 2012 Age: 39
Posts: 1,395
Member: 1724862 Status: Offline Thanks Meter: 448 | Redmi S2 (ysl) Edl Frp Remove With by Hydra Redmi S2 (ysl) Edl Frp Remove With by Hydra 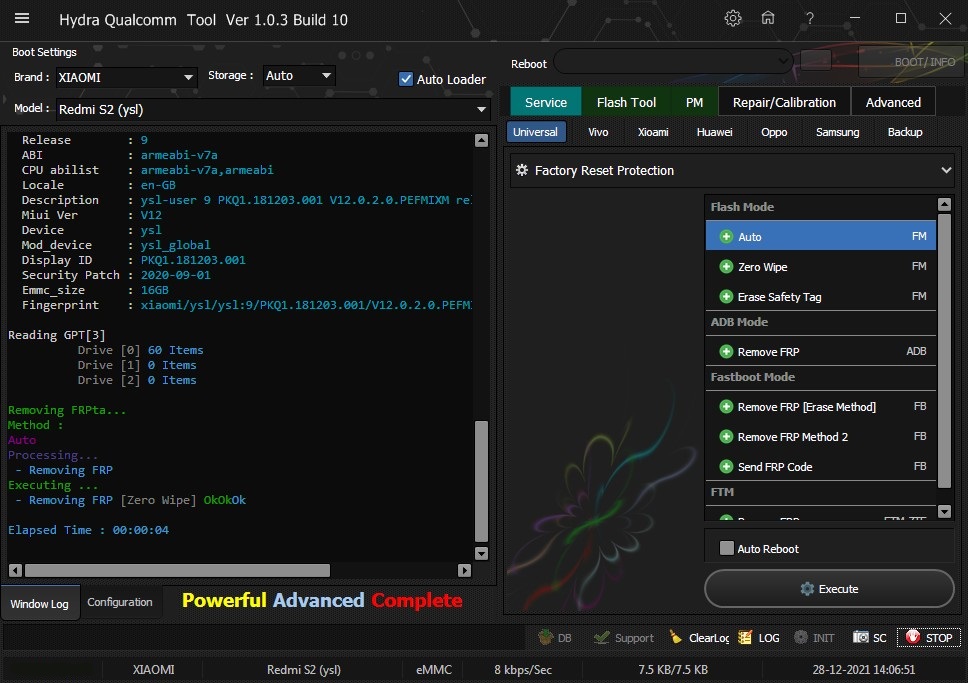 Quote:
| |
 |
| | #2858 (permalink) | |
| No Life Poster       Join Date: Feb 2012 Age: 39
Posts: 1,395
Member: 1724862 Status: Offline Thanks Meter: 448 | Oppo A59st Read Screen Security done With by Hydra Oppo A59st Read Screen Security done With by Hydra 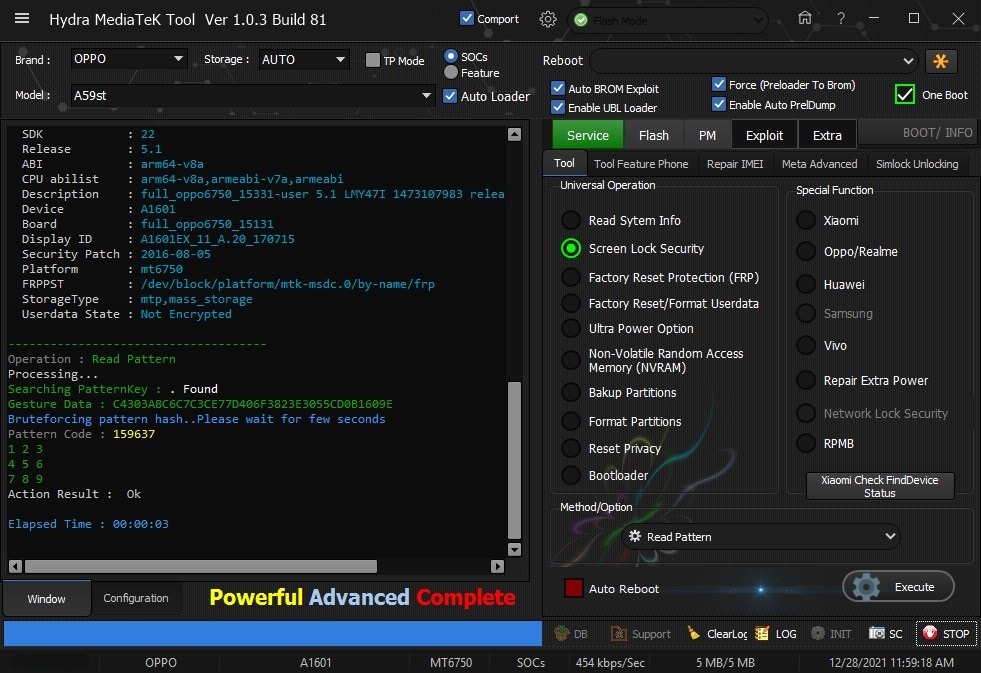 Quote:
| |
 |
| | #2859 (permalink) | |
| No Life Poster       Join Date: Feb 2012 Age: 39
Posts: 1,395
Member: 1724862 Status: Offline Thanks Meter: 448 | SM-A107M (A10s) Bootloader Unlock With by Hydra SM-A107M (A10s) Bootloader Unlock With by Hydra 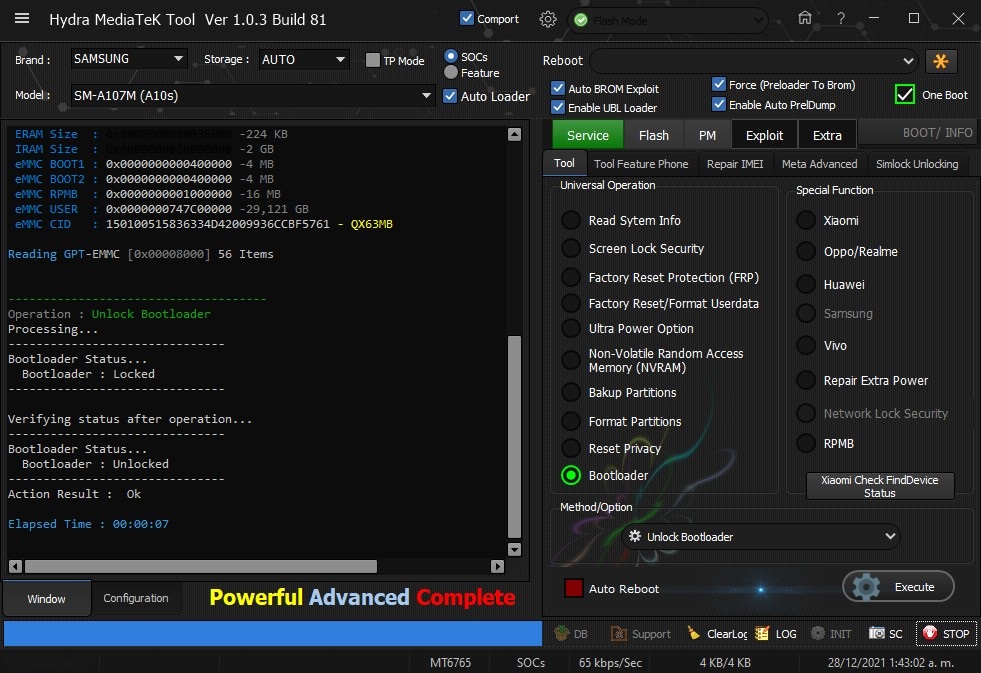 Quote:
| |
 |
| | #2860 (permalink) |
| No Life Poster       Join Date: Jan 2013 Location: gsmhosting Age: 29
Posts: 1,148
Member: 1876736 Status: Offline Thanks Meter: 735 | spd gfive hard reset on diag mode Code: Port : [Auto] Scanning...COM4 Opening Port...(COM4)Ok ------------------------------------------ Factory Reset/Format Userdata... ------------------------------------------ Executing... Factory Reset Action Result..Ok Elapsed Time : 00:00:01 |
 |
| | #2861 (permalink) | |
| No Life Poster       Join Date: Feb 2012 Age: 39
Posts: 1,395
Member: 1724862 Status: Offline Thanks Meter: 448 | SM-A315G (A31) Bootloader Unlock One Click With by Hydra SM-A315G (A31) Bootloader Unlock One Click With by Hydra 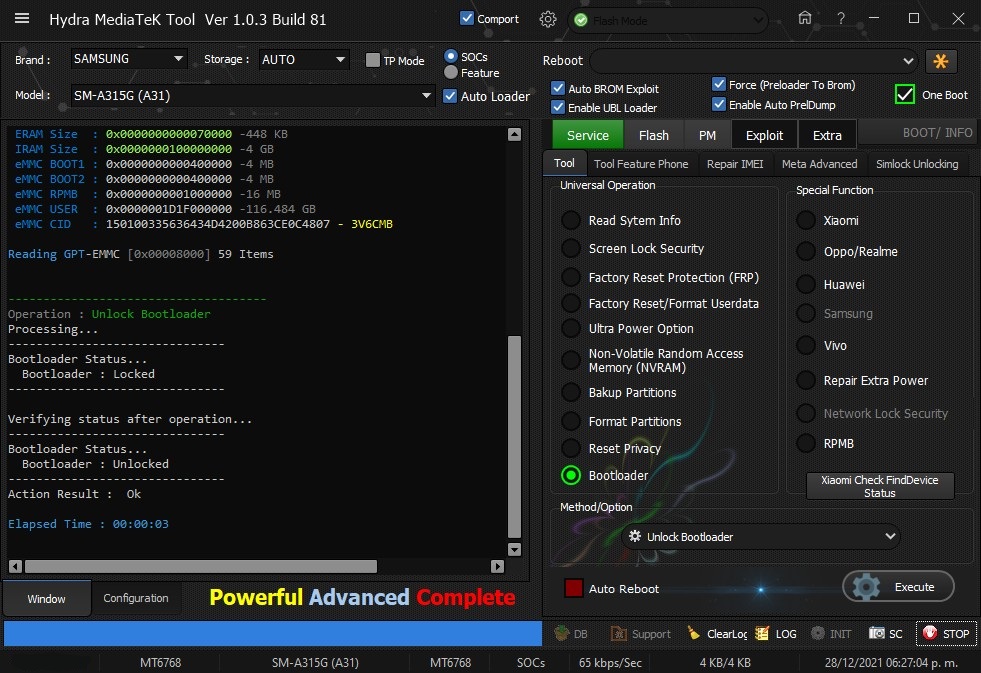 Quote:
| |
 |
| | #2862 (permalink) | |
| No Life Poster       Join Date: Feb 2012 Age: 39
Posts: 1,395
Member: 1724862 Status: Offline Thanks Meter: 448 | Redmi Note 8 (ginkgo) Edl Format Userdata & Frp Remove With by Hydra Redmi Note 8 (ginkgo) Edl Format Userdata & Frp Remove With by Hydra  Quote:
| |
 |
| | #2863 (permalink) | |
| No Life Poster       Join Date: Feb 2012 Age: 39
Posts: 1,395
Member: 1724862 Status: Offline Thanks Meter: 448 | Realme 7 (RMX2151) Remove Realme ID One Clıck With by Hydra Realme 7 (RMX2151) Remove Realme ID One Clıck With by Hydra 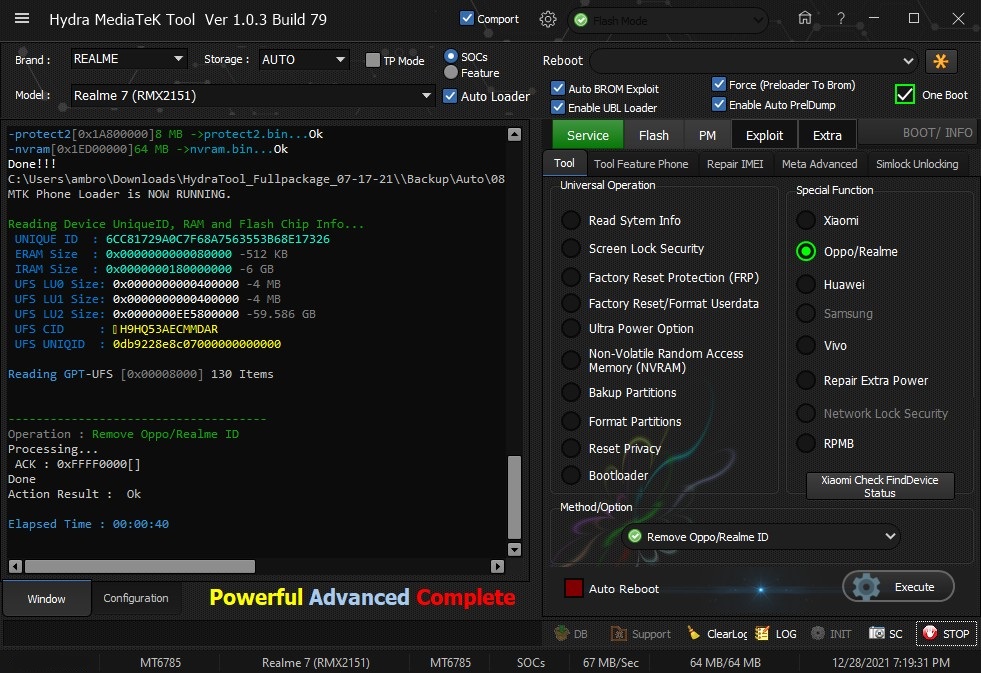 Quote:
| |
 |
| | #2864 (permalink) | |
| No Life Poster       Join Date: Feb 2012 Age: 39
Posts: 1,395
Member: 1724862 Status: Offline Thanks Meter: 448 | Redmi 4A (Rolex) Edl Frp Remove done by Hydra Redmi 4A (Rolex) Edl Frp Remove done by Hydra 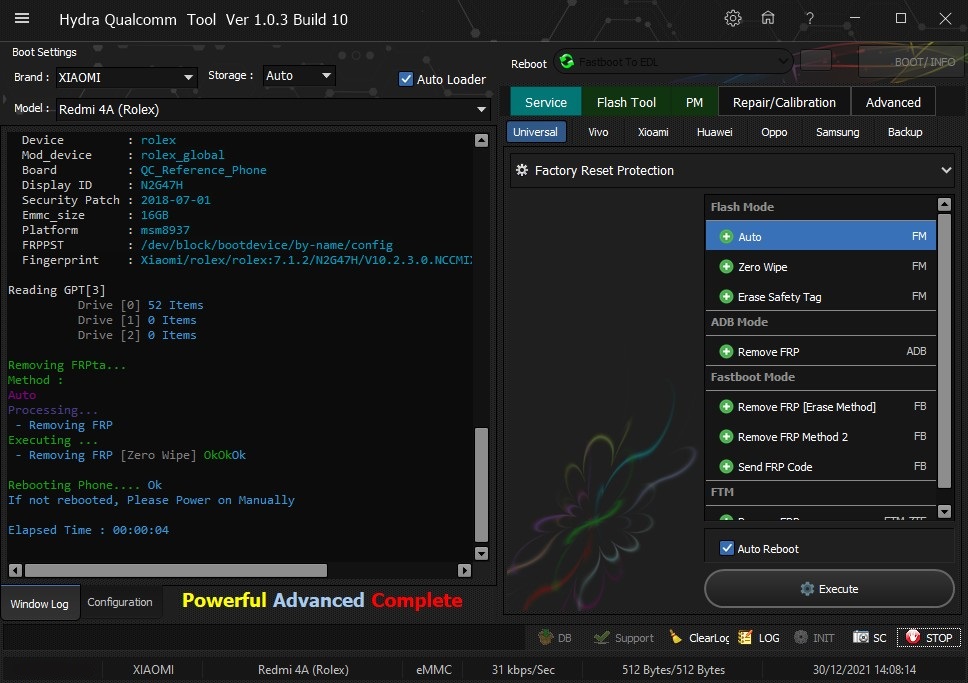 Quote:
| |
 |
| | #2865 (permalink) | |
| No Life Poster       Join Date: Feb 2012 Age: 39
Posts: 1,395
Member: 1724862 Status: Offline Thanks Meter: 448 | MED-LX9 (Y6P 2020) Remove Huawei Account done by Hydra MED-LX9 (Y6P 2020) Remove Huawei Account done by Hydra 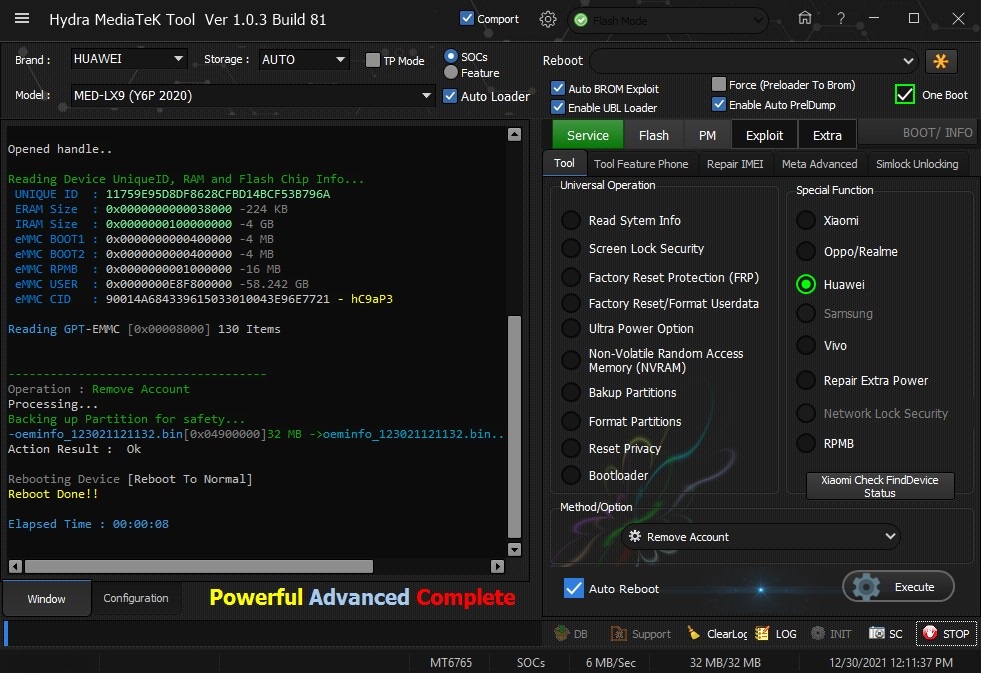 Quote:
| |
 |
 |
| Bookmarks |
| |
|
|