



  |
 |
|
Welcome to the GSM-Forum forums. You are currently viewing our boards as a guest which gives you limited access to view most discussions and access our other features. Only registered members may post questions, contact other members or search our database of over 8 million posts. Registration is fast, simple and absolutely free so please - Click to REGISTER! If you have any problems with the registration process or your account login, please contact contact us . |
| |||||||
| Register | FAQ | Donate | Forum Rules | Root any Device | ★iPhone Unlock★ | ★ Direct Codes ★ | Direct Unlock Source |
 |
| | LinkBack | Thread Tools | Display Modes |
| | #2296 (permalink) |
| Product Manager      Join Date: Apr 2008 Location: Whitehole throught Blackhole!
Posts: 9,582
Member: 747989 Status: Offline Sonork: 100.1593052 Thanks Meter: 8,623 | Hisilicon Huawei RNE-Al00 (Maimang 6) Remove Huawei ID successfully done by Hydra Too Hisilicon Huawei RNE-Al00 (Maimang 6) Remove Huawei ID successfully done by Hydra Tool 1. Run Hydra Main Tool. Screen Short:2. Choose "Hisilicon" Tab. 3. Choose "Module" 4. Tick "Auto Boot" 5. Choose "Service" Tab 6. Choose "Factory Reset Protection / Account" from drop down menu. 7. Choose "Huwaei ID" 8. Click on "Execute" 9. Connect the device to the compute with the help of Data Cable. 10. Wait until the operation is completed. BR Dipendra Pathak |
 |
| | #2297 (permalink) |
| Product Manager      Join Date: Apr 2008 Location: Whitehole throught Blackhole!
Posts: 9,582
Member: 747989 Status: Offline Sonork: 100.1593052 Thanks Meter: 8,623 | Hisilicon Huawei RNE-L22 (NOVA 2i) FRP successfully removed Hydra Main Tool Hisilicon Huawei RNE-L22 (NOVA 2i) FRP successfully removed Hydra Main Tool 1. Run Hydra Main Tool. Screen Short:2. Choose "Hisilicon" Tab. 3. Choose "Module" 4. Tick "Auto Boot" 5. Choose "Service" Tab 6. Choose "Factory Reset Protection / Account" from drop down menu. 7. Choose "Remove FRP" 8. Click on "Execute" 9. Connect the device to the compute with the help of Data Cable. 10. Wait until the operation is completed. BR Dipendra Pathak |
 |
| | #2298 (permalink) |
| Product Manager      Join Date: Apr 2008 Location: Whitehole throught Blackhole!
Posts: 9,582
Member: 747989 Status: Offline Sonork: 100.1593052 Thanks Meter: 8,623 | Huawei AMN-LX9 (Y5 2019) Both IMEI Repair Successfully done by Hydra Tool Huawei AMN-LX9 (Y5 2019) Both IMEI Repair Successfully done by Hydra Tool 1. Run Hydra MTK module. 2. Choose Brand and Module 3. Tick "Auto Broom Exploit" 4. Go to "Service" -->""IMEI" Tab. 5. Tick "IMEI changing is illigal............................". 6. Choose "Huawei Flash Mode" from drop down menu 7. Tick two small box, if you want to repair two IMEI 8. Type the imei written back on your cellphone or battery housing. 9. Tick "Auto Reboot" 10. Click "Execute" 11. connect device to the computer with USB Data cable 12. Wait until the process is completed. Screen Short:  BR Dipendra Pathak |
 |
| | #2299 (permalink) |
| Product Manager      Join Date: Apr 2008 Location: Whitehole throught Blackhole!
Posts: 9,582
Member: 747989 Status: Offline Sonork: 100.1593052 Thanks Meter: 8,623 | Xiaomi Redmi 9A (Dandelion) Mi Account Successfully removed by Hydra Tool Xiaomi Redmi 9A (Dandelion) Mi Account Successfully removed by Hydra Tool 1. Run Hydra MTK Module and Sosc. 2. Choose Brand and Module. 3. Go to "Service"-->"Tool" Tab. 4. Choose "Xiaomi". 5. Click on "Remove Mi Account (Erased Method) + FRP" from drop down menu. 6. Click "Execute" button 7. connect device to the computer with USB Data cable 8. Wait until the process is completed. Screen Short:  BR Dipendra Pathak |
 |
| | #2300 (permalink) |
| Product Manager      Join Date: Apr 2008 Location: Whitehole throught Blackhole!
Posts: 9,582
Member: 747989 Status: Offline Sonork: 100.1593052 Thanks Meter: 8,623 | Xiaomi Redmi 6 (Cereus) formatted selected partition from PM Tab by Hydra Tool Xiaomi Redmi 6 (Cereus) formatted selected partition from PM Tab by Hydra Tool 1. Run Hydra MTK module. 2. Choose Brand and Module. 3. Choose "Auto Broom Exploit" 4. Go to "PM" Tab. 5. Choose "Flash Mode" 6. Click "Partition" and connect device to computer with data cable. 7. Wait until the software shows all partition of cellphone. 8. Choose the partition you want to read, or erase or write. 9. Click on "Erase" or "Write" or "Read" that you need. 10. Wait until the process is completed. Screen Short:  BR Dipendra Pathak |
 |
| | #2301 (permalink) |
| Product Manager      Join Date: Apr 2008 Location: Whitehole throught Blackhole!
Posts: 9,582
Member: 747989 Status: Offline Sonork: 100.1593052 Thanks Meter: 8,623 | Oppo Realme C25 (RMX3191) remove FRP successfully done by Hydra Tool Oppo Realme C25 (RMX3191) remove FRP successfully done by Hydra Tool 1. Run Hydra MTK module. Screen Short:2. Choose Brand and Module 3. Tick "Auto Broom Exploit" 4. Go to "Service" -->"Tool" Tab. 5. Choose MANUAL BOOT Note: If you do not have boot file, you can make it from Hydra "EXPLOIT" Tab using "BROOM (dump Preloader Flash init)" 6. Choose "Factory Reset Protection-FRP" 7. Tick "Format /Erase" 8. Tick "Auto Reboot" 9. Click "Execute" 10. connect device to the computer with USB Data cable 11. Wait until the process is completed.  BR Dipendra Pathak |
 |
| | #2302 (permalink) |
| Product Manager      Join Date: Aug 2018 Location: Ukraine / Harkov
Posts: 1,986
Member: 2857401 Status: Offline Thanks Meter: 6,861 | Vivo Y15 1901 IMEI Repair by Flash Mode Vivo Y15 1901 IMEI Repair by Flash Mode Vivo MTK Repair IMEI in BROM Mode | Without Root | Without Credit | Without Auth |
 |
| The Following User Says Thank You to Hydra Tool For This Useful Post: |
| | #2303 (permalink) |
| Product Manager      Join Date: Apr 2008 Location: Whitehole throught Blackhole!
Posts: 9,582
Member: 747989 Status: Offline Sonork: 100.1593052 Thanks Meter: 8,623 | vivo Y12 1901 repair imei successfully done by Hydra Tool vivo Y12 1901 repair imei successfully done by Hydra Tool 1. Run MTK module 2. Choose Module and Brand "Auto" 3. Go to "Configuration" Tab 4. Untick "Auto Backup" and "Read IMEI" 5. Go to "Service"--> "Tool" 6. Choose "Read System INFO" 7. Click on "BOOT / INFO" 8. Connect Device to the computer using Data Cable. 9. Wait until the Hydra Tool reads all system information. 10. Now, go to "IMEI Repair" Tab 11. Tick "IMEI Changing is illigal........................................" 12. Choose "Vivo FlashMode" from drop down menu. 13. Untick "Auto Reboot" 14. Tick BOTH IMEI boxes 15. Type the correct IMEI from your cellphone or from battery housing. 16. Click on "Repair IMEI" 17. Wait until the process is completed. 18. Now, Tick "Auto Reboot" 19. Click on "Repair IMEI" button. 20. Wait until the process is completed. 21. Done. Video Proof: BR Dipendra Pathak Last edited by Hydra Tool; 08-02-2021 at 11:27. |
 |
| | #2304 (permalink) |
| Product Manager      Join Date: Apr 2008 Location: Whitehole throught Blackhole!
Posts: 9,582
Member: 747989 Status: Offline Sonork: 100.1593052 Thanks Meter: 8,623 | Oppo Reno 3 5G (PDCM00) Unlock Bootloader by Hydra Tool Oppo Reno 3 5G (PDCM00) Unlock Bootloader by Hydra Tool Vodeo Proof: BR Dipendra Pathak Last edited by Hydra Tool; 08-02-2021 at 11:27. |
 |
| | #2305 (permalink) |
| Product Manager      Join Date: Apr 2008 Location: Whitehole throught Blackhole!
Posts: 9,582
Member: 747989 Status: Offline Sonork: 100.1593052 Thanks Meter: 8,623 | Vivo Y15 1901 IMEI Repair by Flash Mode with Manual and Video Vivo Y15 1901 IMEI Repair by Flash Mode with Manual and Video 1. Run MTK module 2. Choose Module and Brand "Auto" 3. Go to "Configuration" Tab 4. Untick "Auto Backup" and "Read IMEI" 5. Go to "Service"--> "Tool" 6. Choose "Read System INFO" 7. Click on "BOOT / INFO" 8. Connect Device to the computer using Data Cable. 9. Wait until the Hydra Tool reads all system information. 10. Now, go to "IMEI Repair" Tab 11. Tick "IMEI Changing is illigal........................................" 12. Choose "Vivo FlashMode" from drop down menu. 13. Untick "Auto Reboot" 14. Tick BOTH IMEI boxes 15. Type the correct IMEI from your cellphone or from battery housing. 16. Click on "Repair IMEI" 17. Wait until the process is completed. 18. Now, Tick "Auto Reboot" 19. Click on "Repair IMEI" button. 20. Wait until the process is completed. 21. Done. Video Proof: BR Dipendra Pathak Last edited by Hydra Tool; 08-02-2021 at 11:27. |
 |
| | #2307 (permalink) |
| No Life Poster      Join Date: Jan 2020 Location: Algeria
Posts: 814
Member: 2944109 Status: Offline Thanks Meter: 656 | Condor C6+ (PGN-508) Read Pattern Condor C6+ (PGN-508) Read Pattern 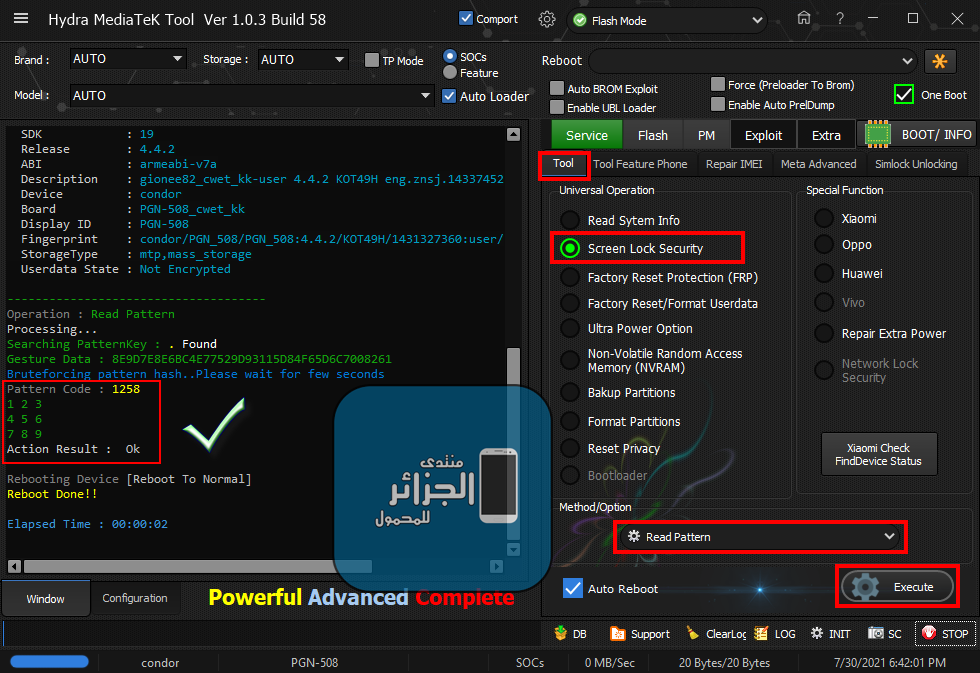 Code: Searching for MTK Device...Found
Port Identification :Flashmode Preloader
FriendlyName :MediaTek PreLoader USB VCOM_V1632 (Android) (COM4)
Device :6&12e3c9ed&0&1
SymbolicName :\??\USB#VID_0E8D&PID_2000#6&12e3c9ed&0&1#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :01/22/2015,3.0.1504.0
Reading System Info
Brand : condor
Vendor : SPA_CONDOR_ELECTORNICS
Model : PGN-508
ID : KOT49H
SDK : 19
Release : 4.4.2
ABI : armeabi-v7a
Description : gionee82_cwet_kk-user 4.4.2 KOT49H eng.znsj.1433745252 release-keys
Device : condor
Board : PGN-508_cwet_kk
Display ID : PGN-508
Fingerprint : condor/PGN_508/PGN_508:4.4.2/KOT49H/1431327360:user/release-keys
StorageType : mtp,mass_storage
Userdata State : Not Encrypted
-------------------------------------
Operation : Read Pattern
Processing...
Searching PatternKey : . Found
Gesture Data : 8E9D7E8E6BC4E77529D93115D84F65D6C7008261
Bruteforcing pattern hash..Please wait for few seconds
Pattern Code : 1258
1 2 3
4 5 6
7 8 9
Action Result : Ok
Rebooting Device [Reboot To Normal]
Reboot Done!!
Elapsed Time : 00:00:02 |
 |
| The Following User Says Thank You to Gsm-Ahmed For This Useful Post: |
| | #2308 (permalink) |
| No Life Poster      Join Date: Jan 2020 Location: Algeria
Posts: 814
Member: 2944109 Status: Offline Thanks Meter: 656 | Samsung Galaxy Grand Prime Pro (SM-J250F) Removing FRP Samsung Galaxy Grand Prime Pro (SM-J250F) Removing FRP 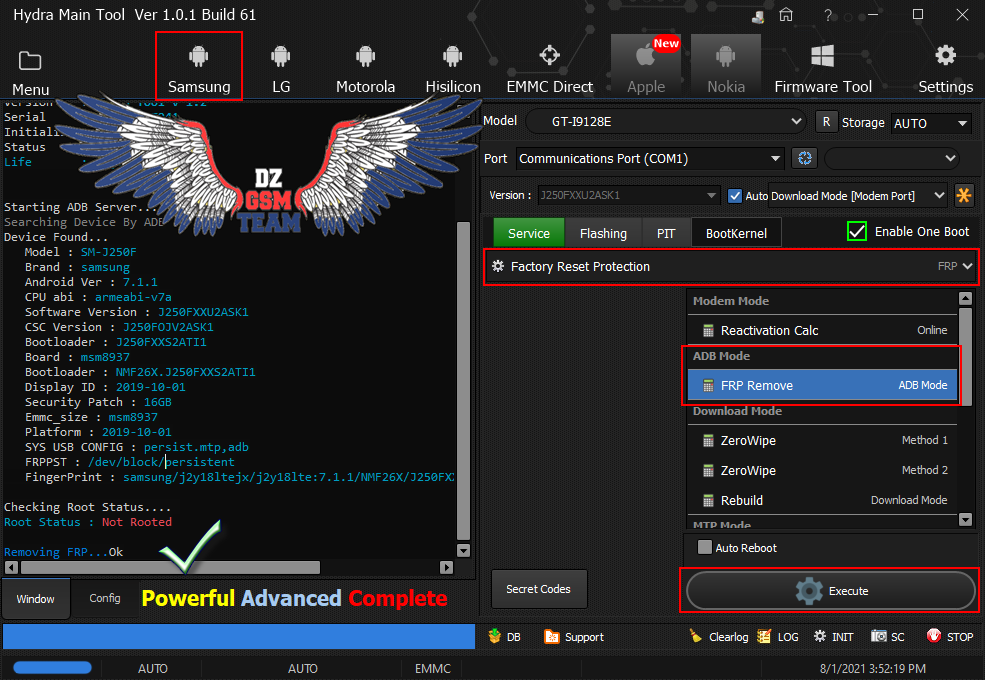 Code: Starting ADB Server.... Searching Device By ADB Device Found... Model : SM-J250F Brand : samsung Android Ver : 7.1.1 CPU abi : armeabi-v7a Software Version : J250FXXU2ASK1 CSC Version : J250FOJV2ASK1 Bootloader : J250FXXS2ATI1 Board : msm8937 Bootloader : NMF26X.J250FXXS2ATI1 Display ID : 2019-10-01 Security Patch : 16GB Emmc_size : msm8937 Platform : 2019-10-01 SYS USB CONFIG : persist.mtp,adb FRPPST : /dev/block/persistent FingerPrint : samsung/j2y18ltejx/j2y18lte:7.1.1/NMF26X/J250FXXS2ATI1:user/release-keys Checking Root Status.... Root Status : Not Rooted Removing FRP...Ok |
 |
| The Following User Says Thank You to Gsm-Ahmed For This Useful Post: |
| | #2309 (permalink) |
| No Life Poster      Join Date: Jan 2020 Location: Algeria
Posts: 814
Member: 2944109 Status: Offline Thanks Meter: 656 | TECNO Spark 6 (KE7) Ultra Power Option TECNO Spark 6 (KE7) Ultra Power Option 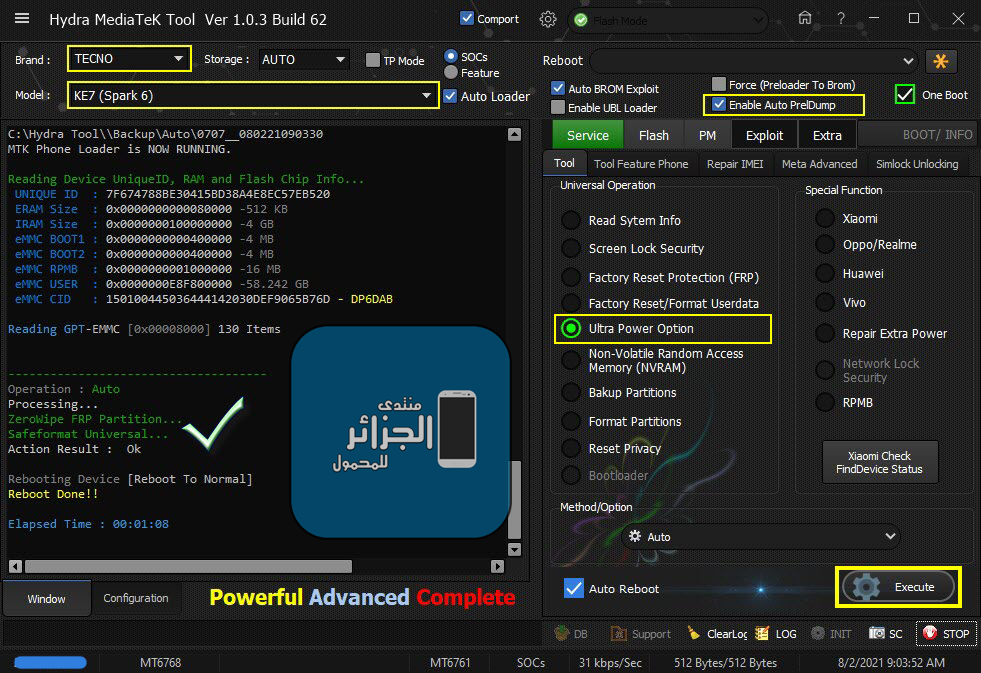 Code: Searching for MTK Device...Found
Port Identification :Flashmode BROM
FriendlyName :MediaTek USB Port_V1632 (COM6)
Device :6&12e3c9ed&0&1
SymbolicName :\??\USB#VID_0E8D&PID_0003#6&12e3c9ed&0&1#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :01/22/2015,3.0.1504.0
Handshaking...Ok
Identifying Hardware ID.....
Reading Device hardware info..
hw code : 0707MT6768 [6768]
hw subcode : 8A00
hw version : CA00
sw version : 0000
Target config : E5
SBC : 01 (True)
SLA : 00 (False)
DAA : 04 (True)
SWJTAG : 04 (True)
EPP : 00 (False)
CERT : 00 (False)
MEMREAD : 20 (True)
MEMWRITE : 40 (True)
CMD_C8 : 80 (True)
Exploiting Device...
Exploit Sent..
Successfully Exploited...
Handshaking...Ok
Identifying Hardware ID.....
Reading Device hardware info..
hw code : 0707MT6768 [6768]
hw subcode : 8A00
hw version : CA00
sw version : 0000
Target config : 00
SBC : 00 (False)
SLA : 00 (False)
DAA : 00 (False)
SWJTAG : 00 (False)
EPP : 00 (False)
CERT : 00 (False)
MEMREAD : 00 (False)
MEMWRITE : 00 (False)
CMD_C8 : 00 (False)
FUSEID : 00000000
SECURE VERSION : 05
BL VERSION : FE
NORMAL BOOT
Preparing Download Agent..
DA : [Not Exist]
Trying Default 6768.bin
Agent: MTK_DOWNLOAD_AGENT -HYDRA
Ver : MTK_AllInOne_DA_v3.3001.2020/03/17.ÉÏÎç10:04_497508
Init : Loader [1]
Sending : Accepted
Identifying Protocol...
Protocol : New
Synchronization...SYNC
Mode : brom
Preloader Initialization...
Parsing preloader_ke7_spark_6.bin
Init : Accepted
Execute Secondary Loader
Init : Loader [2]
Executing : SYNC
Reading Device UniqueID, RAM and Flash Chip Info...
UNIQUE ID : 7F674788BE30415BD38A4E8EC57EB520
ERAM Size : 0x0000000000080000 -512 KB
IRAM Size : 0x0000000100000000 -4 GB
eMMC BOOT1 : 0x0000000000400000 -4 MB
eMMC BOOT2 : 0x0000000000400000 -4 MB
eMMC RPMB : 0x0000000001000000 -16 MB
eMMC USER : 0x0000000E8F800000 -58.242 GB
eMMC CID : 150100445036444142030DEF9065B76D - DP6DAB
DA Speed : high-speed
Reading GPT-EMMC [0x00008000] 130 Items
Autobackup Partitions
-preloader[0x00000000]512 KB ->preloader.bin...Ok
-> Renaming Preloader.... preloader_ke7_h693.bin
Creating Scatter file... C:\Hydra Tool\\Backup\Auto\0707__080221090330\MT6768_Android_scatter.txt
-pgpt[0x00000000]32 KB ->pgpt.bin...Ok
-frp[0x03188000]1024 KB ->frp.bin...Ok
-nvdata[0x08922000]64 MB ->nvdata.bin...Ok
-persist[0x0C922000]48 MB ->persist.bin...Ok
-protect1[0x0F922000]8 MB ->protect1.bin...Ok
-protect2[0x10122000]8 MB ->protect2.bin...Ok
-nvram[0x1E900000]64 MB ->nvram.bin...Ok
Done!!!
C:\Hydra Tool\\Backup\Auto\0707__080221090330
MTK Phone Loader is NOW RUNNING.
Reading Device UniqueID, RAM and Flash Chip Info...
UNIQUE ID : 7F674788BE30415BD38A4E8EC57EB520
ERAM Size : 0x0000000000080000 -512 KB
IRAM Size : 0x0000000100000000 -4 GB
eMMC BOOT1 : 0x0000000000400000 -4 MB
eMMC BOOT2 : 0x0000000000400000 -4 MB
eMMC RPMB : 0x0000000001000000 -16 MB
eMMC USER : 0x0000000E8F800000 -58.242 GB
eMMC CID : 150100445036444142030DEF9065B76D - DP6DAB
Reading GPT-EMMC [0x00008000] 130 Items
-------------------------------------
Operation : Auto
Processing...
ZeroWipe FRP Partition...
Safeformat Universal...
Action Result : Ok
Rebooting Device [Reboot To Normal]
Reboot Done!!
Elapsed Time : 00:01:08 |
 |
| The Following User Says Thank You to Gsm-Ahmed For This Useful Post: |
| | #2310 (permalink) |
| Product Manager      Join Date: Apr 2008 Location: Whitehole throught Blackhole!
Posts: 9,582
Member: 747989 Status: Offline Sonork: 100.1593052 Thanks Meter: 8,623 | Vivo S9 (PD2072E) Unlock Bootloader successfully done by Hydra Dongle Vivo S9 (PD2072E) Unlock Bootloader successfully done by Hydra Dongle VIDEO PROOF: BR Dipendra Pathak |
 |
 |
| Bookmarks |
| |
|
|