



  |
 |
|
Welcome to the GSM-Forum forums. You are currently viewing our boards as a guest which gives you limited access to view most discussions and access our other features. Only registered members may post questions, contact other members or search our database of over 8 million posts. Registration is fast, simple and absolutely free so please - Click to REGISTER! If you have any problems with the registration process or your account login, please contact contact us . |
| |||||||
| Register | FAQ | Donate | Forum Rules | Root any Device | ★iPhone Unlock★ | ★ Direct Codes ★ | Direct Unlock Source | Search | Today's Posts | Mark Forums Read |
 |
| | LinkBack | Thread Tools | Display Modes |
| | #2611 (permalink) |
| No Life Poster       | Code: SM-A025F
Hydra Qualcomm Tool Ver 1.0.3 Build 1
Windows 10 (Version 10.0, Build 21996, 64-bit Edition)
Intel(R) Core(TM) i3 CPU M 350 @ 2.27GHz
Intel(R) HD Graphics
Ram Installed : 8 GB
Windows Access Right : Admin
Software Run As Admnistrator
******* Dongle Info *******
Version : Hydra Tool v 1.2
Serial : 210300012902
Initialize : OKAY
Status : Activated
Life : 0 [0-0-0-0-0]
PreOperation Configuration
Brand : AUTO Model : AUTO Storage : Auto
Loader: Auto
Port : Auto
Searching for Qualcomm 9008 Device...Found
FriendlyName :Qualcomm HS-USB QDLoader 9008 (COM53)
SymbolicName :\??\USB#VID_05C6&PID_9008#6&61bf49f&0&2#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :08/02/2017,2.1.2.7
Getting device info......
Serial No.: 0xD34D8CFB
HW_ID : 0009A0E100200000
MSM ID : 0x0009A0E1, SDM450-Qualcomm Snapdragon 450
MODEL_ID : 0x0000
OEM_ID : 0x0020 - SAMSUNG
PBL Ver : 00000001
PK HASH : c8c8dd565bf1d8407777a58f8a8e580e00207116e0222c9ab19f3e1f88599034
Firehose Loader[A02S_prog_emmc_firehose_8953_ddr.mbn]
--------------------------------------------------
Header Type : OLD
TargetMSM : 8953
Tag :
Version : 3
Code_size : 320
Signature_size : 256
fhVendor : SAMSUNG CORPORATION
HW_ID : 0009A0E100200000
Vendor : SAMSUNG
OEM_ID : 0020
MODEL_ID : 0000
SW_ID : 0000000100000003
APP_ID :
pk_hash : c8c8dd565bf1d8407777a58f8a8e580e00207116e0222c9ab19f3e1f88599034
OEM_VERSION : SWHE0316
IMAGE_VARIANT : JAADANAZA
QC_VERSION : BOOT.BF.3.3.2-00077
--------------------------------------------------
SaharaBoot... Ok
Sending ......................Ok
Connecting to Firehose...
Ping... Ok
Configuration......
Identifying Chip....
Ok
Chip Configuration :
MemoryName : eMMC
MaxPayloadSizeToTargetInBytes : 1048576
MaxPayloadSizeToTargetInBytesSupported : 1048576
MaxPayloadSizeFromTargetInBytes : 4096
MaxXMLSizeInBytes : 4096
TargetName : 8953
Version : 1
*** STORAGE DEVICE INFO ***
Memory Type : eMMC
Block Size in Bytes : 512
Page Size : 512
Manufacturer ID : 21
Serial Number : 2385078298
Firmware Version : 3
Product Name : GX6BAB
Physical Partitions : 3
Total Logical Blocks:
Drive [0] 61071360[29,121 GB]
Drive [1] 8192[4 MB]
Drive [2] 8192[4 MB]
Protocol : Universal
Running : Ok
Failed to read information from phone.
Reading GPT[3]
Drive [0] 128 Items
Drive [1] 0 Items
Drive [2] 0 Items
Service_SamOptFRPAcount_FM
FRP Remove
- Removing FRP [Zero Wipe] Ok
- Removing FRP [Zero Wipe] OkOk
Elapsed Time : 00:00:08 |
 |
| | #2612 (permalink) |
| No Life Poster       | Samsung A02S (SM-A025F) Remove FRP Code: SM-A025F
Hydra Qualcomm Tool Ver 1.0.3 Build 1
Windows 10 (Version 10.0, Build 21996, 64-bit Edition)
Intel(R) Core(TM) i3 CPU M 350 @ 2.27GHz
Intel(R) HD Graphics
Ram Installed : 8 GB
Windows Access Right : Admin
Software Run As Admnistrator
******* Dongle Info *******
Version : Hydra Tool v 1.2
Serial : 210300012902
Initialize : OKAY
Status : Activated
Life : 0 [0-0-0-0-0]
PreOperation Configuration
Brand : AUTO Model : AUTO Storage : Auto
Loader: Auto
Port : Auto
Searching for Qualcomm 9008 Device...Found
FriendlyName :Qualcomm HS-USB QDLoader 9008 (COM53)
SymbolicName :\??\USB#VID_05C6&PID_9008#6&61bf49f&0&2#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :08/02/2017,2.1.2.7
Getting device info......
Serial No.: 0xD34D8CFB
HW_ID : 0009A0E100200000
MSM ID : 0x0009A0E1, SDM450-Qualcomm Snapdragon 450
MODEL_ID : 0x0000
OEM_ID : 0x0020 - SAMSUNG
PBL Ver : 00000001
PK HASH : c8c8dd565bf1d8407777a58f8a8e580e00207116e0222c9ab19f3e1f88599034
Firehose Loader[A02S_prog_emmc_firehose_8953_ddr.mbn]
--------------------------------------------------
Header Type : OLD
TargetMSM : 8953
Tag :
Version : 3
Code_size : 320
Signature_size : 256
fhVendor : SAMSUNG CORPORATION
HW_ID : 0009A0E100200000
Vendor : SAMSUNG
OEM_ID : 0020
MODEL_ID : 0000
SW_ID : 0000000100000003
APP_ID :
pk_hash : c8c8dd565bf1d8407777a58f8a8e580e00207116e0222c9ab19f3e1f88599034
OEM_VERSION : SWHE0316
IMAGE_VARIANT : JAADANAZA
QC_VERSION : BOOT.BF.3.3.2-00077
--------------------------------------------------
SaharaBoot... Ok
Sending ......................Ok
Connecting to Firehose...
Ping... Ok
Configuration......
Identifying Chip....
Ok
Chip Configuration :
MemoryName : eMMC
MaxPayloadSizeToTargetInBytes : 1048576
MaxPayloadSizeToTargetInBytesSupported : 1048576
MaxPayloadSizeFromTargetInBytes : 4096
MaxXMLSizeInBytes : 4096
TargetName : 8953
Version : 1
*** STORAGE DEVICE INFO ***
Memory Type : eMMC
Block Size in Bytes : 512
Page Size : 512
Manufacturer ID : 21
Serial Number : 2385078298
Firmware Version : 3
Product Name : GX6BAB
Physical Partitions : 3
Total Logical Blocks:
Drive [0] 61071360[29,121 GB]
Drive [1] 8192[4 MB]
Drive [2] 8192[4 MB]
Protocol : Universal
Running : Ok
Failed to read information from phone.
Reading GPT[3]
Drive [0] 128 Items
Drive [1] 0 Items
Drive [2] 0 Items
Service_SamOptFRPAcount_FM
FRP Remove
- Removing FRP [Zero Wipe] Ok
- Removing FRP [Zero Wipe] OkOk
Elapsed Time : 00:00:08 |
 |
| | #2613 (permalink) | |
| No Life Poster       Join Date: May 2011
Posts: 1,322
Member: 1576733 Status: Offline Thanks Meter: 622 | Redmi Note 8 Pro (begonia) Unlock Bootloader With by Hydra Redmi Note 8 Pro (begonia) Unlock Bootloader With by Hydra  Quote:
| |
 |
| | #2614 (permalink) | |
| No Life Poster       Join Date: May 2011
Posts: 1,322
Member: 1576733 Status: Offline Thanks Meter: 622 | Poco M3 Brick Solution -Edl Flashıng By hydra Poco M3 Brick Solution -Edl Flashıng by Hydra  Quote:
| |
 |
| | #2615 (permalink) | |
| No Life Poster       Join Date: May 2011
Posts: 1,322
Member: 1576733 Status: Offline Thanks Meter: 622 | Redmi S2 (ysl) Edl Frp Remove With by Hydra Redmi S2 (ysl) Edl Frp Remove With by Hydra  Quote:
| |
 |
| | #2616 (permalink) | |
| No Life Poster       Join Date: May 2011
Posts: 1,322
Member: 1576733 Status: Offline Thanks Meter: 622 | Redmi 7A (Pine) Edl Flash With by Hydra Redmi 7A (Pine) Edl Flash With by Hydra  Quote:
| |
 |
| | #2617 (permalink) | |
| No Life Poster       Join Date: May 2011
Posts: 1,322
Member: 1576733 Status: Offline Thanks Meter: 622 | Huawei Y7 2019 (DUB-LX1) Edl Flash With by Hydra Huawei Y7 2019 (DUB-LX1) Edl Flash With by Hydra  Quote:
| |
 |
| | #2618 (permalink) | |
| No Life Poster       Join Date: May 2011
Posts: 1,322
Member: 1576733 Status: Offline Thanks Meter: 622 | Redmi 9C NFC (angelican) Unlock Bootloader With by Hydra Redmi 9C NFC (angelican) Unlock Bootloader With by Hydra  Quote:
| |
 |
| | #2619 (permalink) |
| No Life Poster      Join Date: Jan 2020 Location: Algeria
Posts: 825
Member: 2944109 Status: Offline Thanks Meter: 666 | Xiaomi Redmi Note 5 (Whyred) Ultra Power Done By HYDRA Xiaomi Redmi Note 5 (Whyred) Ultra Power Done By HYDRA TOOL Removing FRP [Zero Wipe] + Formatting Userdata [Safe Format - eMMc] 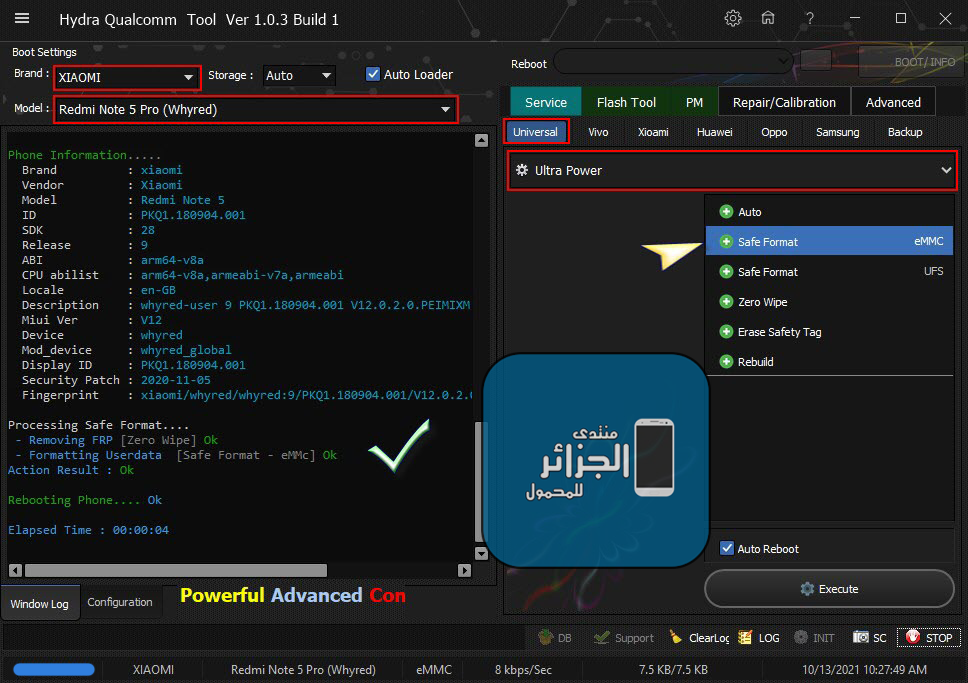 Code: PreOperation Configuration
Brand : XIAOMI Model : Redmi Note 5 Pro (Whyred) Storage : Auto
Loader: mi_2_9.elf
Port : Auto
Searching for Qualcomm 9008 Device...Found
FriendlyName :Qualcomm HS-USB QDLoader 9008 (COM5)
SymbolicName :\??\USB#VID_05C6&PID_9008#6&12e3c9ed&0&1#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :08/31/2015,2.1.2.0
Getting device info..Ok
Device MODE : Firehose
Connecting to Firehose...
Ping...... Ok
Configuration......
Identifying Chip....
Ok
Chip Configuration :
MemoryName : eMMC
MaxPayloadSizeToTargetInBytes : 1048576
MaxPayloadSizeToTargetInBytesSupported : 1048576
MaxPayloadSizeFromTargetInBytes : 4096
MaxXMLSizeInBytes : 4096
TargetName : MSM8996
Version : 1
DateTime : Aug 2 2018 - 22:27:53
*** STORAGE DEVICE INFO ***
Memory Type : eMMC
Block Size in Bytes : 512
Page Size : 512
Manufacturer ID : 21
Serial Number : 2676665404
Firmware Version : 2
Product Name : DD68MB
Physical Partitions : 4
Total Logical Blocks:
Drive [0] 61071360[29.121 GB]
Drive [1] 8192[4 MB]
Drive [2] 8192[4 MB]
Drive [3] 8192[4 MB]
Protocol : Universal
Running : Ok
Reading GPT[4]
Drive [0] 64 Items
Drive [1] 0 Items
Drive [2] 0 Items
Drive [3]
Phone Information.....
Brand : xiaomi
Vendor : Xiaomi
Model : Redmi Note 5
ID : PKQ1.180904.001
SDK : 28
Release : 9
ABI : arm64-v8a
CPU abilist : arm64-v8a,armeabi-v7a,armeabi
Locale : en-GB
Description : whyred-user 9 PKQ1.180904.001 V12.0.2.0.PEIMIXM release-keys
Miui Ver : V12
Device : whyred
Mod_device : whyred_global
Display ID : PKQ1.180904.001
Security Patch : 2020-11-05
Fingerprint : xiaomi/whyred/whyred:9/PKQ1.180904.001/V12.0.2.0.PEIMIXM:user/release-keys
Processing Safe Format....
- Removing FRP [Zero Wipe] Ok
- Formatting Userdata [Safe Format - eMMc] Ok
Action Result : Ok
Rebooting Phone.... Ok
Elapsed Time : 00:00:04 |
 |
| | #2620 (permalink) |
| No Life Poster      Join Date: Jan 2020 Location: Algeria
Posts: 825
Member: 2944109 Status: Offline Thanks Meter: 666 | Stream B1S Safe Format Done Stream B1S Safe Format Done 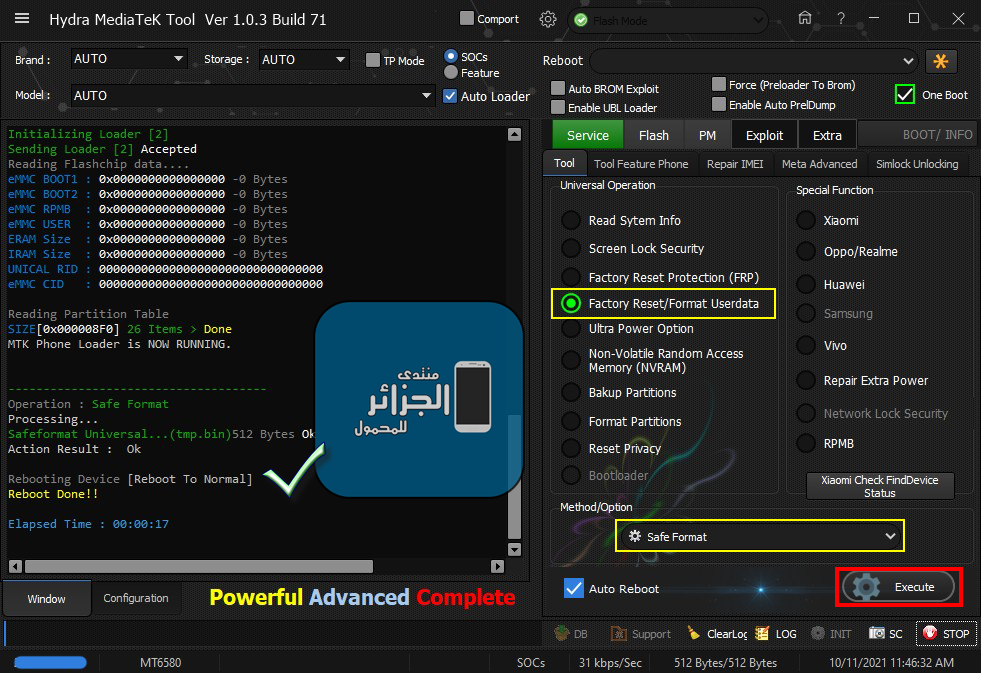 Code: Searching for MTK Device...Found
Port Identification :Flashmode Preloader
FriendlyName :MediaTek PreLoader USB VCOM_V1633 (Android) (COM3)
Device :6&12e3c9ed&0&1
SymbolicName :\??\USB#VID_0E8D&PID_2000#6&12e3c9ed&0&1#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :01/22/2015,3.0.1504.0
Handshaking...Ok
Identifying Hardware ID.....
Reading Device hardware info..
hw code : 6580MT6580 [6580]
hw subcode : 8A00
hw version : CA00
sw version : 0000
Target config : 00
SBC : 00 (False)
SLA : 00 (False)
DAA : 00 (False)
SWJTAG : 00 (False)
EPP : 00 (False)
CERT : 00 (False)
MEMREAD : 00 (False)
MEMWRITE : 00 (False)
CMD_C8 : 00 (False)
FUSEID : 02100040
FUSEID : 02100040
SECURE VERSION : 00
BL VERSION : 01
Preparing Download Agent..
DA : 6580.bin
Agent: MTK_DOWNLOAD_AGENT -HYDRA
Ver : MTK_AllInOne_DA_v3.3001.2020-11-03.22:07_536568
Init : Loader [1]
Sending : Accepted
Identifying Protocol...
Protocol : Old
C4 - eMMC
0007
0000000000000000000000000000
PRMMCCID : 700100543232373038010F1209FF9537
Init Configuration
Running DA 4.2 on BBID : 0x00 Ok
Initializing Loader [2]
Sending Loader [2] Accepted
Reading Flashchip data....
eMMC BOOT1 : 0x0000000000000000 -0 Bytes
eMMC BOOT2 : 0x0000000000000000 -0 Bytes
eMMC RPMB : 0x0000000000000000 -0 Bytes
eMMC USER : 0x0000000000000000 -0 Bytes
ERAM Size : 0x0000000000000000 -0 Bytes
IRAM Size : 0x0000000000000000 -0 Bytes
UNICAL RID : 00000000000000000000000000000000
eMMC CID : 00000000000000000000000000000000
Reading Partition Table
SIZE[0x000008F0] 26 Items > Done
MTK Phone Loader is NOW RUNNING.
-------------------------------------
Operation : Safe Format
Processing...
Safeformat Universal...(tmp.bin)512 Bytes Ok
Action Result : Ok
Rebooting Device [Reboot To Normal]
Reboot Done!!
Elapsed Time : 00:00:17 |
 |
| | #2622 (permalink) | |
| No Life Poster       Join Date: May 2011
Posts: 1,322
Member: 1576733 Status: Offline Thanks Meter: 622 | Redmi 9T Brick Solution-Edl Flash With by Hydra Redmi 9T Brick Solution-Edl Flash With by Hydra  Quote:
| |
 |
| | #2623 (permalink) | |
| No Life Poster       Join Date: May 2011
Posts: 1,322
Member: 1576733 Status: Offline Thanks Meter: 622 | Redmi 9A (dandelion) Bootloader Unlock With by Hydra Redmi 9A (dandelion) Bootloader Unlock With by Hydra  Quote:
| |
 |
| | #2624 (permalink) | |
| No Life Poster       Join Date: May 2011
Posts: 1,322
Member: 1576733 Status: Offline Thanks Meter: 622 | Huawei Y9A(FRL-L22)Remove Huawei Account With by Hydra Huawei Y9A(FRL-L22)Remove Huawei Account With by Hydra  Quote:
| |
 |
| | #2625 (permalink) | |
| No Life Poster       Join Date: May 2011
Posts: 1,322
Member: 1576733 Status: Offline Thanks Meter: 622 | Y6P 2020 (MED-LX9) Remove Frp With by Hydra Y6P 2020 (MED-LX9) Remove Frp With by Hydra  Quote:
| |
 |
 |
| Bookmarks |
| Thread Tools | |
| Display Modes | |
| |
|
|