



  |
 |
|
Welcome to the GSM-Forum forums. You are currently viewing our boards as a guest which gives you limited access to view most discussions and access our other features. Only registered members may post questions, contact other members or search our database of over 8 million posts. Registration is fast, simple and absolutely free so please - Click to REGISTER! If you have any problems with the registration process or your account login, please contact contact us . |
| |||||||
| Register | FAQ | Donate | Forum Rules | Root any Device | ★iPhone Unlock★ | ★ Direct Codes ★ | Direct Unlock Source |
 |
| | LinkBack | Thread Tools | Display Modes |
| | #1381 (permalink) |
| Product Manager      Join Date: Aug 2018 Location: Ukraine / Harkov
Posts: 1,986
Member: 2857401 Status: Offline Thanks Meter: 6,861 | Redmi Note 8 Pro IMEI Repair Bootloader Locked by Hydra Dongle |
 |
| The Following 3 Users Say Thank You to Hydra Tool For This Useful Post: |
| | #1382 (permalink) | |
| Product Manager      Join Date: Apr 2008 Location: Whitehole throught Blackhole!
Posts: 9,582
Member: 747989 Status: Offline Sonork: 100.1593052 Thanks Meter: 8,623 | Xiaomi Redmi Note 6 Pro safe format user data successfully done by Hydra Tool Xiaomi Redmi Note 6 Pro safe format user data successfully done by Hydra Tool Screen Short:  Logs: Quote:
Dipendra Pathak | |
 |
| The Following User Says Thank You to Dipendra Pathak For This Useful Post: |
| | #1383 (permalink) | |
| Product Manager      Join Date: Apr 2008 Location: Whitehole throught Blackhole!
Posts: 9,582
Member: 747989 Status: Offline Sonork: 100.1593052 Thanks Meter: 8,623 | Xiaomi Redmi Mi 8 Lite Partly flashed is done by Hydra Tool Xiaomi Redmi Mi 8 Lite Partly flashed is done by Hydra Tool Screen Short:  Logs: Quote:
Dipendra Pathak | |
 |
| The Following User Says Thank You to Dipendra Pathak For This Useful Post: |
| | #1384 (permalink) | |
| Product Manager      Join Date: Apr 2008 Location: Whitehole throught Blackhole!
Posts: 9,582
Member: 747989 Status: Offline Sonork: 100.1593052 Thanks Meter: 8,623 | MTK MT6575 Safe format successfully with DA 6765_SWSEC.bin file by Hydra Tool MTK MT6575 Safe format successfully with DA 6765_SWSEC.bin file by Hydra Tool Screen Short:  Logs: Quote:
Dipendra Pathak | |
 |
| The Following User Says Thank You to Dipendra Pathak For This Useful Post: |
| | #1386 (permalink) | |
| Product Manager      Join Date: Apr 2008 Location: Whitehole throught Blackhole!
Posts: 9,582
Member: 747989 Status: Offline Sonork: 100.1593052 Thanks Meter: 8,623 | Xiaomi Redmi Note 9 (merlin) Remove MI Account and FRP Successfully Removed By Hydra Xiaomi Redmi Note 9 (merlin) Remove MI Account and FRP Successfully Removed By Hydra Screen Short:  Logs: Quote:
Dipendra Pathak | |
 |
| | #1387 (permalink) | |
| Product Manager      Join Date: Apr 2008 Location: Whitehole throught Blackhole!
Posts: 9,582
Member: 747989 Status: Offline Sonork: 100.1593052 Thanks Meter: 8,623 | Huawei DRA-LX5 (Y5 Light) Zero Wipe FRP partition successfully done by Hydra Tool Huawei DRA-LX5 (Y5 Light) Zero Wipe FRP partition successfully done by Hydra Tool Screen Short:  Logs: Quote:
Dipendra Pathak | |
 |
| | #1388 (permalink) | |
| Product Manager      Join Date: Apr 2008 Location: Whitehole throught Blackhole!
Posts: 9,582
Member: 747989 Status: Offline Sonork: 100.1593052 Thanks Meter: 8,623 | Ausu X00BD Zero Wipe FRP successfully Done by Hydra Tool Ausu X00BD Zero Wipe FRP successfully Done by Hydra Tool Screen Short:  Logs: Quote:
Dipendra Pathak | |
 |
| | #1389 (permalink) | |
| Product Manager      Join Date: Apr 2008 Location: Whitehole throught Blackhole!
Posts: 9,582
Member: 747989 Status: Offline Sonork: 100.1593052 Thanks Meter: 8,623 | Oppo A37m Fixed from Dead by Hydra Tool Oppo A37m Fixed from Dead by Hydra Tool Screen Short:  Logs: Quote:
Dipendra Pathak | |
 |
| | #1390 (permalink) | |
| Product Manager      Join Date: Apr 2008 Location: Whitehole throught Blackhole!
Posts: 9,582
Member: 747989 Status: Offline Sonork: 100.1593052 Thanks Meter: 8,623 | Vivo Y71 (V1731B) Forced Erased to remove FRP successfully done by Hydra Tool Vivo Y71 (V1731B) Forced Erased to remove FRP successfully done by Hydra Tool Screen Short:  Logs: Quote:
Dipendra Pathak | |
 |
| | #1391 (permalink) | |
| Product Manager      Join Date: Apr 2008 Location: Whitehole throught Blackhole!
Posts: 9,582
Member: 747989 Status: Offline Sonork: 100.1593052 Thanks Meter: 8,623 | Cat S30 Zero FRP successfully removed by Hydra Tool Cat S30 Zero FRP successfully removed by Hydra Tool Screen Short:  Logs: Quote:
Dipendra Pathak | |
 |
| | #1392 (permalink) |
| No Life Poster      Join Date: Jan 2020 Location: Algeria
Posts: 814
Member: 2944109 Status: Offline Thanks Meter: 656 | XIAOMI REDMI 8 Removing FRP Done Testpoint  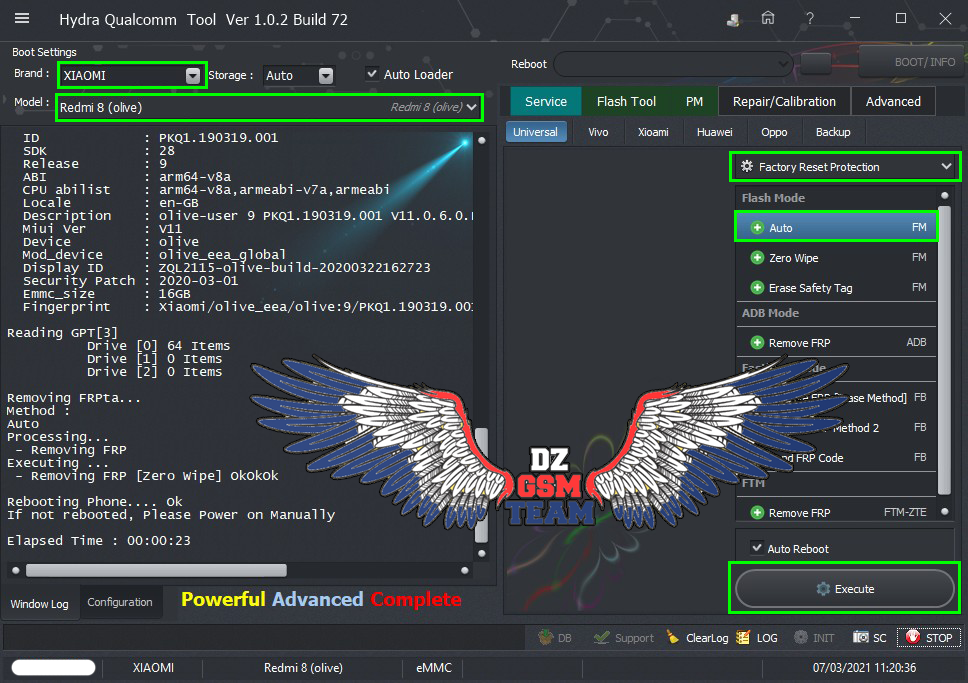 Code: PreOperation Configuration
Brand : XIAOMI Model : Redmi 8 (olive) Storage : Auto
Loader: Xiaomi_Redmi_8_Olive.mbn
Port : Auto
Connection :
Searching for Qualcomm 9008 Device...Found
FriendlyName :
SymbolicName :\??\USB#VID_05C6&PID_9008#6&12e3c9ed&0&1#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :08/02/2017,2.1.2.7
Getting device info......
Serial No.: 0x1141376D
MSM ID : 0x000BF0E1, SDM439-Qualcomm Snapdragon 439
PBL Ver : 00000000
PK HASH : 57158EAF1814D78FD2B3105ECE4DB18A
817A08AC664A5782A925F3FF8403D39A
Firehose Loader[Xiaomi_Redmi_8_Olive.mbn]
SaharaBoot... Ok
Sending .......................Ok
Connecting to Firehose...
Ping... Ok
Configuration.
Xiaomi Authentication needed...
Signature Request -> bob[81efKfdvcrugmyzSW9IDx8TkwRL]
Checking Internet connection....
- Hydra Is Online
Connecting to Hydra Xiaomi Server...
Signature @256bytes Authentication.... Accepted......
Identifying Chip....
Ok
Chip Configuration :
MemoryName : eMMC
MaxPayloadSizeToTargetInBytes : 1048576
MaxPayloadSizeToTargetInBytesSupported : 1048576
MaxPayloadSizeFromTargetInBytes : 4096
MaxXMLSizeInBytes : 4096
TargetName : 8937
Version : 1
*** STORAGE DEVICE INFO ***
Memory Type : eMMC
Block Size in Bytes : 512
Page Size : 512
Manufacturer ID : 19
Serial Number : 333567215
Firmware Version : 4
Product Name : S0J9N8
Physical Partitions : 3
Total Logical Blocks:
Drive [0] 122142720[58,242 GB]
Drive [1] 8192[4 MB]
Drive [2] 8192[4 MB]
Protocol : Universal
Running : Ok
Phone Information......
Brand : Xiaomi
Vendor : Xiaomi
Model : Redmi 8
ID : PKQ1.190319.001
SDK : 28
Release : 9
ABI : arm64-v8a
CPU abilist : arm64-v8a,armeabi-v7a,armeabi
Locale : en-GB
Description : olive-user 9 PKQ1.190319.001 V11.0.6.0.PCNEUXM release-keys
Miui Ver : V11
Device : olive
Mod_device : olive_eea_global
Display ID : ZQL2115-olive-build-20200322162723
Security Patch : 2020-03-01
Emmc_size : 16GB
Fingerprint : Xiaomi/olive_eea/olive:9/PKQ1.190319.001/V11.0.6.0.PCNEUXM:user/release-keys
Reading GPT[3]
Drive [0] 64 Items
Drive [1] 0 Items
Drive [2] 0 Items
Removing FRPta...
Method :
Auto
Processing...
- Removing FRP
Executing ...
- Removing FRP [Zero Wipe] OkOkOk
Rebooting Phone.... Ok
If not rebooted, Please Power on Manually
Elapsed Time : 00:00:23  |
 |
| | #1393 (permalink) |
| No Life Poster      Join Date: Jan 2020 Location: Algeria
Posts: 814
Member: 2944109 Status: Offline Thanks Meter: 656 | Ace Buzz 1 lite Ultra Power Option 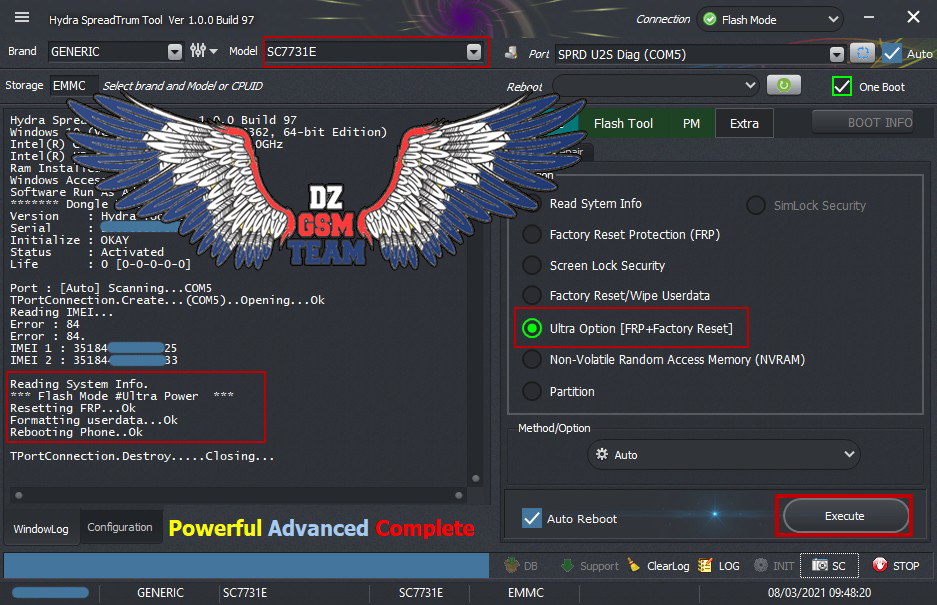 Code: Port : [Auto] Scanning...COM5 TPortConnection.Create...(COM5)..Opening...Ok Reading IMEI... Error : 84 Error : 84. IMEI 1 : 35184XXXXXXXX25 IMEI 2 : 35184XXXXXXXX33 Reading System Info. *** Flash Mode #Ultra Power *** Resetting FRP...Ok Formatting userdata...Ok Rebooting Phone..Ok TPortConnection.Destroy.....Closing... |
 |
| | #1394 (permalink) |
| No Life Poster      Join Date: Jan 2020 Location: Algeria
Posts: 814
Member: 2944109 Status: Offline Thanks Meter: 656 | Condor Plume P6 Pro LTE (PGN528) FRP Remove 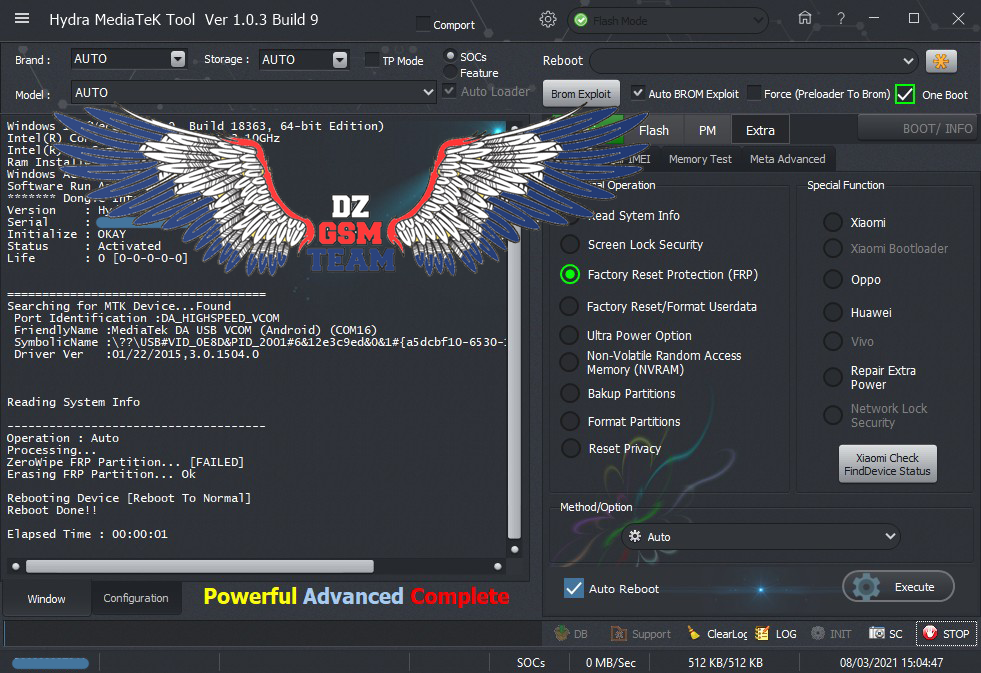 Code: =====================================
Searching for MTK Device...Found
Port Identification :DA_HIGHSPEED_VCOM
FriendlyName :MediaTek DA USB VCOM (Android) (COM16)
SymbolicName :\??\USB#VID_0E8D&PID_2001#6&12e3c9ed&0&1#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :01/22/2015,3.0.1504.0
Reading System Info
-------------------------------------
Operation : Auto
Processing...
ZeroWipe FRP Partition... [FAILED]
Erasing FRP Partition... Ok
Rebooting Device [Reboot To Normal]
Reboot Done!!
Elapsed Time : 00:00:01 |
 |
| | #1395 (permalink) |
| No Life Poster      Join Date: Jan 2020 Location: Algeria
Posts: 814
Member: 2944109 Status: Offline Thanks Meter: 656 | Alcatel Idol 4 LTE (OT-6055K) Safe Format - EMMC Alcatel Idol 4 LTE (OT-6055K) Safe Format - EMMC 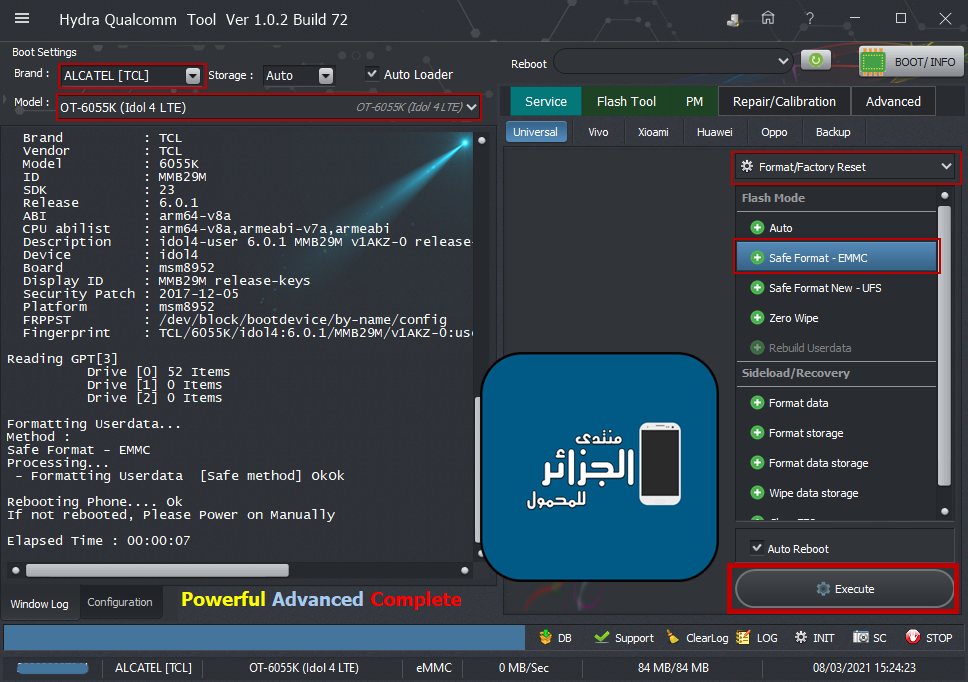 Code: PreOperation Configuration
Brand : ALCATEL [TCL] Model : OT-6055K (Idol 4 LTE) Storage : Auto
Loader: 8952.mbn
Port : Auto
Connection :
Searching for Qualcomm 9008 Device...Found
FriendlyName :Qualcomm HS-USB QDLoader 9008 (COM14)
SymbolicName :\??\USB#VID_05C6&PID_9008#6&12e3c9ed&0&1#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :08/02/2017,2.1.2.7
Getting device info.....
Serial No.: 0x00A48B2C
MSM ID : 0x009720E1, MSM8609-Qualcomm Snapdragon 210
PBL Ver : 00000000
PK HASH : 598FB494403B71C36D1B0DFD0F9E2450
0D767980EF04E5F0A3A94E28DF1FD901
Firehose Loader[8952.mbn]
SaharaBoot... Ok
Sending ..........Ok
Connecting to Firehose...
Ping... Ok
Configuration.......
Identifying Chip....
Ok
Chip Configuration :
MemoryName : eMMC
MaxPayloadSizeToTargetInBytes : 16384
MaxPayloadSizeToTargetInBytesSupported : 16384
MaxPayloadSizeFromTargetInBytes : 4096
MaxXMLSizeInBytes : 4096
TargetName : 8952
Version : 1
Protocol : Feature Phone
Running : Ok
Phone Information.....
Brand : TCL
Vendor : TCL
Model : 6055K
ID : MMB29M
SDK : 23
Release : 6.0.1
ABI : arm64-v8a
CPU abilist : arm64-v8a,armeabi-v7a,armeabi
Description : idol4-user 6.0.1 MMB29M v1AKZ-0 release-keys
Device : idol4
Board : msm8952
Display ID : MMB29M release-keys
Security Patch : 2017-12-05
Platform : msm8952
FRPPST : /dev/block/bootdevice/by-name/config
Fingerprint : TCL/6055K/idol4:6.0.1/MMB29M/v1AKZ-0:user/release-keys
Reading GPT[3]
Drive [0] 52 Items
Drive [1] 0 Items
Drive [2] 0 Items
Formatting Userdata...
Method :
Safe Format - EMMC
Processing...
- Formatting Userdata [Safe method] OkOk
Rebooting Phone.... Ok
If not rebooted, Please Power on Manually
Elapsed Time : 00:00:07 |
 |
 |
| Bookmarks |
| |
|
|